Tuesday, 9 April 2024
Mastering Skills with Play: The Fusion of Gaming and Learning in Black Belt Gamification
Saturday, 6 April 2024
Meet the new Cisco Catalyst 1200 and 1300 Series Switches for SMBs
Cisco Catalyst 1200 Series Switches
Cisco Catalyst 1300 Series Switches
Which one do you need?
Thursday, 4 April 2024
Balancing agility and predictability to achieve major engineering breakthroughs
- According to our 2024 Cybersecurity Readiness Index, 54% of organizations said they have experienced a cybersecurity incident in the last 12 months.
- The latest Security Outcomes Report shows preventing incidents and mitigating losses are the top priorities for security resilience overall.
A pragmatic approach to balancing agility and predictability
- Encouraging cross-functional collaboration and open dialogue about the challenges and benefits of both approaches.
- Ensuring leadership is aligned with the organization’s approach to balancing agility and predictability.
- Creating opportunities, like Hackathons, to fail fast and learn even faster, explore the art of the possible, and to dive into technology to solve unexpected challenges.
- Ensuring consistent messaging and support for team members.
- We blend agile methodologies with more traditional project management approaches (e.g., agile for new features, waterfall for foundational infrastructure). Our processes allow us to take a “dual plane” approach to innovation with one plane focusing on predictable, stable delivery while the other explores innovative, experimental initiatives.
- As the aphorism goes, “you can’t manage what you can’t measure”. We have implemented an outcome-focused approach toward metrics that shifts the focus from output (deliverables) to outcomes (business value). This allows us to demonstrate how agility enhances the ability to deliver value quickly and adapt to market changes, solving some of the toughest challenges for our customers.
- We take a customer-centric approach in all things we do. This means we use customer feedback and market insights to prioritize and guide innovation efforts. This includes dedicated customer advisory boards, and programs built around the voice of our customers like NPS surveys. This helps ensure that agility is directed toward meeting customer needs and not innovating for innovation’s sake.
Innovating to win
Tuesday, 2 April 2024
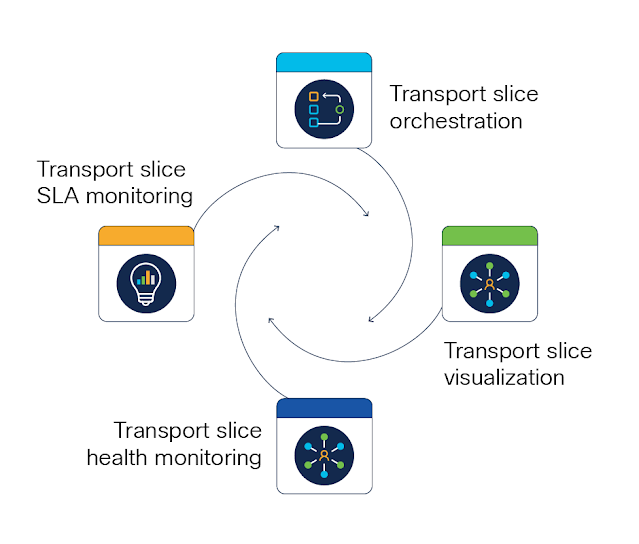
Pave the Way for New Revenue with Transport Slicing Automation and Assurance
Simplify and transform service delivery
Leverage transport slicing for the best outcomes
A complete, end-to-end automated slicing and assurance solution
Fix problems before customers notice
Monday, 1 April 2024
Mastering CCNP Security 300-740 Exam: An In-Depth Look
In the ever-evolving field of network security, standing out as an IT professional requires not just skill, but validation of that skill. The CCNP Security 300-740 certification emerges as a beacon for those dedicated to mastering Cisco networks' security. This coveted credential is more than a certificate; it's a badge of honor that signifies your prowess in deploying and managing cutting-edge security measures in the cyber world.
Diving Deep into the CCNP Security 300-740 Exam
At the heart of the CCNP Security certification lies the 300-740 exam, a rigorous test that probes your knowledge across various pivotal security domains such as secure network access, content security, and navigating the complexities of cloud security. Crafted meticulously, the 300-740 SCAZT exam ensures that those who pass can shield network infrastructures against the threats of today and tomorrow.
300-740 SCAZT Exam Breakdown:
Duration: 90 minutes
Question Count: Between 55 to 65
Passing Score: Typically falls between 750 and 850 out of 1000
Format: A mix of multiple-choice and simulation-based questions
Validity: 3 years before renewal is required
CCNP Security Exam Preparation Pathways
Official Cisco Resources: Dive into the wealth of knowledge provided through Cisco's own training courses. These not only cover the theoretical aspects but also offer practical lab exercises.
Comprehensive Study Guides: Bolster your preparation with detailed study materials that go in-depth into each 300-740 exam topic.
Practice Makes Perfect: Regular practice exams are invaluable. They pinpoint areas needing improvement and familiarize you with the Cisco SCAZT exam's structure and pacing.
Community Engagement: Connect with peers through forums and study groups. Sharing insights and experiences can provide unique perspectives and study tips.
Best Tips to 300-740 Triumph
Know What's Expected: Thoroughly understanding the 300-740 SCAZT exam objectives can give you a clear roadmap of what to study.
Strategic Study Plan: Allocate your study time wisely, ensuring each topic gets the attention it deserves, with regular reviews.
Real-World Application: There's no substitute for hands-on experience. Create a lab environment to practice real-world security scenarios on Cisco networks.
Stay Informed: The cybersecurity landscape is dynamic. Keep abreast of the latest trends and technologies that could be included in the CCNP Security exam.
Career Advancement Post-Certification
Earning the CCNP Security 300-740 certification can significantly propel your career forward, marking you as a seasoned professional ready to tackle complex security challenges. Career doors that may open include roles as a Network Security Engineer, Security Analyst, Cybersecurity Specialist, or Network Administrator with a security focus.
Benefits of Being CCNP Security Certified:
Industry Credibility: CCNP Security certification is a gold standard in IT, highlighting your expertise in Cisco's security solutions.
Career Growth: It paves the way for advanced roles, showcasing your dedication to professional growth and security mastery.
Skill Enhancement: Preparing for the 300-740 SCAZT exam deepens your understanding of network security, from principles to best practices.
Salary Upside: Certified professionals often enjoy higher salaries and better job prospects.
Global Recognition: Cisco's certifications are acknowledged worldwide, opening international career opportunities.
Considering the Challenges:
Investment Required: Achieving certification comes with its costs, including exam fees and study materials.
Time Management: The extensive study required demands a significant time commitment.
Keeping Pace with Technology: As security technologies evolve, so must your knowledge, necessitating continuous learning.
Exam Rigor: The CCNP Security exam's challenging nature demands a solid grasp of complex concepts and hands-on experience.
Specialization: While highly valuable for those in network security, it might not offer the same benefits for individuals in non-Cisco environments or different IT areas.
Conclusion
The journey towards obtaining the CCNP Security 300-740 certification requires dedication, consistent studying, and practical application. It is a path that not only enhances your professional life but also distinguishes you as an expert in the vital field of network security. By embracing the challenge and making the most of the resources available, you can unlock a new realm of career opportunities and personal growth in the IT security domain.
Saturday, 30 March 2024
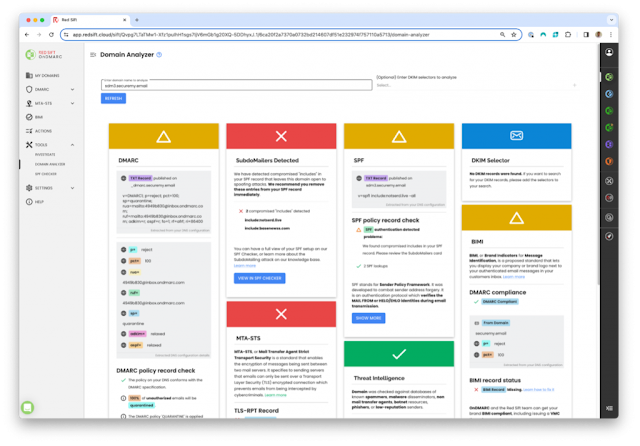
Hiding in Plain Sight: How Subdomain Attacks Use Your Email Authentication Against You
What’s happened?
What should I look out for?
Proactive steps to start today:
What else should I do?
Thursday, 28 March 2024
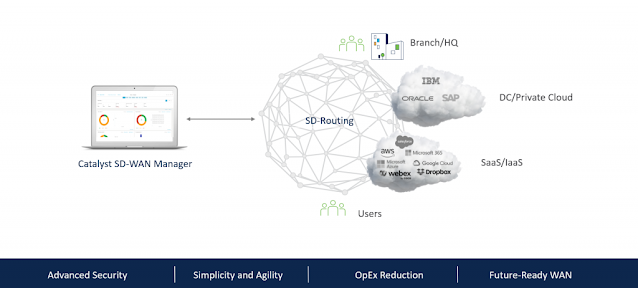
SD-Routing: Unlock Agility and Efficiency for the Secure WAN Edge
- Unify management: Manage device software upgrades, monitoring, and troubleshooting through the intuitive Catalyst SD-WAN Manager dashboard. This simplifies network operations and empowers you to manage both traditional routing and Catalyst SD-WAN environments.
- Tame legacy challenges: Simplify complex legacy operations with SD-Routing. Basic troubleshooting tools within the manager help you maintain and optimize performance. Continuous updates ensure your network stays ahead of the curve.
- Combat configuration drift: Manage and track changes with a unified platform. Use the manager to create configuration templates for standardized deployments and future SD-WAN migration.