Advances in data and technology have the potential to create a new kind of economic divide, one separating those with digital capabilities from those without. Cisco wants to help more countries and states get ahead. We’re doing so with our Country Digital Acceleration (CDA) program, which acts upon research insights from our Digital Readiness Index. Through CDA, we partner with governments, industry, and academia to create jobs and innovate with technology. To date, we have 370 projects active or completed in the areas of transportation, smart cities, healthcare, cybersecurity, and education. We begin a partnership by meeting with a country or state leader and finding where Cisco’s capabilities and a population’s needs align. Then, we provide technology, and just as important, knowledge. We help communities educate the next generation of tech professionals through:
◉ Cisco Networking Academy. Equipping students with real-world skills and career connections in fast-growing IT fields.
◉ Innovation Centers. Spaces where local innovation ecosystems can flourish and innovators can exchange ideas.
◉ University Investments. Sponsorships that allow Cisco to not only foster innovation, but also get access to new ideas.
How the program promotes environmental sustainability
As countries grow and develop, they generally pollute more. By applying digitization and IoT solutions to cities, Cisco, along with partners, can begin to break this cycle. For example:
◉ Smart parking solutions in Paris have reduced congestion by 30 percent
◉ Las Vegas is exploring the use of sensors to route autonomous shuttles to public transit stops based on demand
◉ Bucharest, Romania, achieved 75 percent energy savings with smart lighting, including LEDs and motion sensors
Socioeconomic research
A key input to our social investment strategy is Cisco’s original research. This is conducted in partnership with leading research and advisory companies and world-renowned academic institutions. We believe that our research can contribute to the dialogue about technology’s future impact. We want to understand: what will the digital revolution bring? And how can Cisco make strategic investments to help individuals thrive?
Our research also ensures the relevance of our investment focus areas, such as Cisco Networking Academy, critical human needs, educational opportunity, and economic empowerment. Our research helps heads of state, universities, educators, and nonprofit leaders set the direction for social investments and program development. For example, our research is designed to help states and nations:
◉ Predict the digital skills needed and the most effective ways to address skills gaps and job displacement
◉ Pinpoint the supply and demand of skilled labor in specific regions
◉ Assess their digital readiness and understand key interventions needed to improve
◉ Rethink education systems and partnerships to deliver graduates with the skills necessary for the jobs of the future
◉ Realize the benefits of digitization for all socioeconomic groups
We have presented our findings at the World Economic Forum (WEF), International Society for Technology in Education, Cisco Live, Networking Academy partner conference, and other venues.
Recent research
Our current research examines what it means to be digitally ready and how best to help individuals and countries thrive in the digital world. To uncover key insights and build our understanding of what it means for a country to be digitally ready, we created a holistic framework and measurement model. In 2019, we refreshed and expanded this model – first developed in 2017 — to include additional countries.
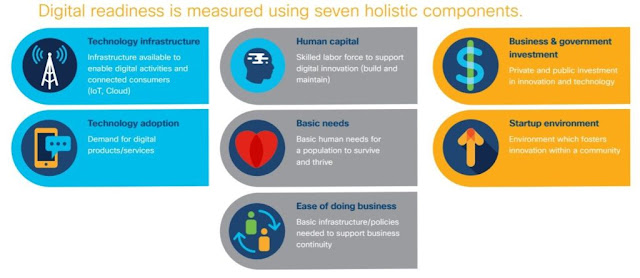
The model measures digital readiness on the basis of seven components: technology infrastructure, technology adoption, human capital, basic needs, ease of doing business, business and government investment and environment for startups.
Understanding a country’s digital readiness helps give insight to what specific investments or interventions could help a country move up in their digital journey. Overall, the 2019 findings remain consistent with the 2017 results, with digital readiness scores broadly mirroring developed and emerging economies. Three stages of digital readiness emerged based on the findings. “Activate” is the lowest stage of digital readiness, “Accelerate” is the middle stage, and “Amplify” is the highest. To better understand country needs, the Accelerate stage was further divided into two sub-stages. Here’s the map of countries identified by digital readiness:
Countries with higher digital readiness have higher levels of GDP per capita and tend to be more productive and prosperous, as measured against the WEF’s Global Competitiveness Index. Countries with higher digital readiness also tend to have a healthier natural environment and vital ecosystem as measured against Yale’s Environmental Performance Index.
Cisco Global Digital Readiness Index Digital Readiness scores reveal which countries are most digitally ready and which are less so, presenting opportunities for local government, industry, educational institutions, and community organizations to work together to help create an inclusive digital economy. The framework to measure digital readiness can also be applied to examine the level of digital readiness of states, territories, regions, and/or provinces within a country. In February 2018, the framework was applied to Australian states and territories. Key government and policymakers used the results to inform investment across the states. The findings were shared to help maximize digital inclusion and show how Australia can move further toward becoming a more digitally inclusive society.
We also made progress in FY19 on research to better understand the landscape of job opportunities resulting from digitization. In 2014, in partnership with Gartner, we studied job digitization and sought to understand the skills and competencies needed. The most recent study takes a broader view by expanding to roles driving digital transformation.
As a larger proportion of businesses transform digitally, the number of roles driving digital transformation will become a larger proportion of total workers. Technologies such as AI, cloud, and IoT are enabling digital change and impacting the future of business, which in turn is transitioning all organizations into digital and technology companies. The research identified 28 digital-related job roles, which align to five general job functions that are critical for driving digital business. The skills and competencies necessary to be successful in these 28 job roles were also identified. They include broad skills such as networking, security and privacy, business orientation, and analytical skills. Specialized skills in the areas of networking, software development, analytics/IoT, and security will also be crucial. The research found that a combination of critical workforce competencies, broad skills, and technical skills are needed to build a well-rounded employee in the age of digital transformation.