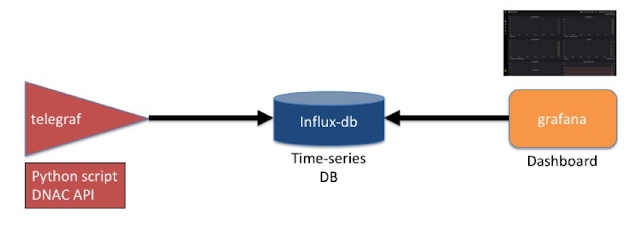
So begin by checking your topic against a few basic criteria:
◈ Does the article answer a question?
◈ Does it explain how to do something?
◈ Is it an “evergreen” topic that won’t quickly go out of date?
◈ Is it suggested by Google?
That last criteria makes it a sure bet it has SEO potential. If you see that Google is suggesting the phrase when you begin typing, it’s vetted as a search-friendly topic.
You’ve picked your topic, so you’ve picked your target keyphrase. Now we’re ready to begin constructing a search friendly article.
Tip! Keep in mind that the longer the keyphrase, the easier it is the rank for. Only the very famous websites will rank for one- and two-word phrases. Virtually any website can rank for the six- and seven-word phrases!
1. Search-Friendly Title and Headline
The title tag (<title>) and the header (<h1>) should both include the target keyphrase, ideally at the beginning.
The title and the header don’t need to be identical. Headers can be long, but for the title tag, keep the total length to 60 words. This will keep it from getting truncated when Google uses the title as the link in Google search results.
Consider using punctuation such as parentheses or a colon to create double headlines. The first half should use the target keyphrase. This helps the rankings. The second half should use numbers, specific benefits or unexpected words. This helps the clickthrough rate.
Here are a few examples:
◈ Video Conferencing Tips for Sales Teams: 5 tips for better remote meetings
◈ Career Tips for Tech Support Professionals (and how to jump to a senior role)
◈ How to Configure a Switch to Be a Root Bridge: 3 Steps for Manual STP Setup
2. Semantically Related Phrases
It’s good to use the target keyphrase in the body text. It’s even better to use the semantically related phrases. Which phrases are semantically related to your topic? Look around and you’ll find them everywhere:
◈ Other words suggested by Google when you search for your target keyphrase
◈ Phrases in the “Searches Related to” box at the bottom of the search results page
◈ Questions in the “People also ask” box
As you write, work these into your article. It’s good for rankings because it’s good for quality. A great page on your topic should also cover these related subtopics. It should answer all of the related questions.
3. Format for Scan Readers
If the visitor clicks on your search listing, but leaves after just a few short seconds, Google sees this as an indication that your article isn’t high quality and isn’t rank-worthy. So getting the visitor to stick around is important for maintaining your rankings.
How can we get the visitor to engage? By making the content easy to scan. That starts with short paragraphs. No one wants to read a long, dense block of text. So keep your paragraph length down to three or four lines.
Next, use lots of formatting to keep the scan readers flowing.
◈ Subheads
◈ Numbered lists and bullet lists
◈ Bolding and italics
◈ Multiple images, diagrams, charts
◈ Contributor quotes from experts
We all have to accept that visitors aren’t going to read everything. Research shows that on a typical visit to a typical webpage, visitors have time to read 28% of the words at most (20% is more likely)
Source: NN Group
But visitors are more likely to keep reading, even if the article is very long, as long as it’s formatted to be easily consumed. So break it up, add white space, and help scanners get to the information they’re looking for quickly.
4. Research, Data, Statistics
Some assertions are backed by evidence. The rest are simply unsupported claims. When you add research data, you are instantly more credible. Your case is stronger. Your message is supported.
Example: The last section of this article made an assertion (formatting is important because visitors are scanning) that was supported by data (NN Group found that visitors aren’t reading everything) making the point stronger.
Bring data to your articles. It will give you the opportunity to add visuals and it will make your content more likely to be cited by others in their content.
5. Internal Links
Finally, search-friendly content is interconnected. It has links from other pages which give it authority. But it also creates deeper paths into other content, helping to prevent the visitor from going back to search results.
Here is a list of links that work:
◈ A link to an older article
Never miss the chance to connect your new articles to high value content you’ve already created.
◈ A link from an older article to your new article
You’re not done publishing something new until you’ve linked to it from something old!
◈ A link to a product or service page (on our site or on Cisco)
Ideally, this content drives demand. You can trigger this by gently guiding visitors toward offers that relate to your content. Anytime you mention a product or service, link.
◈ A link to a related article on another Cisco partner website
We should build relationships with other Cisco partners, let them know what we’re working on. We should find out what they’re publishing. And then link to each other whenever possible. This can do wonders for our search rankings long term.
Our content should work together, and we can work together to make it work harder. Our content should never be isolated and our teams shouldn’t work on islands.
Building interconnected hubs of content that links from one article to the next, on our site and on other partner sites can give us huge and durable benefits in SEO. Build a network of content creators and sync your publishing calendars. This, plus quality and persistence, is the key to winning the top spot in search.
To become a true SEO pro and learn even more about the tactics described above, be sure to check out my latest webinars in Marketing Velocity Learning. SEO Principles and Practices provides an introduction to creating high-ranking content and Advanced SEO takes you beyond the keyword for a practical approach to the future of search.