Saturday, 9 March 2024
Protect Your Cloud Environments with Data Security Observability
Thursday, 16 February 2023
Evolution towards Full-Stack Observability
Modern Applications are complex
Monitoring to Visibility to Full-Stack Observability
Saturday, 14 May 2022
What is Container Scanning (And Why You Need It)
I want to share my experience using vulnerability scanners and other open-source projects for security. First, we need container scanning to make our app and solution secure and safe. The central concept of container scanning is to scan OS Packages and programming language dependencies. Security scanning helps to detect common vulnerabilities and exposures (CVE). The modern proactive security approach provides integration container scanning in CI/CD pipelines. This approach helps detect and fix vulnerabilities in code, containers, and IaC conf files before release or deployment.
How does it work?
Scanners pull the image from the docker registry and try to analyze each layer. After the first running, scanners will download their vulnerability database. Then each time after running, the community (security specialist, vendors, etc.) identifies, defines, and adds publicly disclosed cybersecurity vulnerabilities to the catalog. We need to consider that sometimes when you run some scanners on your server or laptop, scanners can take some time to update their database.
Usually, scanners and other security tools use multiple resources for their database:
◉ Internal database
◉ National Vulnerability Database (NVD)
◉ Scanners also can be configured to incorporate external data sources (e.g., https://search.maven.org/ )
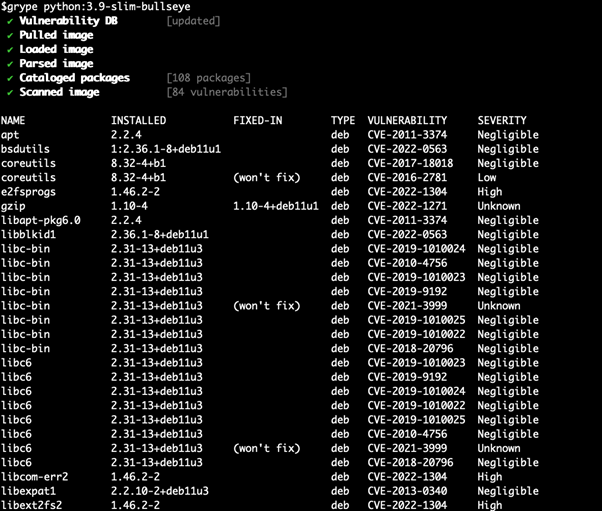
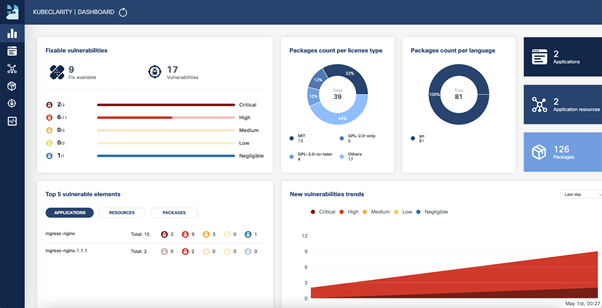
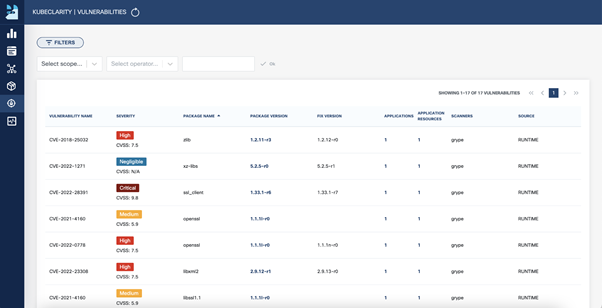
As a result, we see the output with a list of vulnerabilities, name of components or libraries, Vulnerability ID, Severity level (Unknown, Negligible, Low, Medium, High), and Software Bill of Materials (SBOM) format. Using output, we can see or write in a file in which package version vulnerabilities were fixed. This information can help change/update packages or base the image on the secure one.
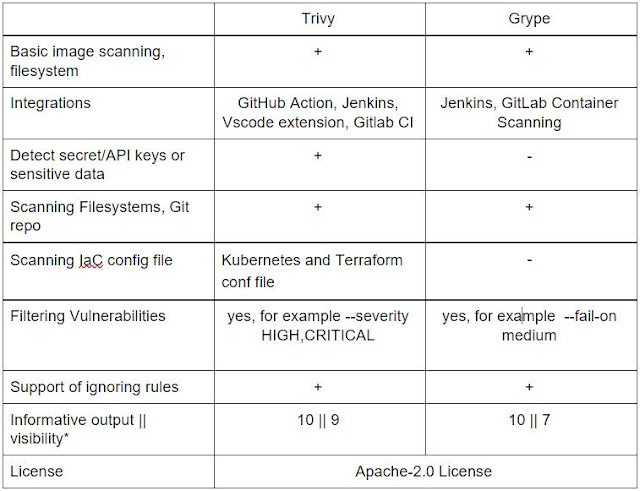
Comparing Trivy and Grype
I chose to compare two different open source vulnerability scanners. Trivy and Grype are comprehensive scanners for vulnerabilities in container images, file systems, and GIT repositories. For the scanning and analytics, I chose the Debian image, as it’s more stable for production (greetings to alpine).