Orchestrate your multi-fabric and multicloud network simply
In any symphony you need a good maestro to help orchestrate all the different instruments to produce a harmonious sound. Everything must be in time and to the beat. It is the same with your networks. When running multiple fabrics both on premise, private clouds or public clouds, you need a maestro or orchestrator as well that can be automated and help manage the network and security policies across vast landscapes.
Since it’s early days, Cisco’s Nexus Dashboard Orchestrator (NDO) has been that maestro, allowing network administrators, engineers and cloud operators work together harmoniously to provide a fast, safe and agile network. We have new versions of NDO, release 3.5 and release 3.6 which will help you build your network capabilities, provide greater ease of use and enhance your security across multiple network fabrics.
What is Cisco NDO
NDO provides consistent network and policy orchestration, scalability, and disaster recovery across multiple data centers through a single pane of glass while allowing the data center to go wherever the data is.
NDO allows you to interconnect separate Cisco® Application Centric Infrastructure (Cisco ACI®) sites, Cisco Cloud ACI sites, and Cisco Nexus Dashboard Fabric Controller (NDFC) sites, each managed by its own controller (APIC cluster, NDFC cluster, or Cloud APIC instances in a public cloud). The on-premises sites can be extended to different public clouds for hybrid-cloud deployments while cloud-first installations can be extended to multi-cloud deployments without on-premises sites. In addition, Nexus Dashboard Orchestrator can be deployed through the Cisco Nexus® Dashboard, which provides a single automation platform to access the data center network’s operational services and tools.
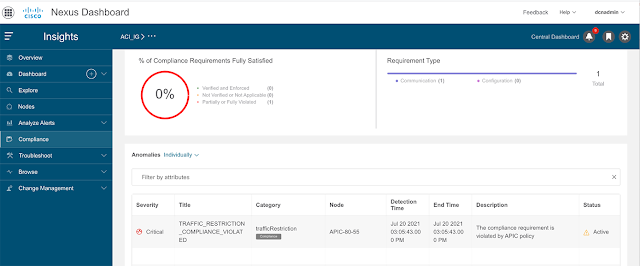
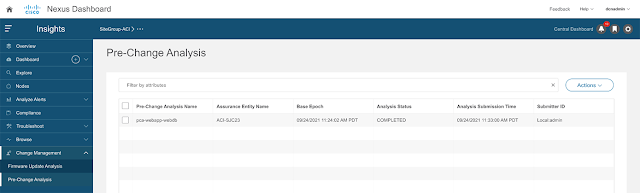
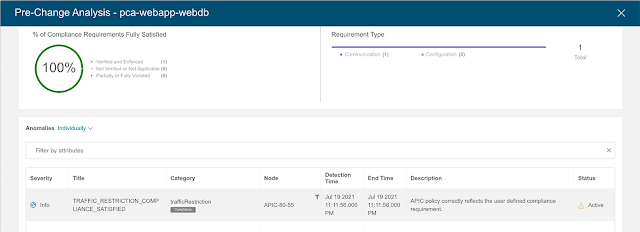
The single-pane network interconnect policy management and the consistent network workload and segmentation policy provided by NDO allows monitoring the health of the interconnected fabrics, enforcement of segmentation and security policies, and performance of all tasks required to define tenant intersite policies in multiple sites through an easy to manage user interface.
What’s New?
- BGP for underlay peering with ISN –
- This provides support peering spines with the ISN devices using BGP adjacencies. It simplifies ISN connectivity using BGP only.
- External connectivity from Cloud Sites
- This allows you to establish external connectivity between Cloud CSRs and external devices with IPsec & BGP, which provides access to cloud resources from external networks (Branch, Campus, Co-lo, Internet)
- Show DCNM object fault info from all sites
- Scalability improvement of 12 DCNM sites
- Configuration drift reconciliation workflow for APIC and NDFC provides:
- NDO workflow that synchronizes and merges any policy config discrepancies/changes made in APIC or NDFC level.
- Ease of Use Improvements
- Scalable static port binding with leaf/port range provisioning
- Bulk update workflow for template objects
- NDO Cloud Enhancements allows:
- Google Cloud connectivity
- Multi-cloud inter-site connectivity between AWS, Azure, and Google Cloud Sites
- Partial mesh EVPN-VXLAN connectivity between on premises and AWS and Azure cloud sites
- Workload connectivity for multicloud without policy
- Proxy support for cloud sites
- SD-Access Campus (DNAC) and ACI Integration – Macro-Segmentation includes automating:
- Connectivity of Campus VN to access DC VRF
- Internet access for Campus VNs through ACI
- Visibility of VN-VRF extension and connectivity status
- NDFC 12.0(2) support