Saturday, 18 May 2024
Integrating IT and Campus Facilities for Future-Ready Learning Space
Monday, 7 June 2021
Education, Education, Education: RSA 2021 and the State of Education Security
There is an old maxim in the real estate profession that is used when evaluating the value of a home. Realtors often speak of “location, location, location”, as if the customer involved in the transaction is so unaware of that factor that it requires the incessant repetition. In cybersecurity, however, one area that is in dire need of a recurrent reminder is the area of education, both of cybersecurity professionals, as well as targeting that specialized knowledge towards the education sector.
Resilience, and Investing in People
This year’s RSA conference was started with an inspirational keynote message from CEO Charles (Chuck) Robbins. The theme of this year’s RSA conference was resilience, which is also the key to effective cybersecurity. The vision for a post-pandemic world is one where Cisco will invest more to make the world a safer place, while carrying out that vision in less time than ever.
An Unnoticed Target
Wendy’s Keen Insights
Follow the Patterns
Why a School is a Good Target
How Cisco is Positioned to Protect These Valuable Assets
Wednesday, 10 March 2021
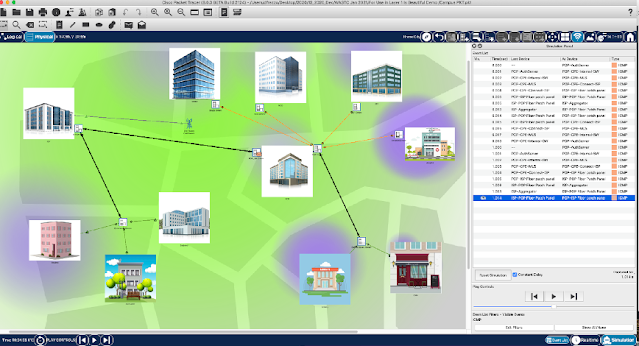
Meet the Enchanted Virtual Classroom
Cisco Networking Academy enables distance learning
The COVID-19 pandemic has disrupted the traditional education model for millions of students and teachers around the world, including the nearly 12,000 learning institutions worldwide that participate as Cisco Networking Academy schools.
The Networking Academy curriculum has been delivered via a hybrid model of in-person and online teaching. So when the pandemic hit, and while many schools, teachers, and students experienced widespread disruption and challenges in making the move to a 100 percent online model, the Networking Academy transition was manageable, and students and teachers were already equipped to operate exclusively online effectively.
Beyond the move to a fully online model, the events of 2020 pushed our engineering teams at Cisco to look for new ways to offer both students and teachers more immersive experiences and better learning engagement opportunities.
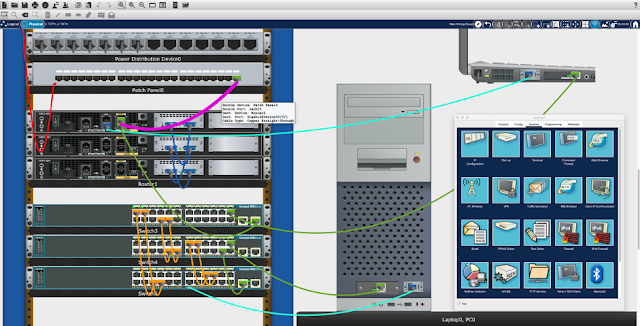
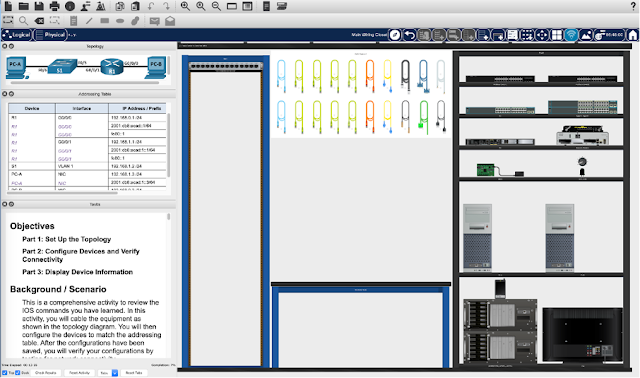
Working hand in hand with Networking Academy instructors, our engineers delivered significant enhancements to Cisco Packet Tracer’s physical mode. Combined with significant increases in the availability of our Cisco Webex collaboration suite, our teams have created what we like to think of as an “Enchanted Virtual Classroom.”
Welcome to a world of enchantment
The concept of enchantment in the digital world – and specifically the notion of “Enchanted Objects” – has been introduced by David Rose, product designer and lecturer at the MIT Media Lab. According to Rose, Enchanted Objects can be brought to life thanks to specific design guidelines for immersive Internet of Things (IoT) environments that align with fundamental human desires including “omniscience, telepathy, safekeeping, immortality, teleportation, and expression.”
Rose believes that IoT sensors and actuators embedded in our physical environments can lead to enchanting experiences.
Within Cisco Networking Academy, we are applying this design philosophy to distance learning.
Fusing Packet Tracer – which invokes senses of safekeeping (a safe place to make mistakes), omniscience (creating networks from scratch), and expression (telling networking stories relevant to their lives), with Webex – which invokes senses of telepathy (insight into how others think) and teleportation (video collaboration as if we were sharing the same physical space doing labs together) enables useful, purpose-driven, even enchanting distance learning experiences.
We seek to help address issues that arise from the loss of physically co-located instructors, students, and equipment. A simulation-based microworld, like Packet Tracer 8.0, with enhanced physical mode representations, used in tandem with collaboration software such as Webex, may have synergies that lead to effective and delightful experiences.
The Charm of Packet Tracer
The magic of learning through Webex
Tuesday, 24 December 2019
Ransomware in Education: How to use your Network to Stay Ahead of Attacks
A typical response may be to deploy multiple security technologies to block threats from entering your organization at various attack vectors, and you should continue to do so. However, just relying on these techniques isn’t enough since 100% prevention is not possible in today’s complex threat landscape. That’s where continuous monitoring of your network’s behavior comes in. By using this approach, you can help detect and respond to a ransomware attack more quickly and effectively.
How to stay ahead of cyber threats
Your network is a source-of-truth of every activity – normal or malicious. Adversaries must use your network in order to carry out their malicious objectives. Because of this, collecting and analyzing your network telemetry is an effective way of detecting advanced threats, like ransomware. Here’s how it helps you.
◉ Detect threats early by pinpointing suspicious behavior. Ransomware attacks are generally initiated through methods like a phishing email or exploitation of a vulnerability. It might involve behavior such as port scanning, command-and-control (C&C) communication back to the attacker network, etc. Whatever means the attackers use, the activity touches the network. By using behavioral modeling, this kind of activity can be easily detected. You can also create custom security policy alerts to detect restricted communications such as use of SMB protocol, or access to sensitive data servers from outside the network. So even if the ransomware is an unknown strain and has infected the organization, the anomalous behavior will give the attackers away.
◉ Correlate local alerts to global campaigns. Attackers often reuse ransomware strains to infiltrate multiple organizations. An effective network security analytics solution is powered by industry-leading threat intelligence that has the knowledge of all the malicious domains, servers, campaigns, and other indicators of compromise. Using multiple analytical techniques like statistical modeling and machine learning, billions of network sessions within your organization can be processed and correlated to global campaigns, in order to pinpoint attacks and then quickly remediate.
◉ Perform forensic analysis for incident response. Your organization has been infected, and you have been immediately notified through alerts of the ransomware attack. Now what? Time is of the essence and your security teams need to answer questions like what machines have been infected, what was the source of the attack, and where are communications occurring? Because you have a record of every network communication, you can begin from the alert and investigate back in time to conduct a thorough forensic analysis to answer those questions and contain the ransomware.
Industry-leading network visibility and security analytics
The capabilities described above are offered by Cisco’s network traffic analysis solution, called Cisco Stealthwatch. It provides enterprise-wide visibility, from the private network to the public cloud, and applies advanced security analytics to detect and respond to threats in real-time.
By using a combination of behavioral modeling, machine learning, and global threat intelligence, Stealthwatch can quickly (and with high confidence) detect threats such as:
◉ C&C attacks
◉ Ransomware
◉ DDoS attacks
◉ Illicit cryptomining
◉ Unknown malware
◉ Insider threats.
With a single, agentless solution, you get comprehensive threat monitoring across your data center, branch, endpoint, and cloud. Plus, it can also analyze encrypted traffic for threats, without any decryption, using our proprietary Encrypted Traffic Analytics technology.
By deploying Stealthwatch, you can turn your network into a “threat sensor” by simply collecting telemetry such as NetFlow. And there is no need to deploy multiple agents. Stealthwatch can be deployed easily. Best of all, it scales automatically with your infrastructure, growing as your needs grow.