About four years ago, my team at Cisco sat down to re-architect enterprise networking, because we knew that the traditional models for running networks were not going to be able to scale with the changes being forced on to them. For example, we saw that the number and types of devices connecting to networks was growing exponentially; that the security perimeter was shifting from data center to being fully distributed in the network; and that wireless networks had become primary networks, not overlays. Meanwhile, networks were getting more business-critical. Even life-critical.
Fortunately, the technologies available to address these challenges are evolving as well. Wireless technologies, AI, rich behavioral and telemetry databases, more flexible and economical WAN links, and abundant cloud compute resources are becoming available to address the new reality.
These are some of the reasons we have gone all-in with intent-based networking (IBN). We released our first products that supported IBN in 2017 – primarily the Catalyst 9000-series switches and Cisco DNA Center. And it’s why we acquired the SD-WAN innovator Viptela, also in 2017.
Behind these new products and acquisitions there is a long-term vision. All our new enterprise products are based on seven core tenets of this vision. I want to explain those here. It may help you see the strategy behind the products we have launched in the past few years. And it will give you an idea of the new services and tools we’ll be rolling out soon.
1. Controller-Based Networking
Networks are complex systems, and a core focus of intent-based networking is that they should be run and managed as cohesive systems. That means network managers need a controller, from which they can monitor, manage, and automate their networks, and eventually create closed-looped systems.
A controller-first system architecture is made up of loosely-coupled systems. It allows network devices and controllers to be upgraded individually, without causing major network disruptions (no more “flag days.”) And by using APIs and well-defined data structures for communication between devices, we also get a system in which programming, maintenance, and upgrading to new capabilities is more straightforward.
2. Wireless as an Equal to Wired
In the past, enterprise networking meant wired networking: cables and fibers connecting critical devices to each other. Wireless, for the most part, was seen as an emerging access technology for devices on the edge of the network. Wireless networks were built as overlays on top of the wired networks. The separation into different infrastructures led to inconsistent policies and operating models between the wired and wireless clients.
We can no longer relegate wireless communication to a different system. Wireless is the predominant access technology for end-user and IoT devices, and to keep these devices managed and secure, we need to think of wireless and wired as one network.
In our latest access products, from our switches like the Catalyst 9300 to Wireless Lan Controllers (WLC) like the Catalyst 9800, we use the same fundamental technologies: The same line of ASICs and the same operating systems. This was not a superficial change. We reengineered our entire line for this, so that the same networking capabilities and security could be enabled for all our devices, and so user policies would be the same no matter what access medium the user was on.
3. Integrated Security
The most modern and insidious security threats often come in today via end-user devices. In addition to traditional attacks focusing on data theft, the goal of many attacks today is destruction of infrastructure, by encrypting and denying access to critical information. But traditional firewalls are much less effective with attacks that move from device to device inside a network, which is a growing threat in the era of wireless, which, from a security perspective, is also the era of the network without a perimeter. There is no “DMZ” anymore. Infected devices can launch attacks no matter what network they are on, and their attacks can jump not just from machine to machine, but from network to network. The only way to prevent these attacks is for the network to act as the first line of defense.
Because these security threats are more complex, and attacks more fluid, it’s important that we use network segmentation as a primary security tool, instead of relying primarily on blacklists. We need dynamic, controller-based systems to manage segmentation and whitelisting across network domains to make sure that people, apps, and devices have access to the resources they need, but that they are never put in contact with the devices, apps, and networks they don’t.
Complementing the network segmentation, we also need to evolve our ideas of where and how we deploy traditional security functions. Along with the traditional standalone deployment models, security services need to be fully integrated with switches and routers, as well as available as cloud services.
Overall, we need networking to be and integral part of how we secure the enterprise against modern threats.
4. Data-Driven
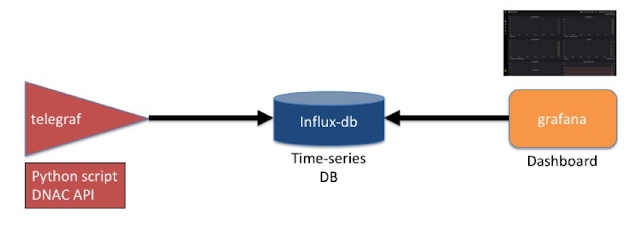
The key to everything we’re building now is data. Data from every dimension of our networking equipment can be collected, collated, parsed, and analyzed. Because when we know what our network equipment is doing we know if it is delivering on our customers’ strategic and day-to-day needs. In Cisco DNA Center, data powers our Assurance capability, which helps us close the loop from intent to action. (In vManage, vAnalytics plays this role.)
The massive amount of information could be overwhelming. Standard algorithms can help us find standard issues that crop up. Beyond that, we rely on machine intelligence to perform complex correlations and generate more valuable insights, like spotting pattern-breaking behavior that may indicate problems on the network.
We are also pioneering the field of machine reasoning to combine machine intelligence with knowledgebases created by teams of experts, to provide smart alerts to network operators, and ultimately, automatic remediation of issues to improve our customers’ experiences with their networks.
5. Cloud-First
This machine intelligence runs locally on our customers’ networks, but there’s extra benefit to be gained when we combine metadata about network use across enterprises. Many of our machine learning capabilities use cloud-based resources, primarily to leverage the vast resource of global data on how networks are performing, and the issues they are facing. This is how the information security industry has long been identifying and remediating global zero-day exploits; we use similar capabilities, seasoned with AI, to improve day-to-day network performance and efficiency for all. No matter where our controller systems run – on-prem or in the cloud – using cloud-based data makes the network more powerful and proactive.
We are also delivering updates to our controllers’ software from the cloud, instead of requiring network operators to manually pull software and update these systems. Furthermore, the rich telemetry we can get from cloud-connected devices enables us to roll out software upgrades gradually across our customer base – and even within customers’ installations. This way, customers can keep up with security issues, and we can deliver new capabilities as we develop them. And yes, it sounds basic if you’re accustomed to using consumer devices like smartphones, but designing controllers for over-the-air updates is a change in this industry – just like Tesla’s ability to roll software updates out to customers’ cars has changed the expectations for how the auto industry delivers software to the car.
While nearly all our customers are moving to cloud-based systems architectures, that transition can be a complex, multiyear journey. For now, most networks are hybrid, on-prem plus cloud, and will be for a long time. In order to seamlessly operate these hybrid networks, customers need consistent features across all their devices and services. We are enabling this by delivering IOS-XE on physical switches & routers, and as virtual instances in the cloud.
6. Support for Existing Networks
It’s one thing to design a networking system using all modern concepts and systems. But the real world isn’t a green field of open racks and empty conduit. We need our systems to work in our customers’ existing “brown field” installations. Businesses generally upgrade infrastructure gradually, piece by piece. Older networking components have to co-exist with the new. “Rip and replace” isn’t a workable implementation tactic.
That is why, although we built Cisco DNA Center and all our new Catalyst 9000-series hardware to be programmable using new, well-defined APIs and new interaction capabilities, we also control and gather data from older products, using traditional CLI (Command Line Interface), SNMP (Simple Network Management Protocol), and other legacy control schemes. Cisco DNA Center presents the network operator – and network applications – with a unified modern interface for all network equipment, and it chooses the best way to connect to the equipment to carry out the operator’s intent.
Similarly, to support the installed base of equipment on existing networks, we are also enabling SD-WAN and vManage on older ISR platforms, so customers can introduce SD-WAN into their current deployments.
7. Multi-Domain
Today’s networks are made up of multiple operational domains (for example: campus, data center, and security), that are tightly linked. Today’s customers need more than interconnected domains. To support business needs, they need security and access policy that spans domains, and they need the agility to support new needs as they arise, with complete end-to-end visibility.
The need for tight integration, despite the differences in the domains, is one of the biggest drivers for moving to a controller-based, fully abstracted architecture.
I’ve long believed that Cisco is uniquely positioned to create this holistic and end-to-end system, and to help businesses create these networks for their own uses. No matter which domain these critical transformation projects starts at, eventually they will need to end up in the same place: With a true multi-domain, any-to-any network controller architecture.
The Goal: Closing the Loop and Supporting Business Transformation
Business today requires infrastructure that responds to technical issues immediately and automatically – in machine time, not human time.
Our intent-based networking systems are designed to close the loop from intent, to activation, to continuous verification (Assurance) – quickly addressing deviation from the original intent.
Intelligence can enter the loop from several sources, including people and systems outside of Cisco: Our network controllers learn from their environment, providing intelligence to developers and partners, so they can add value in the feedback loop – for example, with smarter service desk tool, or automated troubleshooting systems.
The network systems can also be a part of larger business feedback loops. When the entire network is sensing its environment, that data can feed into systems that serve other purposes. For example, we can use the location intelligence our networks gather about the devices they serve, to inform business processes in a way that has simply not been possible before.
That’s why training and certification programs are part of our journey to intent-based networking. Education has always been in our DNA – we’ve been certifying technical personnel since 1993. We recently added new programs for app developers, too, recognizing the role these skills will play in the future of network management.
No matter how much we automate and simplify the management of networks, there will always be new opportunities to improve how a network works, to increase its efficiency, and to use it to help a business succeed. Our customers know where they need to take their technology. We’re going to help them get there.