I can understand if you dread configuring network segmentation. Not only is it hard to configure the many different switches and routers, creating VLANs, using ACLs to create lists of permit or deny IP addresses, it is also easy to make mistakes and risk shutting down parts of the network. And with users and devices moving around, you must continuously modify these configurations. Is it any surprise that many of today’s networks are not optimally segmented?
In this blog we discuss how Cisco Digital Network Architecture (Cisco DNA) makes it easy to segment your campus and branch networks. This blog is the second in a series focusing on aspects of intent-based networking, the first being on controller-led architecture.
Before digging into the solution, let’s understand why you may want to segment your network in the first place.
◉ Enhanced security: Isolate and filter network traffic to limit communications between users and devices
◉ Better access control: Allow users and devices to access only authorized resources
◉ Improved monitoring: Log events, monitor connection attempts, and detect suspicious behavior
◉ Faster containment: Minimize the scope of a network breach
Recognizing that segmenting the network is a security must-have, we set about making it easy to do in Cisco DNA – the access network for campus and branch. Those of you who have experienced the Cisco DNA Center – the controller for a Cisco DNA based network – know that it provides a highly intuitive and easy to use graphical interface to manage the network and is the ideal platform to define segmentation. For those who haven’t, we encourage them to attend one of our monthly demo sessions where we explain what Cisco DNA can do for you.
Cisco DNA Center allows you to easily manage security policies through policy-based abstractions called scalable groups. Scalable groups are used to represent connected users and devices based upon attributes, like role, function, location, etc. rather than IP addresses. These groups then form the basis of security policies, centrally managed on Cisco DNA Center and enforced across the network fabric.
Cisco DNA Center enables simplified management of access control between the different groups, and dynamically configures the access control policy in the fabric consisting of switches, routers, and wireless network devices that make up the fabric.
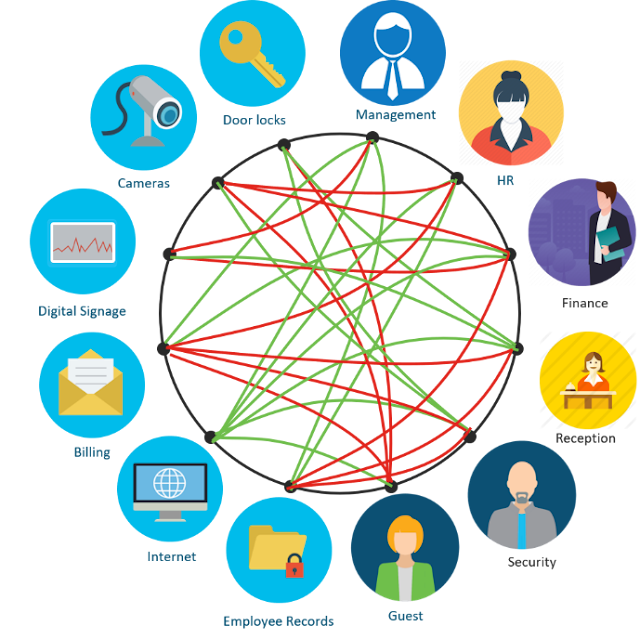
As people and things connect to the network using either a wired or wireless interface, Cisco DNA identifies them and automatically assigns them to their rightful group and places them in the appropriate segment. We call the creation of these Virtual Networks (VN), macro-segmenting.
But what about the communications between members within a VN? We need to control that too for a deeper level of security. We call this micro-segmenting. So, while macro-segmenting isolates traffic between VNs, micro-segmenting controls communications between different groups or members of the same group within the VN.
For example, you might define two VNs – an ‘Employee’ VN with management, HR, security staff, and financial analysts, and an ‘IoT’ VN with security cameras, door locks, and digital signage. With SD-Access macro-segmentation you can ensure that a compromised camera will not let the attacker access HR resources. While with micro-segmentation, you can prevent lateral spread of malware between say HR and security staff or between two financial analysts.
Cisco DNA Center makes it easy to micro-segment the network. The Access Control Application within Cisco DNA Center works with Cisco Identity Services Engine (ISE) to let you define contracts. Contracts are statements that permit or deny specific types of interactions. For example, if you are concerned about malware attacks that spread using well-known TCP ports of 22, 80, and 443, you can simply create a contract that would disallow such communications between members of the same group.
Once you define the contracts, you use a simple matrix within Cisco DNA Center and activate them between source and destination groups. This matrix visually describes policies that the Cisco DNA Center consistently applies and enforces through the network fabric.
Just like Cisco DNA Center segments the access network and creates groups of users, Cisco ACI segments data center and cloud networks and creates groups of applications. Cisco’s multidomain architecture lets these networking domains exchange and map these groups. Now, thanks to this integrated segmentation, users can only run applications they are authorized for. For example, only accounting staff may access point-of-sale systems in keeping with PCI regulations.
In this blog we discuss how Cisco Digital Network Architecture (Cisco DNA) makes it easy to segment your campus and branch networks. This blog is the second in a series focusing on aspects of intent-based networking, the first being on controller-led architecture.
Before digging into the solution, let’s understand why you may want to segment your network in the first place.
◉ Better access control: Allow users and devices to access only authorized resources
◉ Improved monitoring: Log events, monitor connection attempts, and detect suspicious behavior
◉ Faster containment: Minimize the scope of a network breach
Group-based access control
Recognizing that segmenting the network is a security must-have, we set about making it easy to do in Cisco DNA – the access network for campus and branch. Those of you who have experienced the Cisco DNA Center – the controller for a Cisco DNA based network – know that it provides a highly intuitive and easy to use graphical interface to manage the network and is the ideal platform to define segmentation. For those who haven’t, we encourage them to attend one of our monthly demo sessions where we explain what Cisco DNA can do for you.
Cisco DNA Center allows you to easily manage security policies through policy-based abstractions called scalable groups. Scalable groups are used to represent connected users and devices based upon attributes, like role, function, location, etc. rather than IP addresses. These groups then form the basis of security policies, centrally managed on Cisco DNA Center and enforced across the network fabric.
Cisco DNA Center enables simplified management of access control between the different groups, and dynamically configures the access control policy in the fabric consisting of switches, routers, and wireless network devices that make up the fabric.
As people and things connect to the network using either a wired or wireless interface, Cisco DNA identifies them and automatically assigns them to their rightful group and places them in the appropriate segment. We call the creation of these Virtual Networks (VN), macro-segmenting.
The two levels of network segmentation
But what about the communications between members within a VN? We need to control that too for a deeper level of security. We call this micro-segmenting. So, while macro-segmenting isolates traffic between VNs, micro-segmenting controls communications between different groups or members of the same group within the VN.
For example, you might define two VNs – an ‘Employee’ VN with management, HR, security staff, and financial analysts, and an ‘IoT’ VN with security cameras, door locks, and digital signage. With SD-Access macro-segmentation you can ensure that a compromised camera will not let the attacker access HR resources. While with micro-segmentation, you can prevent lateral spread of malware between say HR and security staff or between two financial analysts.
Once you define the contracts, you use a simple matrix within Cisco DNA Center and activate them between source and destination groups. This matrix visually describes policies that the Cisco DNA Center consistently applies and enforces through the network fabric.
Segmentation that extends from access to apps
Just like Cisco DNA Center segments the access network and creates groups of users, Cisco ACI segments data center and cloud networks and creates groups of applications. Cisco’s multidomain architecture lets these networking domains exchange and map these groups. Now, thanks to this integrated segmentation, users can only run applications they are authorized for. For example, only accounting staff may access point-of-sale systems in keeping with PCI regulations.