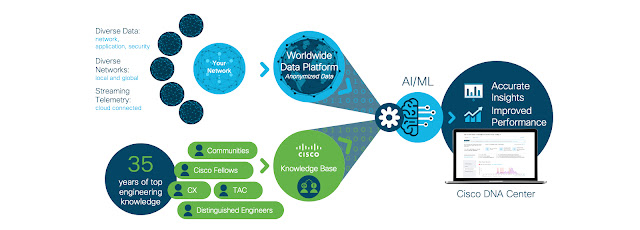
Thursday, 18 May 2023
Forrester TEI™ Finds Cisco Vulnerability Management Delivers 125% ROI
Tuesday, 16 May 2023
IT Leaders Contend with Secure Multicloud Access – The 2023 Global Networking Trends Report
Use of Multiple Clouds is on the Rise
Lack of Operational Consistency is an Obstacle
Integrate Networking and Security from Device to Cloud
Simplify Connectivity to Multiple Clouds
You Can’t Manage What You Can’t See
Saturday, 13 May 2023
Future-proof with Cisco Next-Gen Firewalls
Foundation of Futureproofing
Cisco’s Future-proof Security Platform
Security Architecture Extension
World-class Security Controls
Unified Policy and Threat Visibility
Tackling new opportunities
Thursday, 11 May 2023
Spend Less Time Managing the Network, More Time Innovating with the Network
Automating Compliance Checks
Simplifying Device Maintenance
Moving From Reactive to Preventative
Optimizing the Network Fabric for Application Performance
Simplify Networks with a Foundation of Automation and Analytics
Wednesday, 10 May 2023
How to Pass Cisco 300-420 ENSLD Exam Using Various Study Materials?
Getting certified by Cisco is the recommended path to establishing a career in Cisco products. Countless companies, regardless of their size, rely on Cisco’s network software and equipment. It’s evident that Cisco’s products surpass those of their competitors because they continuously enhance and add new features to their technologies. If your career goal is to work in enterprise design, passing the Cisco 300-420 ENSLD exam will significantly benefit you and give you a significant advantage when job hunting.
Cisco 300-420 ENLSD Exam Overview
To obtain the new CCNP certification, you must pass two tests, one of which is the Cisco 300-420 ENSLD. This exam is a concentration test chosen from a pool of six others. It is mandatory to take the 300-420 exam and the core Cisco 350-401 test to be eligible for the certification. The 300-420 exam encompasses diverse topics that students must be familiar with before attempting. These objectives include:
These topics are intended to aid in your exam preparation, consisting of 55-65 questions and last 90 minutes. Once you grasp these topics well, you will be well-prepared to take the Cisco 300-420 exam and pass it successfully.
Best Study Resources for CCNP Enterprise 300-420 ENSLD Exam
You must have the right study resources to prepare for the CCNP Enterprise 300-420 ENSLD exam. Here are some of the best resources that you can use:
1. Official Cisco Learning Resources
The official Cisco Learning Resources is a great place to start your preparation for the CCNP Enterprise 300-420 ENSLD exam. Cisco offers a range of training courses, study materials, and practice tests that can help you learn the exam topics and get hands-on experience with Cisco technologies and solutions. You can find these resources on the Cisco website or through Cisco’s authorized learning partners.
2. CCNP Enterprise 300-420 ENSLD Study Guide
The CCNP Enterprise 300-420 ENSLD Study Guide is a comprehensive resource covering all the exam blueprint topics. The guide includes detailed explanations, examples, and practice exercises to help you understand the exam concepts and prepare for the test. You can find the study guide on Amazon or other online bookstores.
3. Cisco 300-420 ENSLD Practice Tests
Practice tests are essential to your preparation for the CCNP Enterprise 300-420 ENSLD exam. They help you identify your strengths and weaknesses, get familiar with the exam format and time constraints, and build your confidence for the test. You can find practice tests on the Cisco website, through Cisco’s authorized learning partners, or on online learning platforms such as nwexam website.
Tips for Passing CCNP Enterprise 300-420 ENSLD Exam
Here are some tips that can help you pass the CCNP Enterprise 300-420 ENSLD exam:
1. Understand the Exam Blueprint
The CCNP Enterprise 300-420 ENSLD exam blueprint outlines the topics and subtopics the exam covers. Ensure you understand the blueprint and focus your study efforts on the areas you need to improve.
2. Get Hands-on Experience
The CCNP Enterprise 300-420 ENSLD exam tests your ability to design enterprise networks using Cisco technologies and solutions. You must have hands-on experience with Cisco devices and software to prepare for the exam. Set up a lab environment or use simulation tools for the necessary expertise.
3. Join Study Groups
Joining study groups can help you stay motivated and learn from other candidates preparing for the CCNP Enterprise 300- 420 ENSLD exam. You can find study groups on social media platforms like LinkedIn, Facebook, or Reddit.
4. Use Mind Mapping and Note-taking Techniques
Mind mapping and note-taking techniques can help you organize your thoughts, understand complex topics, and remember important concepts. Use these techniques to create summaries, diagrams, and charts that capture the exam topics and subtopics.
5. Practice Time Management
The CCNP Enterprise 300-420 ENSLD exam lasts for 90 minutes, which means you have limited time to answer 60-70 questions. Practice time management techniques, such as skipping difficult questions and returning to them later, to ensure you answer all the questions within the allotted time.
Conclusion
The CCNP Enterprise 300-420 ENSLD exam is a challenging test requiring extensive knowledge and experience designing enterprise networks using Cisco technologies and solutions. To prepare for the exam, you must have the right study resources, such as official Cisco learning resources, study guides, and practice tests. Additionally, you need to follow some tips, such as understanding the exam blueprint, getting hands-on experience, joining study groups, using mind mapping and note-taking techniques, and practicing time management. With the proper preparation and dedication, you can pass the CCNP Enterprise 300-420 ENSLD exam and advance your career in the networking field.