With the proliferation of IoT and BYOD devices, wireless security is top-of-the-mind for network administrators and customers. Globally, there will be nearly 628 million public Wi-Fi hotspots by 2023, which is almost four-fold increase from 2018. This will increase the attack surface and hence the vulnerability for the network. The total number of DDoS attacks is predicted to reach 15.4 million by 2023, more than double the number from 2018. Due to inherent open nature of wireless communications, wireless LANs are exposed to multitude of security threats, including DoS flood attacks.
Sunday, 25 April 2021
Securing the air with Cisco’s wireless security solution
Thursday, 22 April 2021
The Need for Continuous and Dynamic Threat Modeling
The trend towards accelerated application development, and regular updates to an architecture through an agile methodology, reduces the efficacy and effectiveness of point-in-time threat modeling. This recognition led us to explore and strategize ways to continuously, and dynamically, threat model an application architecture during runtime.
Today, thanks to a robust DevOps environment, developers can deploy a complex architecture within a public cloud such as Amazon Web Services (AWS) or Google Cloud Platform without requiring support from a network or database administrator. A single developer can develop code, deploy an infrastructure through code into a public cloud, construct security groups through code, and deploy an application on the resulting environment all through a continuous integration/continuous delivery (CI/CD) pipeline. While this enables deployment velocity, it also eliminates multiple checks and balances. At Cisco, we recognized the risks introduced by such practices and decided to explore strategies to continuously evaluate how an architecture evolves in production runtime to guard against architecture drift.
Dynamic threat modeling must begin with a solid baseline threat model that is done in real-time. This can in turn be monitored for architecture drift. Our approach to obtain such a real-time view is to use dynamic techniques to allow security and ops teams to threat model live environments instead of diagraming on paper or whiteboards alone.
How Does Dynamic Threat Modeling Work?
Threat modeling is the practice of identifying data flows through systems and various constructs within an architecture that exhibit a security gap or vulnerabilities. A crucial element that enables the practice of threat modeling is generating the right kind of visual representation of a given architecture in an accurate manner. This approach can differ based on context and from one team to another. At Cisco, we instead focused on elements and features that need to exist to allow a team to dynamically perform a threat modeling exercise. These elements include the ability:
◉ To transform an operational view of an architecture to a threat model
◉ To contextualize a requirement
◉ To monitor the architecture for drift based on a requirement
From Operational View to Threat Model
Numerous tools exist that can render an operational view of an architecture. However, an operational view of an architecture is not the same as a threat model. Instead, an operational view must undergo a transformation to create a threat model view of an architecture. For this to occur, the solution should at a minimum provide a way to filter and group queries within an architecture so that only relevant data is visually rendered.
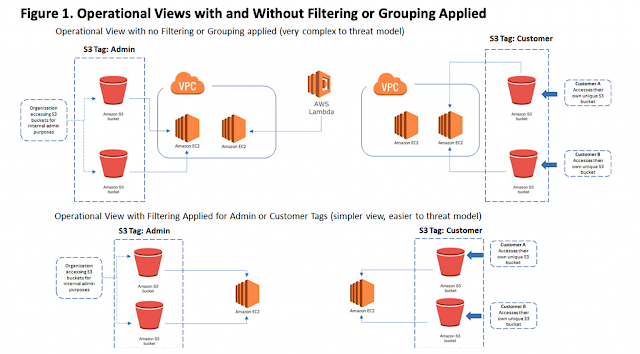
As an example, consider a case where an AWS hosted public cloud offer consists of two types of S3 buckets (Figure 1). One type of S3 buckets is deployed for customers for them to access directly. Each customer gets their own unique S3 bucket to access. Other types of S3 buckets are deployed for organization-specific internal administrative purposes. Both types of S3 buckets are identified through their AWS tags (“Customer” and “Admin” respectively). A filter-based query applied to an architecture of this type can answer questions such as “Are there S3 buckets with Tag: ‘Customer’ or ‘Admin’ in this architecture?”
Figure 1. Operational Views with and Without Filtering or Grouping Applied
What Does it Mean to Contextualize a Requirement?
Ability to Monitor the Architecture for Drift Based on Requirements
Challenges and What the Future Holds
Wednesday, 21 April 2021
Building Trust in Your Access Network
How do you know for sure that a router in your network has not been altered since you deployed it? Wouldn’t it be great if you could cryptographically challenge your router to provide its unique identity? In addition, what if the underlying OS could provide a secure mechanism to detect if the software had been tampered with during boot time and runtime?
Networking equipment manufacturers are seeing an increase in supply chain attacks, which means communication service providers (CSP) need tools that can detect the replacement of critical components such as CPU/NPU. Software security features are insufficient in detecting and protecting against these attacks if the underlying hardware has been compromised. To completely trust the device, CSPs need a chain of trust that is preserved in hardware manufacture, software development and installation, procurement, and live deployment within their network.
With 5G deployments gaining traction, routers are now increasingly deployed in distributed architectures (read as remote locations) and depended on as critical infrastructure. Cisco’s trustworthy platforms ensure customers can validate the authenticity of their devices in both hardware and software to help eliminate malicious access to the network and significantly improve the CSP’s security posture.
To understand how we do this, let’s go over the basic security building blocks included in the NCS 500 platforms (as well as others) that enable us to deliver the following aspects of trustworthy platforms:
◉ Hardware integrity
◉ Boot integrity
◉ Runtime integrity
◉ Operational visibility of your trustworthy network
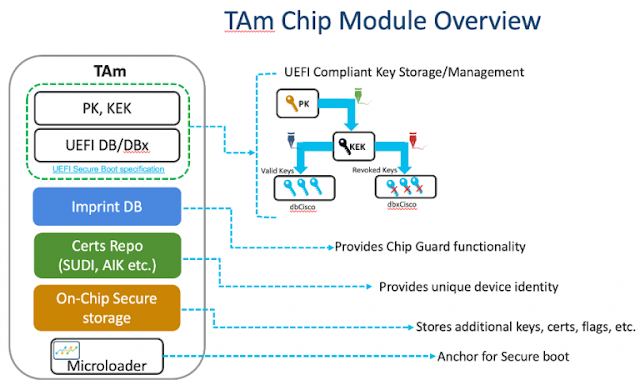
Root of Trust in Hardware
Incorporating the latest software security features is immaterial unless the underlying hardware itself is trustworthy. To provide this strong foundation of Trust, the Cisco NCS 540 and NCS 560 routers incorporate a tamper-resistant Trust Anchor module. This acts to protect the entire Secure boot process from components to operating system loading and establishing a chain of trust.
Measuring & Verifying Trust
Trust at Runtime
Tuesday, 20 April 2021
Cisco DNA Center smooths network operations
As we plan for a safe return to Cisco offices around the world, we are experiencing a large increase in the types and numbers of devices connecting to our network. This means that our teams need to manage an increasingly complex ecosystem more efficiently than ever before.
Like many IT departments, we are scrambling to keep up with these new network demands. In fact, according to one recent study of various enterprises, 43 percent of surveyed IT and network professionals said they struggle to find time to work on strategic business initiatives, and 42 percent spend too much time troubleshooting the network.
Read More: 300-425: Designing Cisco Enterprise Wireless Networks (ENWLSD)
As a result, many IT teams lack the time needed both to grow their networks and take on new projects that could set their companies apart from the competition.
To help address these challenges, our Customer Zero team, a part of Cisco IT, deployed the Cisco DNA Center controller as part of a multi-site initiative to better automate and maintain our campus and branch networks.
Cisco DNA Center delivers centralized command and control
With the Cisco DNA Center, we can take charge of our network, optimize our network investments, and respond to changes and challenges faster and more intelligently than we could before.
Cisco DNA Center provides a real-time dashboard for managing and controlling our enterprise network. It also automates provisioning and change management, checks compliance against policies, and captures asset logs that can be analyzed for troubleshooting, problem resolution, and predictive maintenance.
Assuring optimal network performance
Cisco DNA Center’s Assurance capabilities allows us to quantify network availability and risk based on analytics. It accomplishes this by enabling every point on the network to become a sensor. Cisco DNA Center collects data from 17 different network sources – including NetFlow, SNMP, syslog, streaming telemetry, and more – so that we can view network issues from many different angles and contexts. It sends continuous streaming telemetry on application performance and user connectivity in real time, then uses artificial intelligence (AI) and machine learning to make sense of the data.
Cisco DNA Center’s clean, simple dashboards show overall network status and flag issues. In addition, guided remediation automates the process of issue resolution and performance enhancement, ensuring optimal network user experiences and less troubleshooting. It allows us to resolve network issues in minutes instead of hours — before they become problems. Cisco DNA Center even lets us go back in time to see the cause of a network issue, instead of trying to re-create the issue in a lab.
How Cisco DNA Assurance operates
Making an impact for Customer Zero
Real-world use case: network changes with software upgrades
Sunday, 18 April 2021
Bring Your Broadband Network Gateways into the Cloud
With average fixed broadband speeds projected to peak up to 110+ Mbps and the number of devices connected to IP networks ballooning to 29+ billion (more than three times the global population by 2023), Internet growth remains unabated and could even be stronger as the ongoing pandemic makes the internet more critical than ever to our daily lives, defining a new normal for humanity – video conferences replaced physical meetings, virtual “happy hours” with coworkers and friends replaced get-togethers, and online classrooms have immersed children in new methods of learning.
Shouldering the weight of these new digital experiences, communication service providers are experiencing a significant increase in traffic as well as a change in traffic patterns while struggling with average revenue per user (ARPU) trending flat to down. They need to reimagine their network architectures to deliver wireline services in a more cost-efficient manner. With the average revenue per user (ARPU) flat or declining, network architectures must evolve to deliver cost-efficient wireline services.
Responsible for critical subscriber management functions and a key component of any wireline services’ architecture, the broadband network gateway (BNG) has historically been placed at centralized edge locations. Unfortunately, these locations don’t provide the best balance between the user plane and the control plane’s performance requirements. The user plane (also known as the forwarding plane) scale is tied to the bandwidth per subscriber, while the control plane scale depends on the number of subscriber sessions and services provided for end-users. In most situations what happens is that either the control plane or the user plane ends up being either over or underutilized.
For years, the limited number of services per end-user and moderate bandwidth per user allowed network designers to roll out BNG devices that supported both user plane and control plane on the same device because minimal optimization was required. But today, with the exponential growth in traffic, subscribers, and services fueled by consumers’ appetite for new digital experiences, the traditional BNG architecture facing some severe limitations.
Given the changing needs and requirements, it is no longer possible to optimize the user plane and control plane when hosted on the same device. And it’s not scalable, making it difficult to support bandwidth or customer growth, control costs, and manage complexity with more and more BNG deployments. It is time to entirely rethink the BNG architecture.
Cloud Native Broadband Network Gateway
To overcome these operational challenges and right-size the economics, Cisco has developed a cloud native BNG (cnBNG) with control and user plane separation (CUPS) – an important architectural shift to enable a more agile, scalable, and cost-efficient network.
This new architecture simplifies network operations and enables independent location, scaling, and life cycle management of the control plane and the user plane. With the CUPS architecture, the control plane can be placed in a centralized data center, scaled as needed, and it can manage multiple user plane instances. Cloud native control planes provide agility and speed up the introduction of new service introduction using advanced automation. Communication Service Providers (CSPs) can now roll out leaner user plane instances (without control plane related subscriber management functions) closer to end-users, guaranteeing latency, and avoiding the unnecessary and costly transport of bandwidth-hungry services over core networks, Thereby, they can place Content Distribution Network (CDN’s) deeper into the network, enabling peering offload at the edge of the network hence delivering a better end-user experience.
There are also other benefits. A cloud native infrastructure provides cost-effective redundancy models that prevent cnBNG outages, minimizing the impact on broadband users. And, a cloud-native control plane lets communication service providers adopt continuous integration of new features, without impacting the user plane which remains isolated from these changes. As a result, operations are eased, thanks to a centralized control plane with well-defined APIs to facilitate the insertion into OSS/BSS systems.
When compared to a conventional BNG architecture, Cisco cloud native BNG architecture brings significant benefits:
1. A clean slate Fixed Mobile Convergence (FMC) ready architecture as the control plane is built from the ground-up with cloud-native tenets, integrating the subscriber management infrastructure components across domains (wireless, wireline, and cable)2. Multiple levels of redundancy both at the user plane and control plane level
3. Optimized user plane choices for different deployment models at pre-aggregation and aggregation layers for converged services
4. Investment protection as an existing physical BNG can be used as user planes for cnBNG
5. Granular subscriber visibility using streaming telemetry and mass-scale automation, thanks to extensive Yang models and KPIs streamed via telemetry, enabling real-time API interaction with back-end systems
6. A Pay-as-you-grow model allows customers to purchase the user planes network capacity, as needed
Analysis has shown that these benefits translate into up to 55% Total Cost of Ownership (TCO) savings.
An Architecture Aligned to Standards
This past June, the Broadband Forum published a technical report on Control and User Plane Separation for a disaggregated BNG – the TR-459 – that notably defines the interfaces and the requirements for both control and user planes. Three CUPS interfaces are defined – the State Control Interface (SCi), the Control Packet Redirect Interface (CPRi), and the Management Interface (Mi).
With convergence in mind, the Broadband Forum has selected the Packet Forwarding Control Protocol (PFCP) defined by 3GPP for CUPS as the SCi protocol. It is a well-established protocol especially for subscriber management. Whereas the TR-459 is not yet fully mature, Cisco’s current cnBNG implementation is already aligned to it.
On the Road to Full Convergence
Historically, wireline, wireless, and cable subscriber management solutions have been deployed as siloed, centralized monolithic systems. Now, a common, cloud-native control plane can work with wireline, wireless, and cable access user planes paving the way to a universal, 5G core, converged subscriber management solution capable of delivering hybrid services. And Network Functions (NF’s) that are part of the common cloud-native control plane, not only share the subscriber management infrastructure, they also provide a consistent interface for policy management, automation, and service assurance systems.
Read More: 500-450: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)
Moving forward, CSPs can envision a complete convergence of policy layer and other north-bound systems, all the way up to the communication service provider’s IT systems.
With a converged model in place, customers can consume services and applications from the access technology of their choice, with a consistent experience. And communication service providers can pivot to a model with unified support services, and monitoring/activation systems, while creating sticky service bundles, as more end-user devices are tied to a single service, increasing customer retention.
Cisco is uniquely positioned to help customers embrace this new architecture with a strong end-to-end ecosystem of converged subscriber management across mobile, wireline, and cable, in addition to, a fully integrated telco cloud stack across compute, storage, software defined fabric, and cloud automation.
Source: cisco.com
Saturday, 17 April 2021
100-490 RSTECH Free Exam Questions & Answers | CCT Routing and Switching Exam Syllabus
Cisco RSTECH Exam Description:
The Supporting Cisco Routing and Switching Network Devices v3.0 (RSTECH 100-490) is a 90-minute, 60-70 question exam associated with Cisco Certified Technician Routing and Switching certification. The course, Supporting Cisco Routing and Switching Network Devices v3.0, helps candidates prepare for this exam.
Cisco 100-490 Exam Overview:
- Exam Name:- Supporting Cisco Routing and Switching Network Devices
- Exam Number:- 100-490 RSTECH
- Exam Price:- $125 USD
- Duration:- 90 minutes
- Number of Questions:- 55-65
- Passing Score:- Variable (750-850 / 1000 Approx.)
- Recommended Training:- Supporting Cisco Routing and Switching Network Devices (RSTECH) v3.0
- Exam Registration:- PEARSON VUE
- Sample Questions:- Cisco 100-490 Sample Questions
- Practice Exam:- Cisco Certified Technician Routing & Switching Practice Test
Your workforce is ready – but is your workplace?
We’re heading back to the office!!
It won’t happen overnight – but the signs are increasingly positive that we are on our way back. Some companies, like Cisco and Google, have begun encouraging a phased return to the office, once the situation permits. Personally, I can’t wait to be in the same physical space as my colleagues, as well as meeting our customers face-to-face.
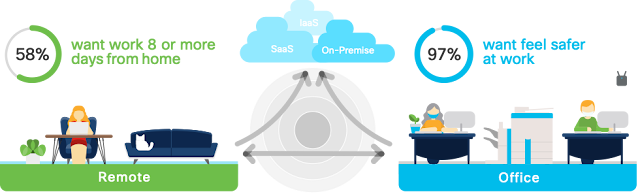
Like most of you, I desire the flexibility to choose where I work. Based on our recent global workforce survey, only 9% expect to be in the office 100% of the time. That means IT will need to deliver a consistently secure and engaging experience across both in-office and remote work environments.