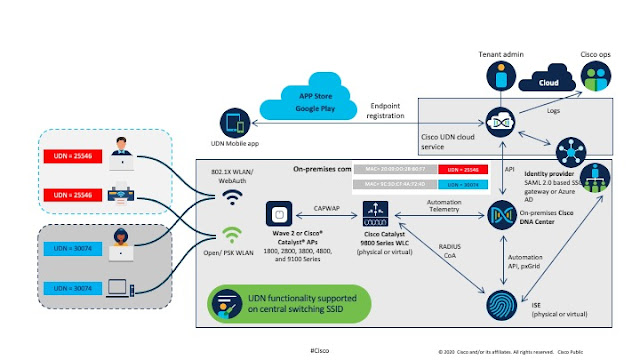
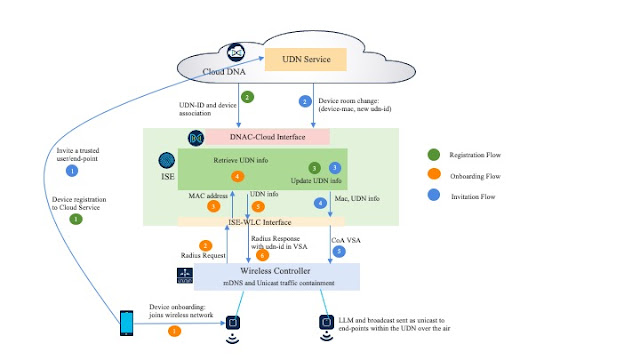
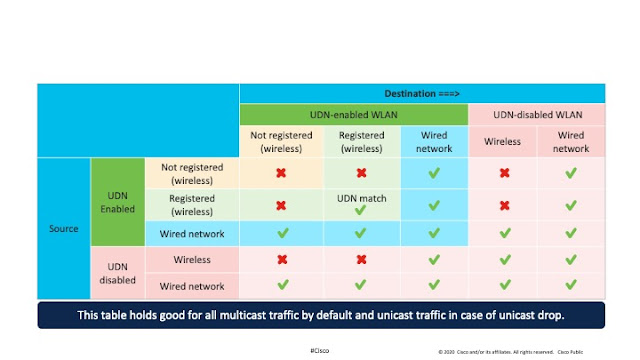
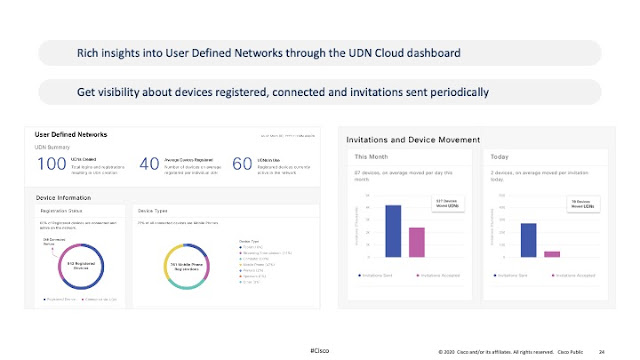
We live in a wireless world. We almost never plug our computers into a network. Our mobile phones and tablets provide constant connectivity. Some of us wear health tracking devices like Apple Watches, Fitbits, and Garmins. These devices count our steps, measure our heart rates, and log the number of hours we sleep. In doing so, health tracking devices create incredible volumes of data we use to monitor our personal health and improve the quality of our lives. When we don’t feel well, we can look back at hours slept and pulse rate to understand the cause and effect of our bodies’ inputs and outputs.
In many ways, our bodies are like machines requiring inputs like food for fueling, sleep for recovery, and exercise for maintaining optimal performance. When we take care of our bodies, we are rewarded with optimal outputs including increased awareness and productivity.
The same is true for machines on the factory floor. They require electricity for fuel and raw materials to manufacture products. Historically, machinists and engineers were the experts in operating their tooling. They learned through years of experience. Over time, sensors connected to the equipment and computers collected data used to monitor and improve visibility into operating characteristics. Sensors measure equipment performance like vibration, current draw, and lubricant temperatures assisted equipment operators in gaining maximum productivity from their equipment.
Initially many of these sensors and computers were wired and tethered. Over time, sensors became wireless and hard-wired computers morphed into wireless laptops, tablets, and mobile devices. And with wireless becoming pervasive, manufacturers gained considerable flexibility to monitor and manage the health of their factory equipment.
The shift to mobility
Previously, we described networks as being wireless. Over-time, we shifted from wireless to mobile and mobility. With mobility, we can drive the business benefits associated with the wireless features.
Building a mobile manufacturing network creates many challenges. The fundamental challenge is to ensure the wireless capabilities are built on a solid foundation. The foundation requires robust security and a common network infrastructure. Historically, the factory network operated independently of the enterprise network. However, today, it’s possible to secure and converge both the factory and enterprise networks with
Cisco’s standard platform.
Once the foundation has been established, the mobile environment must be configured for the three foundational use cases. These use cases enable data, communications, and video capabilities.
Although it sounds obvious, data drives everything. Sensors enable access to data. The simplest type of IoT sensors- vibration, current, particle, temperature, humidity, etc. connects wirelessly. These sensors then communicate with our networks where we secure, move, and reduce data we want to persist or keep, as well as discard the data when it’s perishable.
When we move to communication, the most tangible and relatable mobility use case, we typically think about providing workers with mobile devices like tablets and phones. Mobile communications enable workforces to do their jobs at the place of work. Wi-Fi enabled voice, makes it possible to replace licensed use of hand-held paid spectrum and cellular fees by shifting to Wi-Fi enabled communicators.
Of course, with Wi-Fi mobile communicators, everyone on the factory floor gains immediate access to factory floor personnel as well as receive real-time notifications, pages, and safety alert messages.
Wireless video has become part of our daily lives, typically through applications like
Cisco WebEx, Facetime, and many others. On the shop floor or in a warehouse, the video capabilities take communications to the next level. Video on the shop floor, whether enabled by a mobile phone or tablet, immediately takes away the mystery of trying to imagine what is happening or what has happened.
The business benefits of mobility
Because every dollar spent in manufacturing is tied to a return on investment, it’s crucial to map mobility capabilities to business needs and benefits.
Ultimately, factory wireless solutions enable essential business benefits like less downtime, fewer line stoppages, improved worker efficiency, increased cycle time and higher OEE, which means better productivity, availability, and quality.
The
Cisco Factory wireless platform includes our products, services, partners and solution implementation plans. Together, all of these components provide what’s necessary for customers to deploy and scale their wireless capabilities.
A manufacturing plant is like a living organism – requiring care and feeding in all areas. Every organism must be part of a connected ecosystem, sensing and sharing information across all parts to ensure not just survival, but growth as well.
While we wouldn’t attach a Fitbit to a piece of manufacturing equipment, we will deploy wireless and mobility capabilities in our factories to monitor and connect our equipment, resulting in operational benefits with improved cost, quality, and delivery.