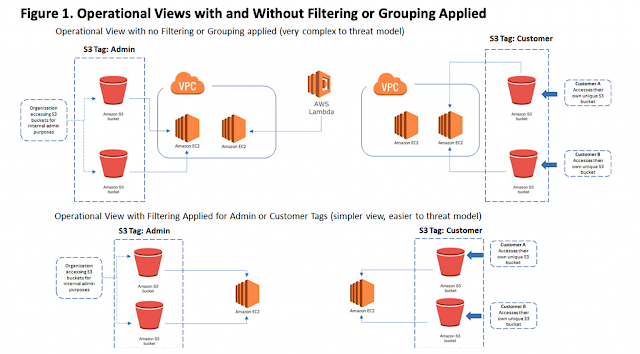
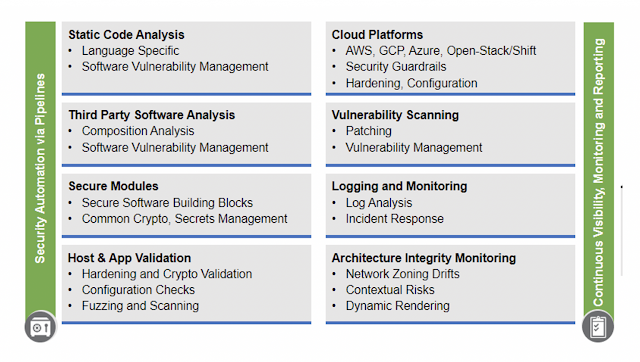
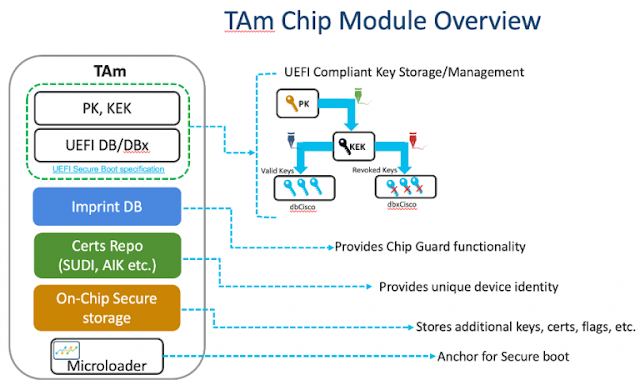
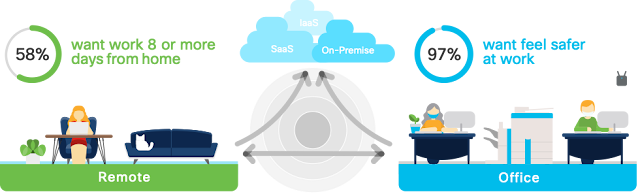
With average fixed broadband speeds projected to peak up to 110+ Mbps and the number of devices connected to IP networks ballooning to 29+ billion (more than three times the global population by 2023), Internet growth remains unabated and could even be stronger as the ongoing pandemic makes the internet more critical than ever to our daily lives, defining a new normal for humanity – video conferences replaced physical meetings, virtual “happy hours” with coworkers and friends replaced get-togethers, and online classrooms have immersed children in new methods of learning.
Shouldering the weight of these new digital experiences, communication service providers are experiencing a significant increase in traffic as well as a change in traffic patterns while struggling with average revenue per user (ARPU) trending flat to down. They need to reimagine their network architectures to deliver wireline services in a more cost-efficient manner. With the average revenue per user (ARPU) flat or declining, network architectures must evolve to deliver cost-efficient wireline services.
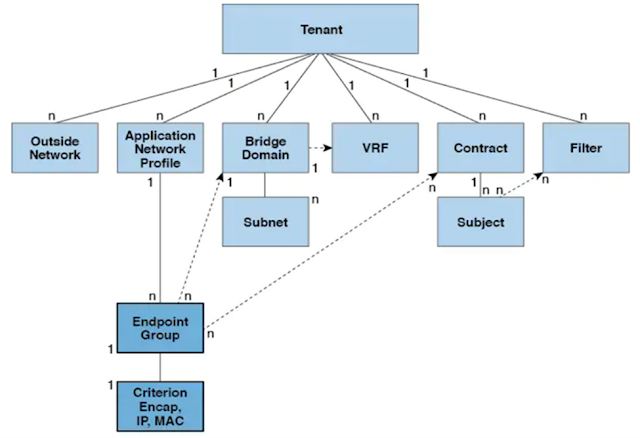
Responsible for critical subscriber management functions and a key component of any wireline services’ architecture, the broadband network gateway (BNG) has historically been placed at centralized edge locations. Unfortunately, these locations don’t provide the best balance between the user plane and the control plane’s performance requirements. The user plane (also known as the forwarding plane) scale is tied to the bandwidth per subscriber, while the control plane scale depends on the number of subscriber sessions and services provided for end-users. In most situations what happens is that either the control plane or the user plane ends up being either over or underutilized.
For years, the limited number of services per end-user and moderate bandwidth per user allowed network designers to roll out BNG devices that supported both user plane and control plane on the same device because minimal optimization was required. But today, with the exponential growth in traffic, subscribers, and services fueled by consumers’ appetite for new digital experiences, the traditional BNG architecture facing some severe limitations.
Given the changing needs and requirements, it is no longer possible to optimize the user plane and control plane when hosted on the same device. And it’s not scalable, making it difficult to support bandwidth or customer growth, control costs, and manage complexity with more and more BNG deployments. It is time to entirely rethink the BNG architecture.
Cloud Native Broadband Network Gateway
To overcome these operational challenges and right-size the economics, Cisco has developed a cloud native BNG (cnBNG) with control and user plane separation (CUPS) – an important architectural shift to enable a more agile, scalable, and cost-efficient network.
This new architecture simplifies network operations and enables independent location, scaling, and life cycle management of the control plane and the user plane. With the CUPS architecture, the control plane can be placed in a centralized data center, scaled as needed, and it can manage multiple user plane instances. Cloud native control planes provide agility and speed up the introduction of new service introduction using advanced automation. Communication Service Providers (CSPs) can now roll out leaner user plane instances (without control plane related subscriber management functions) closer to end-users, guaranteeing latency, and avoiding the unnecessary and costly transport of bandwidth-hungry services over core networks, Thereby, they can place Content Distribution Network (CDN’s) deeper into the network, enabling peering offload at the edge of the network hence delivering a better end-user experience.
There are also other benefits. A cloud native infrastructure provides cost-effective redundancy models that prevent cnBNG outages, minimizing the impact on broadband users. And, a cloud-native control plane lets communication service providers adopt continuous integration of new features, without impacting the user plane which remains isolated from these changes. As a result, operations are eased, thanks to a centralized control plane with well-defined APIs to facilitate the insertion into OSS/BSS systems.
When compared to a conventional BNG architecture, Cisco cloud native BNG architecture brings significant benefits:
1. A clean slate Fixed Mobile Convergence (FMC) ready architecture as the control plane is built from the ground-up with cloud-native tenets, integrating the subscriber management infrastructure components across domains (wireless, wireline, and cable)
2. Multiple levels of redundancy both at the user plane and control plane level
3. Optimized user plane choices for different deployment models at pre-aggregation and aggregation layers for converged services
4. Investment protection as an existing physical BNG can be used as user planes for cnBNG
5. Granular subscriber visibility using streaming telemetry and mass-scale automation, thanks to extensive Yang models and KPIs streamed via telemetry, enabling real-time API interaction with back-end systems
6. A Pay-as-you-grow model allows customers to purchase the user planes network capacity, as needed
Analysis has shown that these benefits translate into up to 55% Total Cost of Ownership (TCO) savings.
An Architecture Aligned to Standards
This past June, the Broadband Forum published a technical report on Control and User Plane Separation for a disaggregated BNG – the TR-459 – that notably defines the interfaces and the requirements for both control and user planes. Three CUPS interfaces are defined – the State Control Interface (SCi), the Control Packet Redirect Interface (CPRi), and the Management Interface (Mi).
With convergence in mind, the Broadband Forum has selected the Packet Forwarding Control Protocol (PFCP) defined by 3GPP for CUPS as the SCi protocol. It is a well-established protocol especially for subscriber management. Whereas the TR-459 is not yet fully mature, Cisco’s current cnBNG implementation is already aligned to it.
On the Road to Full Convergence
Historically, wireline, wireless, and cable subscriber management solutions have been deployed as siloed, centralized monolithic systems. Now, a common, cloud-native control plane can work with wireline, wireless, and cable access user planes paving the way to a universal, 5G core, converged subscriber management solution capable of delivering hybrid services. And Network Functions (NF’s) that are part of the common cloud-native control plane, not only share the subscriber management infrastructure, they also provide a consistent interface for policy management, automation, and service assurance systems.
Read More: 500-450: Implementing and Supporting Cisco Unified Contact Center Enterprise (UCCEIS)
Moving forward, CSPs can envision a complete convergence of policy layer and other north-bound systems, all the way up to the communication service provider’s IT systems.
With a converged model in place, customers can consume services and applications from the access technology of their choice, with a consistent experience. And communication service providers can pivot to a model with unified support services, and monitoring/activation systems, while creating sticky service bundles, as more end-user devices are tied to a single service, increasing customer retention.
Cisco is uniquely positioned to help customers embrace this new architecture with a strong end-to-end ecosystem of converged subscriber management across mobile, wireline, and cable, in addition to, a fully integrated telco cloud stack across compute, storage, software defined fabric, and cloud automation.
Source: cisco.com