Saturday, 30 March 2024
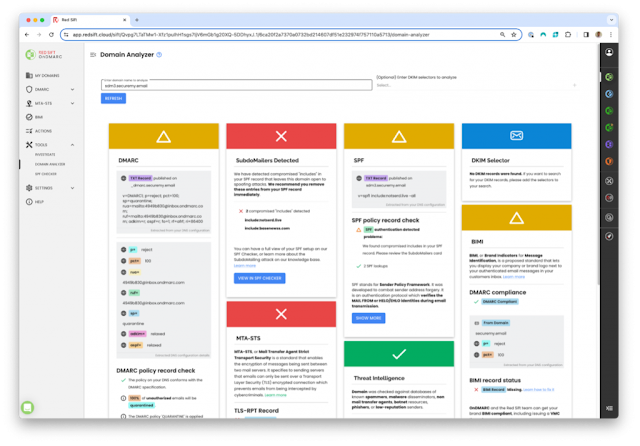
Hiding in Plain Sight: How Subdomain Attacks Use Your Email Authentication Against You
Thursday, 28 March 2024
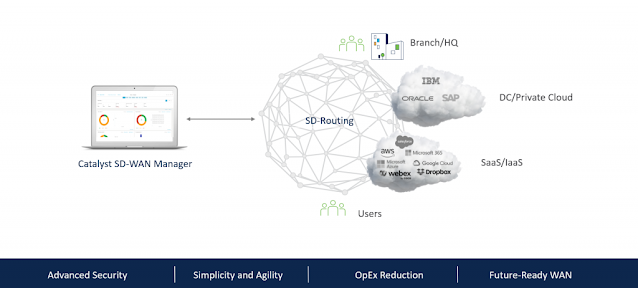
SD-Routing: Unlock Agility and Efficiency for the Secure WAN Edge
- Unify management: Manage device software upgrades, monitoring, and troubleshooting through the intuitive Catalyst SD-WAN Manager dashboard. This simplifies network operations and empowers you to manage both traditional routing and Catalyst SD-WAN environments.
- Tame legacy challenges: Simplify complex legacy operations with SD-Routing. Basic troubleshooting tools within the manager help you maintain and optimize performance. Continuous updates ensure your network stays ahead of the curve.
- Combat configuration drift: Manage and track changes with a unified platform. Use the manager to create configuration templates for standardized deployments and future SD-WAN migration.
Security
Cloud on-ramp for multicloud
Tuesday, 26 March 2024
GenAI will Transform B2B Interactions and Solutions in the Year Ahead with New Depth of Context and Control
Additional B2B considerations with GenAI
Moving fast towards contextual understanding and reasoning
Saturday, 23 March 2024
Increase Market Share Quickly with Cisco Specializations and GTM Tools
- Differentiate yourself from your competition by earning more Cisco Powered Services Specializations and pave your way to Gold-level advantages.
- Use your market development funds for business development, demand generation, funding headcount, and internal training.
- Leverage ready-made marketing kits and templates and get access to experts to help you grow your business.
- Earn greater pricing incentives and discounts that help you reach your revenue goals faster. Cisco continuously updates and adds marketing resources, so you can maximize your earning potential as your sales grow.
Growth drivers
Greater Together
Create marketplace differentiation with Cisco
- Proven blueprints: Validate your competency in areas including Power Hybrid Work, Secure the Enterprise, Transform Infrastructure, and Reimagine Applications.
- Quicker path to advancement: Meet specialization training requirements with up to 40 percent cost reductions. Role-share using CCIEs and CCNPs helps you meet Provider-level requirements faster.
- Showcase capabilities: Once you achieve these specializations, you gain access to industry-recognized logos and exclusive go-to-market resources to build successful solutions and services for Managed SD-WAN, Meraki, SASE, FSO, and many more.
- Sales acceleration: Expand your Cisco Powered Services portfolio and earn greater rewards within the Provider role, including exclusive upfront discounts and market development funds.
New resources available
Thursday, 21 March 2024
Transforming the Economics of Superfast Broadband with Cisco Routed PON
Why can’t we just keep doing things the old way?
What sets Routed PON apart?
Flexibility, service differentiation, and investment protection
Tuesday, 19 March 2024
Complexity drives more than security risk. Secure Access can help with that too.
Provide a strong user experience and troubleshoot performance issues
- Devices, such as laptops
- Wi-Fi networks
- Internet service providers
- Corporate resources, such as VPNs or security tools
- Applications
- Device – detailed user and system information, including CPU and memory utilization and Wi-Fi signal strength.
- Internet and network paths – key metrics regarding the network path from the device to the Secure Access gateway, including latency, packet loss, and jitter.
- Collaboration applications – automatic performance tests for key collaboration tools, such as Cisco Webex, Microsoft Teams, and Zoom.
- SaaS applications – insight into the most popular SaaS applications, including the overall health status and details such as HTTP response times and status codes.
Single-dashboard, single-agent
All at no extra cost
Experience insights is just one capability of an incredible solution
Saturday, 16 March 2024
Simplify DNS Policy Management With New Umbrella Tagging APIs
This blog post will show you how you can automate DNS policy management with Tags.
To streamline DNS policy management for roaming computers, categorize them using tags. By assigning a standard tag to a collection of roaming computers, they can be collectively addressed as a single entity during policy configuration. This approach is recommended for deployments with many roaming computers, ranging from hundreds to thousands, as it significantly simplifies and speeds up policy creation.
High-level workflow description
1. Add API Key
2. Generate OAuth 2.0 access token
3. Create tag
4. Get the list of roaming computers and identify related ‘originId’
5. Add tag to devices.
The Umbrella API provides a standard REST interface and supports the OAuth 2.0 client credentials flow. While creating the API Key, you can set the related Scope and Expire Date.
To start working with tagging, you need to create an API key with the Deployment read/write scope.
First, we need to generate an OAuth 2.0 access token.
Let’s create tag with the name “Windows 10”
The following function helps us Get the List of roaming computers:
After adding tags, let’s check the dashboard
- Each roaming computer can be configured with multiple tags
- A tag cannot be applied to a roaming computer at the time of roaming client installation.
- You cannot delete a tag. Instead, remove a tag from a roaming computer.
- Tags can be up to 40 characters long.
- You can add up to 500 devices to a tag (per request).