Saturday, 29 June 2024
Cisco Enhances Zero Trust Access with Google
Friday, 28 June 2024
200-901 DEVASC Certification: Unlocking New Opportunities
The 200-901 DEVASC (Developing Applications and Automating Workflows using Cisco Platforms) certification is a highly regarded credential for IT professionals aiming to excel in network automation and application development. This certification demonstrates your proficiency in creating and managing applications on Cisco platforms, positioning you as a valuable asset in the tech industry. In this article, we will delve into ten key career benefits of obtaining the 200-901 DEVASC certification and how it can propel your professional growth to new heights.
What is the 200-901 DEVASC Certification?
The 200-901 DEVASC certification, offered by Cisco, is designed for professionals aiming to gain expertise in software development and network automation. This certification focuses on essential skills such as using Cisco APIs, implementing network programmability, and automating network tasks. It is ideal for those seeking roles in network engineering, software development, and DevOps.
Cisco 200-901 Exam Details:
- Exam Price: USD 300
- Duration: 120 minutes
- Number of Questions: 90-110
- Passing Score: Variable (750-850 / 1000 Approx.)
What Are the Prerequisites for the Cisco 200-901 DEVASC Exam?
There are no formal prerequisites for taking the 200-901 DEVASC exam. However, Cisco recommends having a foundational understanding of programming concepts and networking basics. Experience with Python programming, REST APIs, and an understanding of network fundamentals can be beneficial.
What Topics Are Covered in the 200-901 DEVASC Exam?
The 200-901 DEVASC exam covers a range of topics essential for developing and automating workflows on Cisco platforms. According to the Cisco 200-901 certification exam syllabus, the primary topics include:
- Software Development and Design: Understanding software development processes, data formats, and data encoding.
- Understanding and Using APIs: Knowledge of REST APIs, CRUD operations, and API authentication methods.
- Cisco Platforms and Development: Familiarity with Cisco platforms and their capabilities.
- Application Deployment and Security: Techniques for deploying applications and ensuring their security.
- Infrastructure and Automation: Implementing network automation using tools like Ansible and Puppet.
- Network Fundamentals: Basic networking concepts and IP addressing.
For a detailed breakdown, refer to the Cisco 200-901 certification exam syllabus.
How Difficult is the 200-901 DEVASC Exam?
The difficulty of the 200-901 DEVASC exam depends on your background and preparation. Candidates with a solid understanding of programming, networking basics, and hands-on experience with Cisco platforms typically find the exam manageable. However, it is still a challenging certification that requires thorough preparation and practice.
What Are the Best Study Materials and Resources for Preparing for the 200-901 DEVASC Exam?
To prepare effectively for the 200-901 DEVASC exam, consider using the following study materials and resources:
Official Cisco Study Guides:
- Cisco offers official study guides and e-learning courses tailored to the DEVASC exam. These resources are designed by Cisco experts and provide comprehensive coverage of all exam objectives. The guides include detailed explanations, practical examples, and hands-on labs to reinforce learning.
200-901 Practice Tests and Mock Exams:
- 200-901 Practice tests and mock exams are invaluable for familiarizing yourself with the exam format and identifying areas where you need improvement. They simulate the actual exam environment and help you gauge your readiness.
- Websites like Nwexam.com offer quality practice tests. Additionally, Cisco's practice exams can be a good benchmark.
Cisco DevNet:
- Utilize resources from the Cisco DevNet community for practical insights and tutorials. Cisco DevNet provides a wealth of learning labs, sandboxes, and documentation to help you gain hands-on experience with Cisco technologies.
- Engage with the DevNet community to ask questions, share knowledge, and learn from others who are also preparing for the exam.
Books:
- Books such as "Developing Applications for Cisco Webex and Webex Devices" are excellent resources for in-depth learning. They provide detailed information and practical examples that are crucial for understanding the topics covered in the exam.
- Other recommended books include "Cisco Certified DevNet Associate DEVASC 200-901 Official Cert Guide" and "Programming and Automating Cisco Networks: A Guide to Network Programmability and Automation in the Data Center, Campus, and WAN."
Supplementary Resources:
- Forums and Study Groups: Join forums and study groups on platforms like Reddit and Cisco Learning Network. Interacting with others preparing for the same exam can provide additional insights and support.
- Webinars and Videos: Many websites, including Cisco's own training portal, offer webinars and video tutorials that can be helpful.
Top 10 Career Benefits of Earning the 200-901 DEVASC Certification
1. Enhanced Technical Skills
The 200-901 DEVASC certification focuses on developing your technical skills in network automation and programming. You'll gain hands-on experience with Cisco APIs, network programmability, and the integration of software and hardware systems. This expertise is highly sought after in the IT industry, where the demand for skilled professionals in automation and application development continues to grow.
2. Competitive Edge in the Job Market
In a competitive job market, having the 200-901 DEVASC certification on your resume sets you apart from other candidates. Employers recognize the value of this certification and often prioritize candidates who possess it. By demonstrating your knowledge and proficiency in network automation, you increase your chances of landing lucrative job offers and promotions.
3. Higher Earning Potential
Certified professionals often command higher salaries compared to their non-certified counterparts. The 200-901 DEVASC certification can significantly boost your earning potential by validating your specialized skills in network automation and application development. Employers are willing to pay a premium for employees who can streamline processes and improve efficiency through automation.
4. Career Advancement Opportunities
The 200-901 DEVASC certification opens doors to various career advancement opportunities. With this credential, you can pursue roles such as Network Automation Engineer, Software Developer, DevOps Engineer, and more. These positions often come with greater responsibilities, higher salaries, and the potential for leadership roles within organizations.
5. Recognition and Credibility
Earning the 200-901 DEVASC certification enhances your professional credibility and recognition in the industry. It demonstrates your commitment to staying updated with the latest technologies and best practices in network automation and application development. This recognition can lead to increased trust and respect from peers, employers, and clients.
6. Skill Validation and Confidence
The certification process involves rigorous training and examinations that validate your skills and knowledge. Successfully earning the 200-901 DEVASC certification boosts your confidence in your abilities to tackle complex network automation tasks and develop robust applications. This confidence translates into better job performance and career satisfaction.
7. Networking Opportunities
Pursuing the 200-901 DEVASC certification provides you with opportunities to network with other professionals in the field. You can connect with peers, mentors, and industry experts through certification courses, study groups, and professional events. These connections can be valuable for career growth, job referrals, and staying informed about industry trends.
8. Access to Exclusive Resources
As a certified professional, you gain access to exclusive resources provided by Cisco. These resources include advanced training materials, webinars, technical support, and community forums. Leveraging these resources can help you stay ahead of the curve, continuously improve your skills, and solve complex problems more efficiently.
9. Contribution to Organizational Success
With the 200-901 DEVASC certification, you can make significant contributions to your organization’s success. Your expertise in network automation and application development can streamline operations, reduce costs, and enhance overall productivity. Organizations value employees who can drive innovation and deliver tangible results.
10. Personal and Professional Growth
The journey to earning the 200-901 DEVASC certification is challenging and rewarding. It requires dedication, continuous learning, and problem-solving skills. This process not only contributes to your professional growth but also fosters personal development. You become more adept at critical thinking, time management, and adapting to new technologies.
Conclusion
Achieving career growth with the 200-901 DEVASC certification is a strategic move for any IT professional. Cisco Certified DevNet Associate certification offers numerous benefits, including enhanced technical skills, increased earning potential, and greater job opportunities. By investing in this credential, you position yourself as a valuable asset to any organization and set the stage for a successful and fulfilling career in network automation and application development.
Thursday, 27 June 2024
Cisco API Documentations Is Now Adapted for Gen AI Technologies
OpenAPI documentations is now available to download
- Construct code or script that utilizes related Cisco API
- Find related API operations or ask to fix existing code using the information in the API documentation
- Create integrations with Cisco products through API
- Create and test AI agents
- Utilize related Cisco OpenAPI documentation locally or using approved AI tools in your organization.
Structured vs Unstructured data
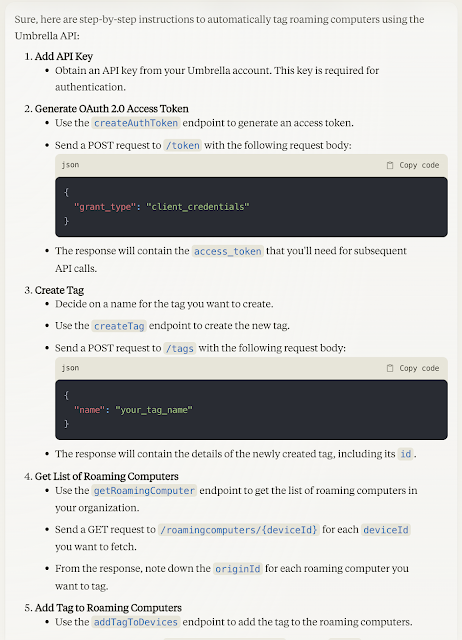
- Add API Key
- Generate OAuth 2.0 access token
- Create tag
- Get the list of roaming computers and identify related ‘originId’
- Add tag to devices.
Benefits of using LLM-friendly documentation as a part of the prompt
Tuesday, 25 June 2024
Security Cloud Control: Pioneering the Future of Security Management
Customer Outcomes with Security Cloud Control
Saturday, 22 June 2024
Up your Quality of Life with Secure MSP Hub and Secure MSP Center
Thursday, 20 June 2024
Campaign Spotlight: Driving Demand with Marketing Velocity Central and User Protection Campaign
The User Protection Challenge
Cisco User Protection Suite
- Better experiences: enables your customers to be productive at their job with secure, seamless access to all resources
- Better economics: Work with one vendor to provide the breadth of solutions to protect your users – that means one contact, one contract, and one renewal.
- Better efficacy: improve your customers’ security posture, lower their risks, and keep their sensitive information safe.
- Consolidating cybersecurity solutions under one vendor to simplify subscription management for partners
- Expanding the opportunity into an Enterprise Agreement (EA), making it much more difficult for competitive security providers to displace incumbency
- Collaborating with our customers as a trusted advisor and support customers on their user protection journey
- Improving efficiency and saving customers money, while providing a valuable business outcome
Drive demand and pipeline with Marketing Velocity Central
- Co-branding: show your credibility by downloading and using your Cisco partnership logo through logo builder
- Customization: set yourself apart by picking a ready-to-go campaign, edit it and choose from the many images in our library
- Account-Based Targeting: upload and manage your list of contacts in one single place while tracking campaign engagement via a lead-scoring method
- Full-Service Activities: hire a third-party marketing agency to help you obtain even better results and use your Cisco marketing funds, or your own funds
Tuesday, 18 June 2024
Stay Compliant: Cisco Secure Workload Introduces State-of-the-art, Persona-based Reporting
A New Era of Informed Decision Making
Addresses Challenges Directly
Saturday, 15 June 2024
Bolster SaaS Security Posture Management with Zero Trust Architecture
Introducing Zero Trust Posture Management
Cisco Secure Access and AppOmni SaaS Security Platform
How ZTPM Complements ZTNA
- Secure access to all applications including those involving non-standard protocols as well as those based on multi-channel and client-to-client architectures
- A single unified management console across all security modules
- Comprehensive ‘best-of-breed’ security capabilities, consistent rulesets, and entails a minimal learning curve
- Resilient cloud-native architecture with extensive end-user count scalability, efficient single-pass processing for faster responses
- Automatic load distribution and rebalancing of traffic fosters better performance
- Visibility into data access configuration and least privilege within SaaS applications
- Security coverage for all SaaS identities (human and machine) i.e. external users, anonymous/ guest-users, and third party or cloud-to-cloud applications
- Application and identity-aware threat detection to monitor user behavior of internal and external users
- Continuous security of application posture, configuration drift, and critical application components of SaaS applications
- Identify and mitigate misconfigurations such as side-loaded accounts or misconfigured Single Sign On (SSO) that may allow bypassing of ZTNA controls and protect your users from password attacks and account compromise
Thursday, 13 June 2024
Cisco Simplifies Cloud Security with AWS Cloud WAN Service Insertion
- Achieving secure connectivity across clouds, virtual private clouds (VPCs), regions, and on-premises networks
- Ensuring security is baked into the network architecture from the start.
Cisco’s cloud firewalls
- Cisco Secure Firewall Threat Defense Virtual (formerly FTDv) is the virtualized option of the Secure Firewall Threat Defense solution, enabling you to extend your network security capabilities from on-premises into the cloud, gaining a complete view of your network environment.
- Cisco Multicloud Defense is a cloud-native security-as-a-service offering that automatically scales to secure your cloud applications wherever they’re deployed. Multicloud Defense offers the same infrastructure automation that you expect from a cloud service, making your security as easy to deploy as your application is.
Benefits of Cisco cloud firewalls with Cloud WAN
- Unified Infrastructure for Security and Global Networking: AWS Cloud WAN offers a unified infrastructure designed for extensive AWS deployments worldwide. The integration of Cisco’s cloud firewalls with AWS Cloud WAN equips organizations with superior security measures for protecting traffic within regions, between regions, and from on-premises networks to cloud environments.
- Simplified Multi-Regional Security Deployment: Many enterprises utilizing AWS Cloud WAN establish multi-regional networks to facilitate regional growth or implement disaster recovery strategies. The new service insertion feature streamlines the deployment across multiple regions, enabling straightforward traffic routing for both intra- and inter-regional flows through the security infrastructure, thereby eliminating the complexity associated with intricate multi-regional network arrangements.
- Seamless integration: Customers often need inter-VPC, VPC-to-internet, or on-premises-to-VPC traffic inspected. With Cisco’s cloud firewalls supporting AWS Cloud WAN Services Insertion, customers can easily steer network traffic for inspection without creating and managing complex routing configurations.
- Ease of management: Customers are constantly looking to simplify operational complexities. Cisco’s cloud firewall does all the heavy lifting in deployment and management, allowing customers to focus on their business priorities.