Consider for a second how you think about your vehicle’s maintenance. If you’re like the majority, you might drive your car every day and feel confident that you can get from place to place without scheduling a routine checkup every 5000 miles, as automotive experts suggest. You might wait for a signal to prompt that something is wrong, whether it’s a check engine light, tire pressure warning, etc. to take your car in to get serviced. And then it’s back to getting from point A to point B every time you step in your vehicle. The problem is, all the buttons and warning signs inside your vehicle can signal that everything is ok, but they don’t necessary provide information on the health of all the underlying parts.
Driving as if everything is ok without performing routine checkups is a lot like monitoring your network without rigorously evaluating it on a consistent basis. Just as parts of your car can deteriorate or break without your knowledge, network support and capacity thresholds are often broken from incremental requirement burdens that the network has to shoulder. This results in teams consistently performing corrective network maintenance, costing more and creating longer downtimes in the long run. In fact, results show that “preventative maintenance represents roughly 10-30 percent of total maintenance costs as compared to corrective maintenance.”
One idea is to set some time aside – either once or twice a year – and perform a thorough network audit. It may seem mundane and unappealing at first but think about the potential value it could bring your team (and the organization) if you found a major problem or gap ahead of time. For example, what if you were upgrading to high-resolution video but found that the network was experiencing consistent packet drops? Or what if you were deploying a new unified communications solution but found your network’s Quality of Service (QoS) was never revisited for real-time voice and video applications 7-8 years after it was first deployed?
IT organizations that routinely do this before a new deployment or cloud migration often find the most value and are able to get buy-in from other critical stakeholders, such as those in finance and upper management, for future change initiatives. They are able to articulate the severity of repercussions if something goes wrong, which can often include an “all-hands-on-deck” situation for IT and extra costs incurred for the whole company.
Another benefit is that audits help bridge a gap between executives and IT. An audit creates a foundational platform in which both parties can understand what’s most important through an objective report. This has often served as a catalyst for IT departments to get projects approved as they are able to finally provide credibility and evidence for specific recommendations that had initially been declined for not being “a priority” or for being “too complex” of a solution.
If you’re interested in trying this yourself, take three of your sites and at least one data center and simulate what the network traffic would be with your new collaboration solution. Monitor the key parameters (e.g. jitter, delay, packet loss, etc.), the bandwidth difference, and how the network’s load-balancing changes throughout the session. Then perform a risk analysis with your findings, which can include:
◈ A list of gaps, problems, and likely future issues
◈ An as-is scenario that highlights the likelihood and magnitude of associated risks
◈ A list of necessary and recommended upgrades
◈ Predicted cost, timing, and impact of upgrades
◈ Expected deployment date after upgrades are made
The goal is to spot areas that have been overlooked and to identify key drivers that could negatively impact future upgrades and solutions.
If you’re open to having an external party help you do this, Cisco has a couple audit options that might benefit you, including a:
- Cloud Collaboration Readiness Assessment
- Media Network Readiness Assessment (for video and Webex deployments)
- Network Readiness Assessment (for UC and Contact Center deployments)
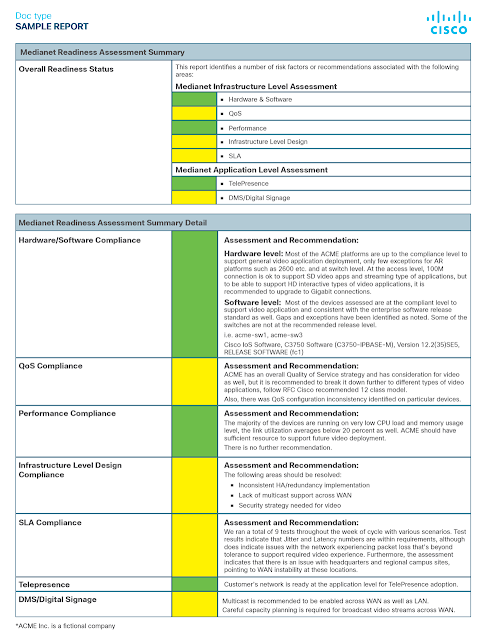
Each Readiness Assessment consists of a detailed analysis of your foundational network (critical Layers 1-3), including security and compliance, so you can easily upgrade your collaboration technology without hassle or fear. Each assessment also addresses reliability requirements and validates your network’s capacity to deliver desired business outcomes, helping you understand the implications and repercussions of different options before you deploy or migrate. To help provide some context, let’s look at a quick example.
Last year, a global leader in consumer and business credit reporting wanted to upgrade its Contact Center solution and agreed to have a Network Readiness Assessment beforehand so it could properly address any concerns. The IT department initially resisted the idea but later agreed, noting:
◈ All bandwidth requirements had been met
◈ The network was highly redundant and had no known issues
◈ IP routing was in good shape
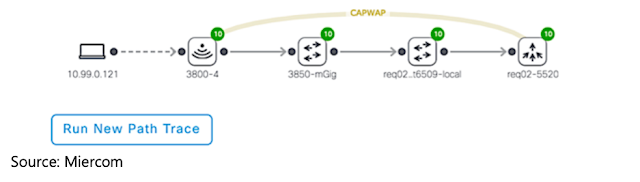
After identifying eight sites and two data centers to perform the assessment on, the Cisco Customer Experience team installed its proprietary software and simultaneously set up a network probe at each of the eight sites to simulate real time RTP traffic. It found:
◈ The IP routing between the eight key sites was not configured properly and the convergence time was too high, causing network packet drops
◈ The bandwidth was not configured properly to handle the amount of traffic to be deployed
◈ The QoS and network policies were outdated and needed to be updated before the upgrade
Ultimately, without the assessment the customer’s network would have likely crashed with the new deployment, costing millions and requiring all IT personnel to immediately fix the problem.
Turning your department from a reactive standpoint to a proactive one can help you better anticipate outcomes and problems before they occur. If you’re thinking about conducting a network audit on your own for your next collaboration upgrade, consider what resources you need to create a good report and the questions you’ll need to ask yourself along the way. What would have to be true in my audit in order to convince management to think differently? How do I ensure that my results are accurate and that I have the right data to back up my findings? How do I get others involved to create buy-in and to not upset those who would be impacted?
Driving as if everything is ok without performing routine checkups is a lot like monitoring your network without rigorously evaluating it on a consistent basis. Just as parts of your car can deteriorate or break without your knowledge, network support and capacity thresholds are often broken from incremental requirement burdens that the network has to shoulder. This results in teams consistently performing corrective network maintenance, costing more and creating longer downtimes in the long run. In fact, results show that “preventative maintenance represents roughly 10-30 percent of total maintenance costs as compared to corrective maintenance.”
So, what can you do?
One idea is to set some time aside – either once or twice a year – and perform a thorough network audit. It may seem mundane and unappealing at first but think about the potential value it could bring your team (and the organization) if you found a major problem or gap ahead of time. For example, what if you were upgrading to high-resolution video but found that the network was experiencing consistent packet drops? Or what if you were deploying a new unified communications solution but found your network’s Quality of Service (QoS) was never revisited for real-time voice and video applications 7-8 years after it was first deployed?
How would packet drops affect your network before a new deployment?
Would you catch them in time?
IT organizations that routinely do this before a new deployment or cloud migration often find the most value and are able to get buy-in from other critical stakeholders, such as those in finance and upper management, for future change initiatives. They are able to articulate the severity of repercussions if something goes wrong, which can often include an “all-hands-on-deck” situation for IT and extra costs incurred for the whole company.
Another benefit is that audits help bridge a gap between executives and IT. An audit creates a foundational platform in which both parties can understand what’s most important through an objective report. This has often served as a catalyst for IT departments to get projects approved as they are able to finally provide credibility and evidence for specific recommendations that had initially been declined for not being “a priority” or for being “too complex” of a solution.
If you’re interested in trying this yourself, take three of your sites and at least one data center and simulate what the network traffic would be with your new collaboration solution. Monitor the key parameters (e.g. jitter, delay, packet loss, etc.), the bandwidth difference, and how the network’s load-balancing changes throughout the session. Then perform a risk analysis with your findings, which can include:
◈ A list of gaps, problems, and likely future issues
◈ An as-is scenario that highlights the likelihood and magnitude of associated risks
◈ A list of necessary and recommended upgrades
◈ Predicted cost, timing, and impact of upgrades
◈ Expected deployment date after upgrades are made
The goal is to spot areas that have been overlooked and to identify key drivers that could negatively impact future upgrades and solutions.
If you’re open to having an external party help you do this, Cisco has a couple audit options that might benefit you, including a:
- Cloud Collaboration Readiness Assessment
- Media Network Readiness Assessment (for video and Webex deployments)
- Network Readiness Assessment (for UC and Contact Center deployments)
Last year, a global leader in consumer and business credit reporting wanted to upgrade its Contact Center solution and agreed to have a Network Readiness Assessment beforehand so it could properly address any concerns. The IT department initially resisted the idea but later agreed, noting:
◈ All bandwidth requirements had been met
◈ The network was highly redundant and had no known issues
◈ IP routing was in good shape
After identifying eight sites and two data centers to perform the assessment on, the Cisco Customer Experience team installed its proprietary software and simultaneously set up a network probe at each of the eight sites to simulate real time RTP traffic. It found:
◈ The IP routing between the eight key sites was not configured properly and the convergence time was too high, causing network packet drops
◈ The bandwidth was not configured properly to handle the amount of traffic to be deployed
◈ The QoS and network policies were outdated and needed to be updated before the upgrade
Ultimately, without the assessment the customer’s network would have likely crashed with the new deployment, costing millions and requiring all IT personnel to immediately fix the problem.
Turning your department from a reactive standpoint to a proactive one can help you better anticipate outcomes and problems before they occur. If you’re thinking about conducting a network audit on your own for your next collaboration upgrade, consider what resources you need to create a good report and the questions you’ll need to ask yourself along the way. What would have to be true in my audit in order to convince management to think differently? How do I ensure that my results are accurate and that I have the right data to back up my findings? How do I get others involved to create buy-in and to not upset those who would be impacted?
A good practice is to assume there’s already something wrong
in your network. Doing so will help give you the drive to ensure that
each possible risk is rigorously evaluated.
Learning what could prevent future success is arguably just as important as understanding what facilitates it in the first place.