Headlines in 2018 include several data breaches where the acquired company led to an incident for the acquirer. A large travel site reported a data breach of information on 880,000 payment cards in March of 2018. The attack was believed to compromise systems months earlier. The investigation determined that the incident was potentially linked to legacy IT systems from an acquired company. Failure to update or integrate these systems left the parent company potentially vulnerable.
A Baltimore-based apparel manufacturer reported a data breach affecting customers who leverage the company’s sports tracking app. 150 million customer records associated with the app were compromised. The app creator was acquired by the parent company in 2015. Compromised data includes usernames, passwords and email addresses.
Companies with an acquisition strategy need to include information security in the M&A process. Many security tools can be leveraged to provide visibility into an organization’s network, users and information. These visibility tools should be used to determine the accessibility of information to both appropriate personnel and unauthorized parties. Understanding the vulnerabilities, network segmentation, access to assets and information, and asset lifecycle management are important negotiation metrics.
The acquiring company should be able to run visibility or vulnerability assessments of the target company as part of the negotiation. Vulnerability scanners help gather risk data. NetFlow and network traffic metadata tools provide visibility into the scope and nature of an organization’s traffic. This can help an organization identify and inventory assets. Visibility into web traffic, DNS queries, and applications in use all contribute to a view of an organization.
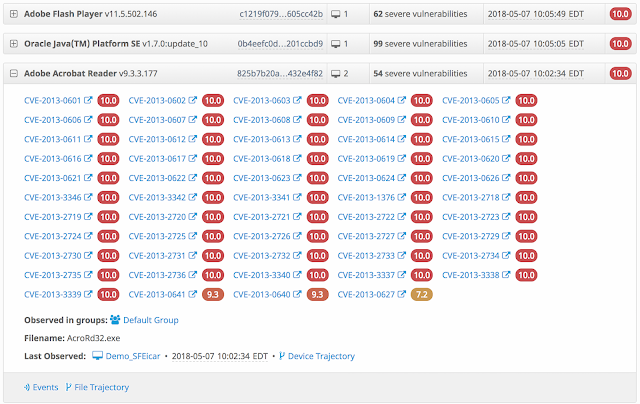
Vulnerable software report from AMP for Endpoints
These tools can help to establish where the target company is in terms of risk mitigation and security posture. It can tell the acquiring company how many man hours will need to go to get the target company to the appropriate levels of risk. An intelligent organization’s leadership understands that security is essential to all parts of the network. Proactive planning for growth and development must also be part of that security strategy.
Incident Response teams often use security tools to provide visibility into an organization following a data breach. These same tools can provide visibility into a target company’s information systems and networks. Use of these tools in advance of an acquisition can provide insight into the projects, security awareness training and even culture change necessary to understand the role of security in modern IT. Implementation of non-disclosure agreements can protect both the acquiring company and the target from leaks due to any gaps in the organization’s security posture.
Legacy systems have led to organizations appearing in the headlines. The brand damage, class action lawsuit payouts, data breach notifications and payment for services such as identity theft are all avoidable. Introducing and executing on a strong information security strategy as part of the M&A process is one way for organizations to minimize risk exposure and to understand the challenges and steps to achieving their desired security posture.
Leaders in organizations are accountable for the risk and exposure of users, information and networks. Visibility into these facets of an organization are key to ongoing security and to informed expansion, including mergers and acquisitions. The call to action for these organizational leaders focuses on that visibility. Research visibility, traffic profiling, application discovery and vulnerability tools. Speak with the organization’s trusted advisors, both internal and external, about the tools available and their recommendations. Regularly speak with the organization’s business leaders about emerging markets and potential mergers. Create and maintain an open dialogue about the potential risks and exposures that come with M&A. Many business leaders understand the importance of security in day-to-day operations. Including potential future business expansion in that conversation will help to craft a strategic information security policy.