When people think of fleets, they often think of a collection of ships cruising across the sea. Modern-day fleets, however, include public transportation, first responders, and service trucks for utilities, ISPs, and equipment or appliance repair. Gone are the days when fleet activities were solely managed by two-way radio voice communication from a dispatcher. In the last 20 years, fleets have been reinvented to digitally connect over wide area networks (WANs) while on the move and sending and receiving important information in real-time enabling them to operate efficiently and reliably. Modern fleets share the need for reliable and available communications, security, and visibility.
Communication, Reliability, and Visibility
Whether we are talking about public transportation moving thousands of citizens across the city, first responders racing to the scene of an accident, or service fleets responding to power outages – fleet deployments have a definitive need for secure, reliable network connectivity with high availability that will relay business information in real-time and through the best transport possible in order to maintain operational availability and contain costs.
Consider the impact of a city bus losing connectivity to computer-aided dispatch and missing route updates or a first responder being unable to access the location of an accident scene. These kinds of scenarios emphasize the criticality of that connectivity being both reliable and available. Just like office applications, these fleet solutions require always-on, reliable WAN connectivity to perform their functions while in motion and while they are wirelessly connected.
Security as the Backbone of Fleet Management
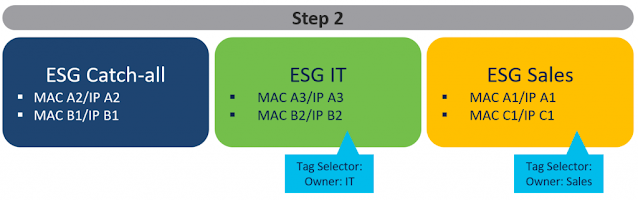
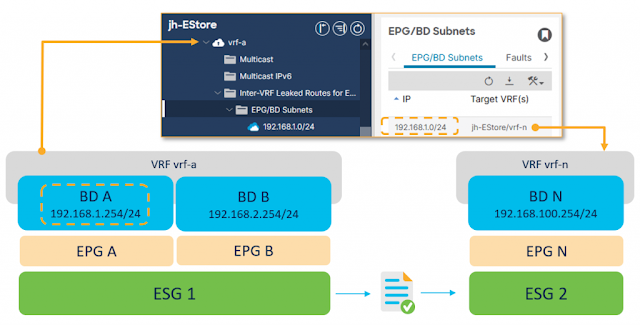
Segmentation is critical. Take a city bus for example – several applications are running simultaneously across payment services, predictive maintenance, passenger services, and video analytics. Each requires controlled access so that only the intended persona can access data associated with each service. Using these examples, you’d want only the payment processing company seeing payment information, the maintenance department seeing predictive maintenance data, and security forces seeing video footage. This segmentation enabled by virtual routing and forwarding (VRF) capabilities provides peace of mind for those on the security side while simplifying the day-to-day life for those on the operations side.
Credentialed access to enterprise networks is also important for service fleets that run applications accessing inventory databases, work order management systems, and even payment systems that are hosted in the enterprise core network. Identity-based security policies on Cisco SD-WAN help ensure that access to sensitive information is automated and scalable to keep the right eyes on the right data.
Data encryption is critical for first responders, particularly ambulances, due to the additional consideration of patient information. Privacy is necessary to comply with HIPPA guidelines so stricter measures may need to be taken to ensure the data is secure. Cisco SD-WAN provides peace of mind when it comes to the handling of sensitive information as 2048-bit encryption keys, and underlying traffic encrypted using the AES-256 cipher come standard for devices connected through your routers.
Operational Efficiency – The Brass Ring
While all fleet categories require reliable and available connectivity as well as security, transit systems, and service fleets are also greatly concerned about operational efficiency. The fact is that most public transit systems operate at a loss and are publicly funded, bringing immense pressure to reduce costs. Service fleets, while typically funded by private industry, are ever vigilant about controlling costs and reducing service call count and duration. Both have the need for automation, consolidation, visibility, and managing airtime costs.
Cisco SD-WAN is the Answer
Cisco SD-WAN provides fleet operators with the ability to connect and monitor their fleet vehicles and automate processes while also providing needed visibility, security, and consolidation with the enterprise network.
The ruggedized industrial routers in the Cisco Catalyst IR Series come SD-WAN ready to meet vehicle environmental conditions. These routers provide reliable and available connectivity through multiple means of transport ranging from 5G and LTE to broadband, Wi-Fi, and even satellite. Cisco SD-WAN also offers configurable failovers between transports to ensure continuous communication. The brain of Cisco SD-WAN, vSmart, can automatically route business critical traffic over high bandwidth links and send lower priority traffic over lower cost links, while the vManage dashboard lets you see it all in real-time.
Cisco SD-WAN comes standard with a host of security functions that ensure your fleet vehicles and their applications are protected at the same level as the enterprise. By creating template-based policies, onboarding new devices come with ease and helps bridge together your IT and OT teams as well. The main security benefits of using Cisco SD-WAN for fleet management come from:
◉ End-to-end segmentation that isolates and protects critical information.
◉ Encrypted IPsec tunnels for data privacy.
◉ Identity-based policy management for both enterprise and industrial networks.
◉ Utilizing Cisco Umbrella for protection against internet-based threats.
◉ Security features running directly on the router, including embedded enterprise firewall, IPS, and URL filtering capabilities.
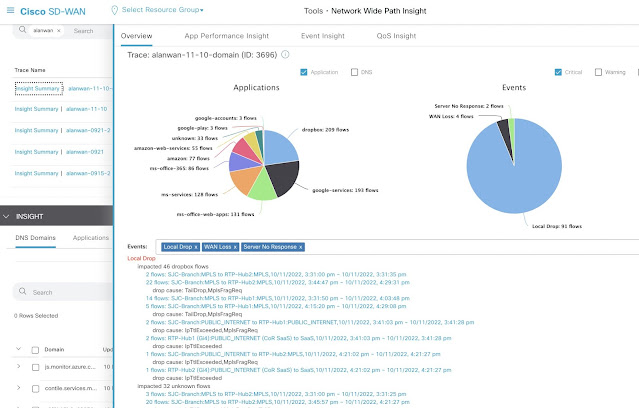
Cisco SD-WAN provides end-to-end visibility for every application and device across the entire SD-WAN fabric. Between the IoT devices powering your fleet, cloud-native applications used in the office, and every device your employees touch – Cisco SD-WAN provides a consolidated console that is guaranteed to simplify your IT operations. Reliability, availability, security, and visibility are all provided to ensure that your enterprise and fleet vehicles are optimized and protected in any scenario.
Source: cisco.com