There are many variations of the “Law of Constant Change”; while they all have their own spin on it, the common thread is that change is constant and that it needs to be harnessed. When looking at changes and disruptions in technology, it comes as no surprise that there are numerous transformations and trends which are reshaping the IT landscape. The megatrends and change drivers span a wide range of business changes and transformation agents such as:
Saturday, 1 October 2022
Empowering the four IT personas using Cisco DNA Center with Rings of Power
Thursday, 8 September 2022
Quick automation wins with Cisco DNA Center
Out-of-the-box automation with Cisco DNA Center
Granular Automation Control
Focusing on automation outcomes and benefits
| Tangible Metrics | Intangibles |
|
Faster moves adds and changes |
Team Agility |
Tuesday, 26 April 2022
How To Do DevSecOps for Kubernetes
In this article, we’ll provide an overview of security concerns related to Kubernetes, looking at the built-in security capabilities that Kubernetes brings to the table.
Kubernetes at the center of cloud-native software
Since Docker popularized containers, most non-legacy large-scale systems use containers as their unit of deployment, in both the cloud and private data centers. When dealing with more than a few containers, you need an orchestration platform for them. For now, Kubernetes is winning the container orchestration wars. Kubernetes runs anywhere and on any device—cloud, bare metal, edge, locally on your laptop or Raspberry Pi. Kubernetes boasts a huge and thriving community and ecosystem. If you’re responsible for managing systems with lots of containers, you’re probably using Kubernetes.
The Kubernetes security model
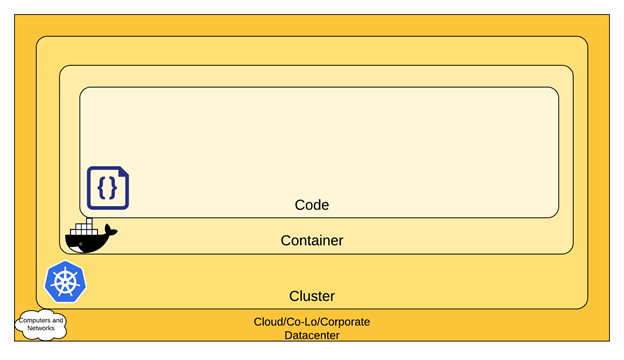
When running an application on Kubernetes, you need to ensure your environment is secure. The Kubernetes security model embraces a defense in depth approach and is structured in four layers, known as the 4Cs of Cloud-Native Security:
Read More: 350-801: Implementing Cisco Collaboration Core Technologies (CLCOR)
1. Cloud (or co-located servers or the corporate datacenter)
2. Container
3. Cluster
4. Code
Authentication
Authorization
Admission
Secrets management
Data encryption
Encryption at rest
Encryption in transit
Managing container images securely
Defining security policies
Monitoring, alerting, and auditing
Tuesday, 8 February 2022
What DevSecOps Means for Your CI/CD Pipeline
The CI/CD (Continuous Integration/Continuous Deployment) pipeline is a major ingredient of the DevOps recipe. As a DevSecOps practitioner, you need to consider the security implications for this pipeline. In this article, we will examine key items to think about when it comes to DevSecOps and CI/CD.
The type of CI/CD pipeline you choose—whether it’s managed, open source, or a bespoke solution that you build in-house—will impact whether certain security features are available to you out of the box, or require focused attention to implement.
Let’s dive in
Secret management for your CI/CD pipeline
Your CI/CD pipeline has the keys to the kingdom: it can provision infrastructure and deploy workloads across your system. From a security perspective, the CI/CD pipeline should be the only way to perform these actions. To manage your infrastructure, the CI/CD pipeline needs the credentials to access cloud service APIs, databases, service accounts, and more—and these credentials need to be secure.
Injecting secrets into workloads
Infrastructure as code: a security perspective
Bring your own security tools
Comprehensive detection and response
In case of faulty CI/CD, break glass
Friday, 5 February 2021
A Framework for Continuous Security
Technology is at the core of business today. Maintaining the resiliency of critical data, assets, systems, and the network is mission-critical; crucial to meeting business goals. As a result, development operations (DevOps) professionals must continuously improve the overall resilience —along with the security posture — of workloads, software, and applications (Figure 1). To do this at scale and speed requires the integration of a suite of application security tools in the continuous integration/continuous delivery (CI/CD) pipelines that automate posture assessment and provide visibility to help manage security risks.
At Cisco, we learned early on that application security processes were inhibiting our business agility. We knew we had to embrace an Agile and DevOps culture as early adopters to deliver software products based on business demands rapidly and iteratively. Agile DevOps without application security automation leads to a “hurry up and wait” situation, where some processes move quickly only to be bogged down by others. With evolving technologies such as cloud, Docker, Kubernetes, open-source as well as daily and frequent release cycles, it is hard for application security teams to keep up with the threat landscape. In a typical modern application development and deployment technology stack, 80% of the code base is comprised of third-party software. Only 20% is custom code. Most of the security breaches we have seen in recent years were entirely preventable had there been necessary security measures taken, not only for the custom code but also for the third-party software.
We set out to create a DevSecOps culture that empowers the application teams to continuously build and deploy secure applications instead of being gated by a central security function. To do this, we integrated and orchestrated a suite of application security tools within CI/CD pipelines under a program called Continuous Security Buddy (CSB) for CI/CD pipeline edition. It enables the development teams to ramp up their application security program while making application security transparent and friction-free.
Co-design and Co-development of the Solution
Security Scan Flexibility
Automated Compliance Reporting
Measuring Progress and Success
Thursday, 14 May 2020
How do you gauge software quality before deployment?
With more than two decades in the industry, I understand the software development life cycle thoroughly, its processes, metrics, and measurement. As a programmer, I have designed and developed numerous complex systems, led the software development strategy for CI/CD pipelines, modernized processes, and automated execution. I have answered the call for stellar customer journey analytics for varied software releases, allowing our business to grow to scale. Given my background, I would like to share my thoughts on our software development process, product and feature release quality, and strategies to prepare for successful product deployments. I look forward to sharing my opinions and collaboratively working with you on building customer confidence through high-quality software deployments.
But, before I begin, here are some terms the way I think of them:
◉ Product Software Release— Mix of new and enhanced features, internally or customer-found defect fixes, and may contain operational elements related to installations or upgrades.
◉ Software Release Quality— Elements like content classification, development and test milestones, quality of the code and test suites, and regressions or collateral to track release readiness prior to deployment.
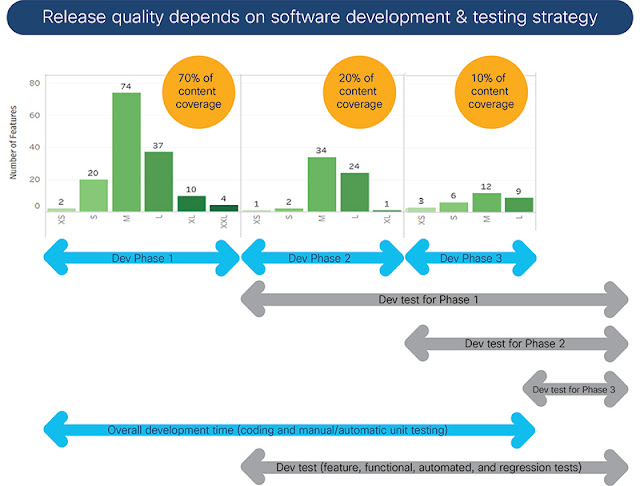
◉ Release Content— Classified list of features and enhancements with effort estimations for development. For example, we may use T-shirt size classification for development efforts (including coding, unit testing, unit test found bug fixes, and unit test automation): Small (less than 4 weeks), Medium (4-8 weeks), Large (8-12 weeks), Extra-Large (12-16 weeks). Categorize feature testing similarly as well.
◉ Release Quality and Health— Criteria for pre-customer deployment quality, with emphasis on code and feature development processes, corresponding tests, and overall release readiness.
Through this lens, let’s view the journey of our Polaris release. Before we do, let me emphasize that quality can never be an afterthought, it has to be integral to the entire process from the very beginning. Every aspect of software development and release logistics require you to adopt a quality-conscious culture. I believe there are four distinct phases or checkpoints to achieve this goal:
Thursday, 5 March 2020
Unify NetOps and SecOps with SD-WAN Cloud Management
Conflict or Collaboration?
The problem of balancing the goals of NetOps with SecOps has a lot to do with how the network and all the connected devices and domains are being managed. Traditionally in NetOps, there have been separate consoles and Unified Computing Servers (UCS) to configure, monitor and analyze network domains – several for the data center, multiple for the campus wireless network, and still more for cloud, branch, and edge deployments.
Similarly, in order for SecOps to capture, log, and analyze traffic in all the various domains, special taps are installed where traffic is entering and leaving the domains. SecOps has an additional burden of storing all the traffic logs in case of a breach or successful malware attack in order to pinpoint the cause and prove appropriate steps are taken to remediate breaches and prevent future attacks.
That’s a lot of boxes to buy, install, and securely manage—a number that grows with each expansion of the enterprise network. Ironically, the extra compute devices needed by SecOps ultimately have to be managed by NetOps to ensure they do not affect overall network performance. Thus, more conflict.
Can NetOps and SecOps get to the point of collaboration instead of conflict? In fact, new cross-enterprise business initiatives make collaboration a necessity.
Digital Transformation Projects Benefit from Unified Operations and Security
As organizations seek new ways to connect with customers, suppliers, and service partners by making business processes personal and frictionless, they initiate application development efforts that span across operations. A unifying foundation for these development efforts are the NetOps and SecOps teams.
Deploying new multi-cloud applications or moving processes to the edge—retail outlets, branch offices, medical clinics—requires assurance that the network is responsive, always available, and secure. NetOps needs to work with Development teams to understand network SLAs and cloud usage requirements for the new apps. SecOps needs to ensure that the proper network permissions, segmentations, and polices are applied to the network at application launch time. NetSecOps collaboration is key to timely deployment of next-generation applications with security and the required levels of performance.
Collaboration is important too in the battle of the budgets. With IT budgets generally flat over the last few years, making sure NetOps and SecOps teams use both CapEx and OpEx funds judiciously is critical for maximum efficiency. There is an opportunity to combine NetOps and SecOps teams to generate the most value from the available budget, equipment, and knowledge of how an enterprise’s unique network responds to changes in applications and threats.
From these examples, you can see that unifying NetOps and SecOps has solid benefits for enterprise digital transformation efforts. Is there a technology platform that makes unification not only possible, but also makes the transition a natural evolution rather than a forced organizational change? By combining a software-defined network fabric with single-console cloud management, SD-WAN can play a significant role in the unification of NetSecOps.
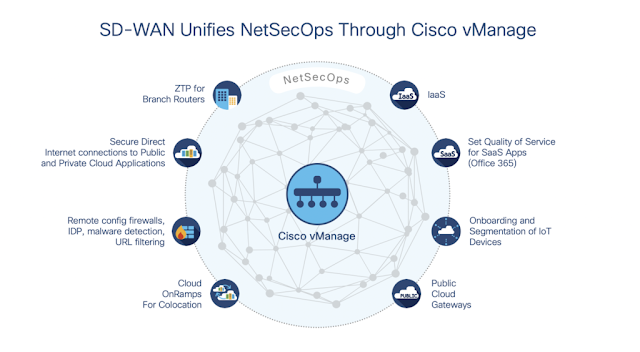
SD-WAN Unified Network Cloud Management for NetSecOps
A primary benefit of Cisco SD-WAN powered by Viptela for NetSecOps is the ability to provide a single, role-based interface in Cisco vManage to control network performance, segmentation, and security. Through the lens of vManage, NetSecOps can:
◉ Install and configure branch SD-WAN routers remotely with Zero Touch Provisioning (ZTP)
◉ Automatically route traffic through the most efficient and cost-effective path (MPLS, broadband, direct internet, LTE/5G) using dynamic path selection.
◉ Manage performance, security, and access policies for cloud onramps to SaaS, IaaS, and colocations.
◉ Remotely configure and manage at the branch level the application-aware firewalls, URL-filtering, intrusion detection/prevention, DNS-layer security, and Advanced Malware Protection (AMP) to secure branch traffic that is using direct internet connections to SaaS applications.
◉ Drawing on policies set up in Cisco SD-Access and Identity Services Engine (ISE), NetSecOps can collaborate to configure segmentation rules that are uniformly applied across distributed locations to keep traffic separated—such as employee wireless access from payment system traffic—improving performance and security.
Managing and Protecting East-West Traffic Flow and Security in Branches
With the plethora of integrated security layers that comes with Cisco SD-WAN, traffic entering and leaving a branch is thoroughly inspected for application infiltration, intrusion by malware, and accessing known bad URLs. But there is still the tricky problem of when malware is introduced by a device or someone inside the branch network.
In the days of spoke and hub WANs, traffic from each device within a branch would be backhauled to the enterprise data center for inspection and verification, and then back to the branch. This has always been a troublesome scenario for NetOps as the traffic load for just backhauling and inspecting interfered with traffic that legitimately had to go the data center for additional processing. The alternative, of course, was to lock down all the endpoints in branches, limiting their flexibility and any options to BYOD for employees.
Securing Access to SaaS Applications via Direct Internet Connections
The workforce is quickly becoming more dependent on applications hosted in SaaS cloud platforms, such as Office 365, which require routing through direct internet access. With SD-WAN, NetSecOps can focus on not just fine-tuning application performance but also the defenses that secure the valuable corporate data being transmitted over the internet connections to and from branch sites. By using Cisco SD-WAN Cloud OnRamps to SaaS and IaaS clouds, the network selects the path that is the most effective to handle Azure, AWS, or Google Cloud workloads while the built-in layers of security provide protection with DNS URL filtering, advanced malware protection, and application-aware firewalls. Both application performance and security are managed by NetSecOps via the SD-WAN vManage cloud controller portal.
Fostering Collaboration Among NetOps and SecOps is Key to Network Agility
With Cisco SD-WAN’s ability to manage operations and security via the same cloud portal, it really is achievable to create a NetSecOps team that promotes collaboration, reduces CapEx and OpEx, and maximizes device and application QoE and security. Unifying these two critical functions helps create an agile network that makes digital transformation projects possible while keeping on top of advanced security threats. I’d like to hear your thoughts on the ways SD-WAN can provide better synergy between operations and security.
Thursday, 3 October 2019
Tune in: “Demystifying Cisco Orchestration for Infrastructure as Code”
Automating the software development life-cycle
DevOps teams are becoming more agile, reducing costs, and delivering a superb customer experience by automating the software development life-cycle. Cisco Orchestration solutions extend the benefits of automation to the entire stack. Each layer of the underlying infrastructure is delivered as Code (IaC). Orchestrators reduce the complexity of programmability, operational state, and visibility. In this session, we decode the differences between domain-specific workflow automation versus cross-domain orchestration. Achieving the goal of ‘Automate everything’ requires the right tool for the right use case. With use cases in mind, we will cover several Cisco orchestration solutions in their respective domains and cross domain capabilities. A brief demo will showcase Open Source and Cisco Orchestration tools working together hand-in-hand.