For the 2nd year, RSA Conference 2018 APJ created an educational exhibit, sponsored by RSA and Cisco, to monitor the RSA Conference public Wi-Fi network provided by the Marina Bay Sands (MBS). This exhibit was created in the form of the RSA Conference Security Operations Center (SOC). RSA and Cisco provided technology and staffing to monitor the network for threats, but also to educate attendees on the risks of free Wi-Fi.
What is the difference between a SOC and a NOC?
Network Operations Center
The NOC is usually responsible for monitoring and maintaining the overall network infrastructure—its primary function is to ensure uninterrupted network service
Security Operations Center
The SOC is responsible for protecting networks, as well as web sites, applications, databases, servers and data centers and other technologies
RSA and Cisco provided the SOC. The NOC was provided by the MBS.
The mission of the RSAC SOC was to ensure the conference Wi-Fi is not attacked (denial of service, laterally spreading malware, etc.). We did not block malicious DNS traffic, downloads or attachments; as this was a learning and demonstration environment. We make sure that network is protected from attackers. We locate (when we can) and advise users when they are at risk.
What technology is in the RSAC SOC?
MBS provided the RSAC SOC a span of all network traffic from the .RSAConference network, which was passed through the Cisco Next Generation Firewall / ISP and then split the traffic to NetWitness Packets NetWitness Packets and the Cisco Stealthwatch teams.
RSA used NetWitness Packets to collect and investigate all traffic on the Wi-Fi network, from the firewall; to detect deviations from normal behavior and create a probability-weighted risk score for alerts based on these results. NetWitness inspects every network packet session for threat indicators at time of collection and enriches this data with threat intelligence and business context. At the end of the conference, all of this data was wiped from NetWitness.
For suspicious files that might be malicious, NetWitness Packets checks a community AV lookup, some static analysis and its own network intelligence. Then the NetWitness Orchestrator sends the files to Cisco Threat Grid for dynamic malware analysis.
Threat Grid combines advanced sandboxing with threat intelligence into one unified solution to protect organizations from malware. Threat Grid analyzes the behavior of a file against millions of samples and billions of malware artifacts. The SOC team had a global and historical view of the malware, what it’s doing and how large a threat it posed to the RSAC network.
Threat Grid identifies key behavioral indicators of malware and their associated campaigns. The SOC team was able to save time by quickly prioritizing attacks with the biggest potential impact. We used tools like Glovebox, to safely interact with samples and observe malware behavior directly. In addition, we used Cisco Umbrella to have visibility in all DNS activity. We also used the Threat Intelligence of Cisco Visibility and Talos Intelligence.
When the Cisco team found a potential threat, they handed it off to the RSA team for further investigation. In summary, the technology stack was:
◈ Firewall – Cisco Next Generation Firewall with IPS
◈ Full Packet Capture and Investigation – RSA NetWitness Packets
◈ Orchestration – RSA NetWitness Orchestrator, powered by Demisto
◈ Dynamic File Analysis – Cisco Threat Grid
◈ DNS / IP Intelligence – Cisco Umbrella / Cisco Umbrella Investigate
◈ Encrypted Traffic Analytics – Cisco Stealthwatch and Cognitive Threat Analytics
◈ Threat Intelligence – Cisco Visibility
Identifying endpoint vulnerabilities without an agent
Cisco’s Next Generation Firewall was set up as the perimeter Firewall for the wireless connection of the RSA APJ event. All traffic to and from wireless guests went through the Firepower Threat Defense (FTD). FTD not only detected threats, but also discovered what was running on the network endpoints; such as Operating Systems, Ports, Applications and Files.
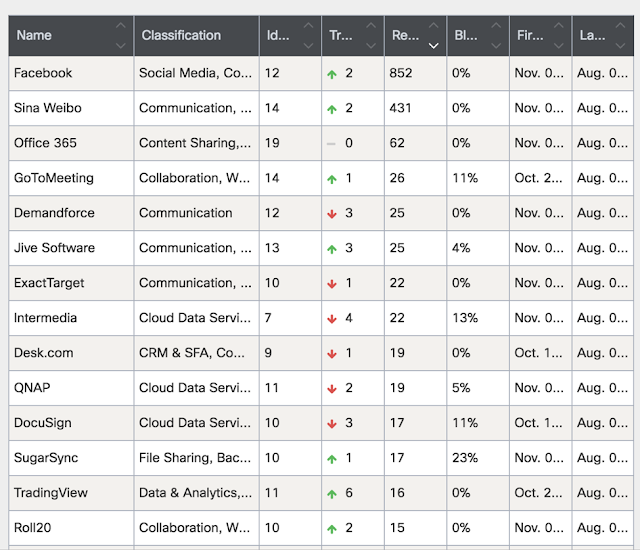
Discovered Applications
Discovered Files
Geolocation Information
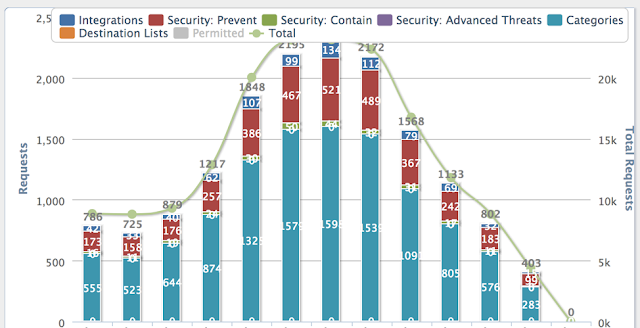
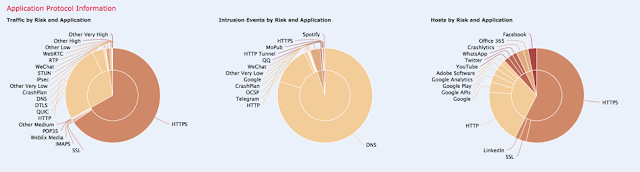
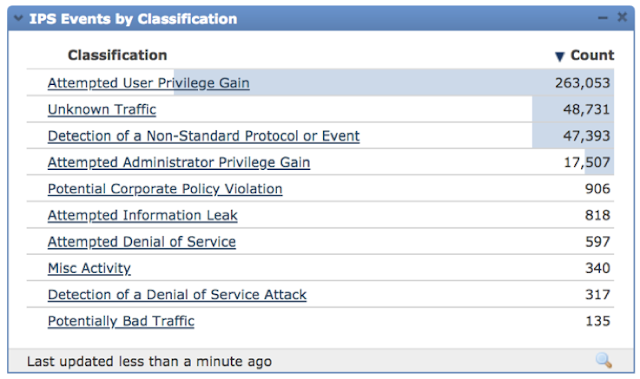
During the conference, several threats were detected, and we were able to see the total Connections and Bytes connecting to known bad IP Addresses.
We were also able to see the Total Intrusion Events detected per Classification.
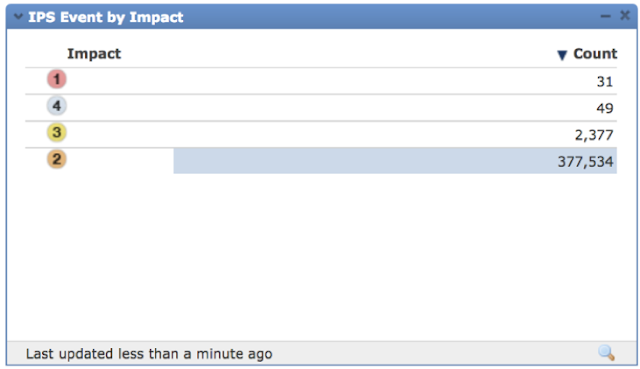
FTD automatically correlated threat events with the contextual information discovered to identify which IPS events to prioritize for further investigation. This was reflected via Impact Flag 1 events. Data showed that there were 31 events to be prioritized.
Impact Flag 1 events shown below.
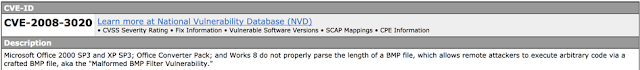
Checking the Rule documentation of the BMP overflow IPS event, it shows that it is applicable only for traffic coming from external network to internal network.
And, applicable if the target host has this vulnerability, with cve.mitre.org documentation included.
Checking on the event we confirmed that the event is coming from the Internet going inside the network. IPS Event Details below.
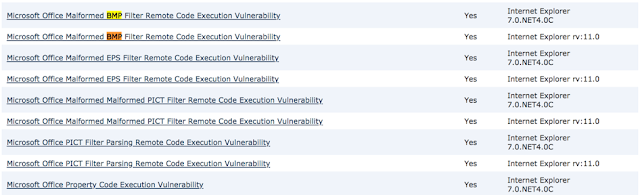
Checking on the host profile, we confirmed the target host had this specific vulnerability.
Vulnerability list of the target host based on the discovered Operating System and Applications.
Why download the exploit, when you can carry it with you?
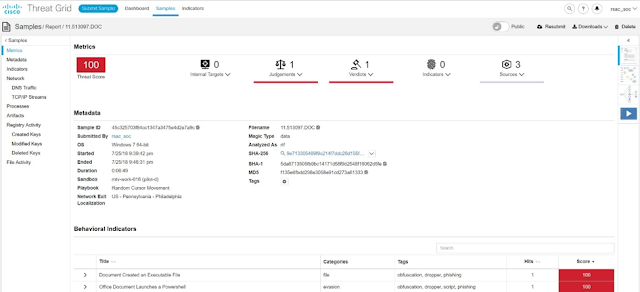
On the 2nd day of the Conference, the SOC team observed a .DOC file sent to a conference attendee in a plain text email, along with several PDFs. The .DOC file was extracted by NetWitness and had a score of 0 from the RSA Malware Analysis Community lookup, meaning it had never been detected by an AV vendor. The Static Analysis score was 80, making it worth a review, and the Dynamic Analysis/Sandbox score from Threat Grid was 100, meaning confirmed malicious based on behavior. The team went into action to assess the threat.
The .DOC file was assigned a Threat Score of 100 for the Behaviors of launching Powershell and creating an Executable File.
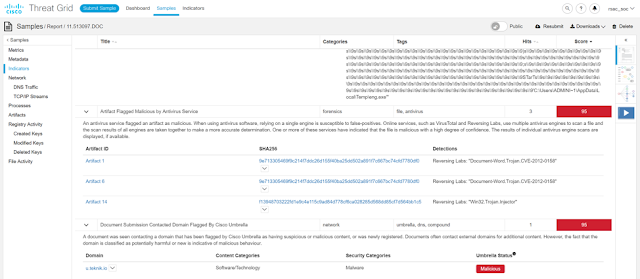
We were able to see the code in the document to create and launch the eng.exe file.
After the creation of the executable, the malware dropped some artifacts on disk that are known to be used by remote access Trojans and opened communication with a domain on the Umbrella block list for Malicious.
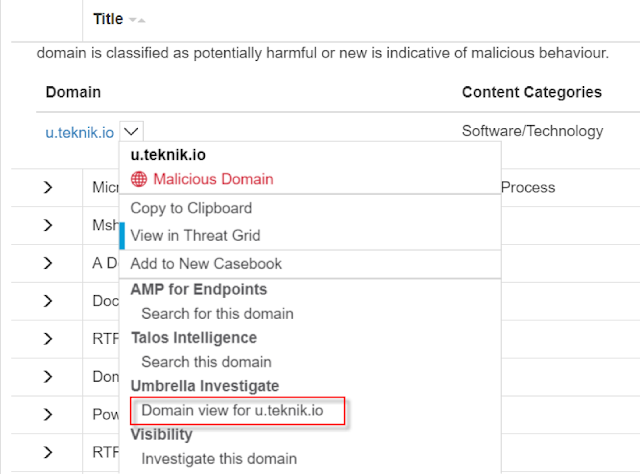
We pivoted to Umbrella Investigate to learn more. If we had AMP for Endpoints deployed on the endpoints in the network, we would have instantly been able to see affected endpoints and remediate.
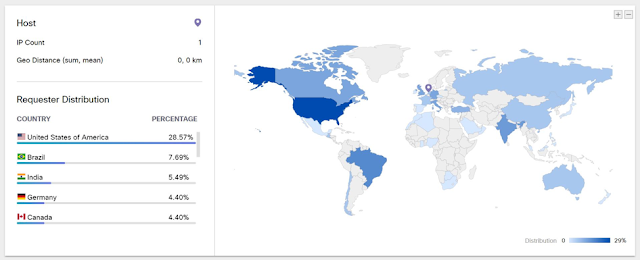
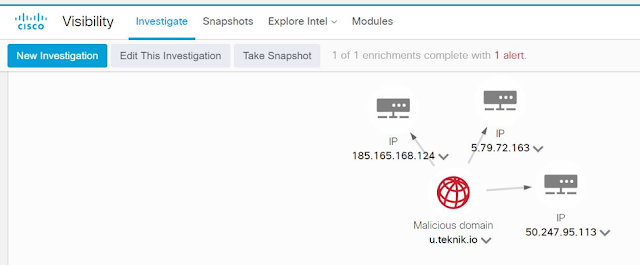
In Umbrella Investigate, we learned more about the domain, including the global requests for the campaign.
Most affected computers from the United States.
We found the hosted IP address 5[.]79[.]72[.]163 (link to the Investigate report) and then went into Cisco Visibility to access the global Cisco threat intelligence and to see if there were more associated IPs.
With this intelligence, we were able to go to the Firewall and NetWitness teams and check if there was any outbound communication to those three IP addresses. There were none, indicated the person who received the email did not open it on a vulnerable endpoint at the conference.
Everything an attacker needs for spear phishing lures
Threat Grid currently supports the following file types for analysis:
For RSAC SOC, the NetWitness team focused on submitting the following file types, with the distribution in parenthesis:
◈ .PDF (93%)
◈ .EXE (4%)
◈ .DLL (2%)
◈ .DOC/X (<1%)
◈ .XLS/X (<1%)
We saw many invoices, billing statements and confidential business proposals as attachments to emails sent with unsecure protocols, such as POP3 and HTTP. Each could be used by an attacker, sniffing the public network; to craft a custom spear phishing lure, as they had legitimate business and financial information; such as the email addresses of the sender/receiver, account information, billing address and the types of products/services the email recipient expected to receive.
Cryptomining
At Black Hat Asia 2018 in March, we saw a massive increase in cryptocurrency mining. Also, with the Black Hat training courses, there were 20 times as many domains of concern for roughly the same amount of DNS requests, around 5 million for each of the conferences in Singapore.
There was much less Cryptomining at RSAC; however, several common sites were active:
◈ widgetsbitcoin[.]com (links to the Umbrella Investigate report)
◈ api.hitbtc[.]com
◈ ws022.coinhive[.]com
◈ coinhive[.]com
◈ cdn.mngepvra[.]com
◈ authedmine[.]com
◈ coin-hive[.]com
◈ coinone.co[.]kr
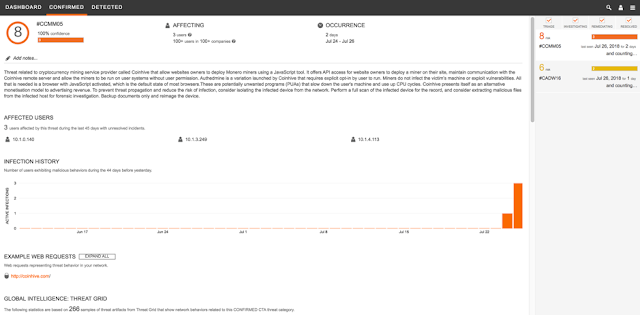
When we saw the cryptocurrency mining activity based on Umbrella DNS request, Stealthwatch provided the visibility into endpoint without an agent/connector. Below is the dashboard of Cognitive Cloud Analytics (CTA). Together with Cisco Stealthwatch Enterprise, CTA is part of Cisco Encrypted Traffic Analytics. This solution can detect malware hiding in encrypted traffic without decrypting the data.
Upon investigate into “High Risk” and “Confirmed” event. There were three endpoints identified to have cryptocurrency mining activity at the time of investigation.
Below is the snapshot of the endpoint activities related to cryptocurrency mining.
Together with Umbrella, we could identify endpoint with initial cryptocurrency mining DNS request and detail HTTPS request to the server with Stealthwatch Enterprise and CTA.