Visibility is a key to success across a wide range of disciplines. If you’re a basketball fan like me, you know that visibility is important when a player makes an alley-oop pass to his teammate in an NBA game. It’s even more important for high-risk operations like landing an aircraft in the fog. Now imagine how essential visibility is for securing a manufacturing site.
When you can’t see what’s happening on your network, keeping your manufacturing site secure and addressing today’s threat detection landscape can be difficult-to-impossible. Visibility into your IT and your operational technology (OT) assets helps to answer these critical questions:
◉ What assets are on your network? What is their level of criticality?
◉ Which assets communicate with other assets and what are they saying?
◉ Which assets are vulnerable and need extra attention?
Essentially, manufacturers need enhanced visibility to see things before they happen, swiftly respond during events and access ongoing insights regarding the state of their environment. Unfortunately, many manufacturers today lack visibility into the assets on their industrial network.
This lack of visibility may severely impact the implementation of cybersecurity best practices and risk mitigation plans.
Visibility Matters
Enhanced visibility includes:
◉ Asset inventory and vulnerability management
◉ Network segmentation to limit threat spreading
◉ Critical event tracking
◉ Focusing threat detection on where it matters
According to a Forrester Study, 55 percent of industrial organizations have little or no confidence that they know what devices exist in their industrial network. In addition, 76 percent of manufacturers believe their current security practices may be inadequate. Many do not believe they could contain, eradicate, and recover from a breach.
This cybersecurity risk expands as industrial systems become further connected, for instance as companies employ digital transformation. For example, 66 percent1 of manufacturers have already experienced a cybersecurity security incident impacting their industrial control systems (ICS). Anyone watching the nightly news can see that there is a growing number of cybersecurity attacks occurring in critical infrastructure.
Unfortunately, manufacturers are getting breached because appropriate cybersecurity practices are not in place. For some, this results from the expansion of manufacturing systems over the years through acquisitions, causing several legacy systems to populate the plant floor. For others, the loss of knowledge as experienced workers leave can contribute to cybersecurity vulnerability. Not to mention the trend toward companies employing remote workers, and facilities now being connected to their supply chains and no longer isolated, only add to the threat surface.
Chuck Robbins, Cisco CEO, during his RSAC 2021 keynote put the risk this way: “If we think about cybercrime like we think about the GDP of companies, it would be the third largest economy in the world after the US and China with $6 trillion in global damages. And we all know the real cost is not being able to run our businesses or the reputational damage that you suffer and the impact on your organization in the future.”
Put simply, how can you secure an environment if you don’t know what’s connected? Gaining visibility is key to building and maintaining a detailed asset inventory, managing vulnerabilities, and segmenting networks to limit threat spreading. Visibility also lets you focus threat detection where it really matters so that you can track critical events before it’s too late.
Leaders in IT and OT security work together help to enhance your visibility
Cisco – a global leader in industrial networking and security – and Rockwell Automation – a global leader in industrial control, power and information systems – continue to combine forces to lead digital transformation for The Connected Enterprise. And now, Rockwell Automation is expanding its threat detection services offerings by adding Cisco Cyber Vision to its portfolio.
“We are excited to continue growing our strategic alliance offerings with Cisco,” said Angela Rapko, director, Portfolio & Business Management–Customer Support and Maintenance (CSM), Rockwell Automation. “The addition of Cisco Cyber Vision to our cybersecurity threat detection services portfolio benefits our customers by expanding the integration between the Rockwell Automation and Cisco ecosystems, particularly around cybersecurity.”
Proactive approach to industrial cybersecurity
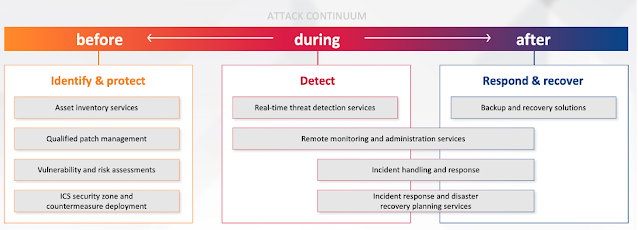
To help industrial customers improve their security postures, Rockwell Automation offers a portfolio of world-class industrial cybersecurity services (Figure 1). These services follow the NIST Cybersecurity Framework. At a high level, they help customers build a more secure, robust, future-ready network for their connected enterprises by providing assessment, design, implementation, and monitoring solutions.
Figure 1: Rockwell Automation cybersecurity framework
By leveraging Rockwell services to implement Cisco solutions, our customers can realize ‘best of both world’ benefits. The OT domain expertise from Rockwell helps to improve security posture in the manufacturing environment while mitigating potential risks to production. In parallel, leveraging Cisco solutions in the OT space provides for maximized integration into existing Cisco based infrastructure on the IT side, making it easier for IT to manage and maximize investments relative to a holistic Enterprise approach to security.
Rockwell Automation uses Cisco Cyber Vision to deliver improved visibility
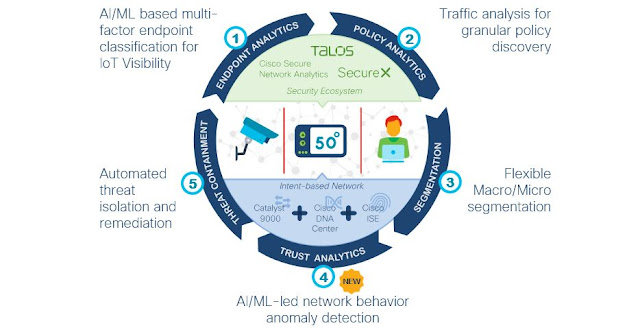
To help improve customers’ visibility into their networks, Rockwell Automation has added Cyber Vision as part of its visibility and threat detection services portfolio. Cisco Cyber Vision helps customers maintain the integrity of their plant assets and protect them against cybersecurity threats as part of an overall cybersecurity threat defense. Cyber Vision provides full visibility into industrial control systems including identifying device vulnerabilities, tracking critical events, detecting abnormal behaviors as well as cyber threats. It feeds IT security tools with all this OT context to easily build security policies and accelerate incident response. Whether you are a Rockwell customer, a Cisco customer or a joint customer of ours already, you can benefit from these new solutions and services.
By providing full visibility, Cisco Cyber Vision helps customers build zones and conduits by:
◉ Automatically discovering all the assets connected on a network, as well as the logical relationships between them
◉ Enabling OT users to group assets based on knowledge of the underlying process and overall security requirements
◉ Aggregating traffic flows into conduits, which then receive segmentation policies

By improving visibility, Cisco Cyber Vision also helps customers to detect threat vectors by identifying behavioral changes within the communication patterns on the network.
Improved visibility helps OT, IT, and Security Operations (CISO) work better together:
◉ OT keeps production going and improves uptime.
◉ IT implements cybersecurity best practices.
◉ CISO builds and enforces OT security policies without disrupting production.
Finally, improved visibility helps to establish a more collaborative workflow between IT and OT, creating a more common ground for them to work together and collaborate. IT and OT work on the same representation of the industrial network but from different points of view:
◉ From a network hygiene viewpoint, IT provides cybersecurity best practices and a perspective on threat detection.
◉ With its knowledge of the industrial process, OT understands which assets are the most critical and whether or not a particular event represents a threat within a certain context
In short, IT, OT, and CISO must work together to deliver enhanced security through visibility. Just like two basketball players executing an alley-oop pass, improved visibility is a key to enabling their successful collaboration.
Source: cisco.com