If you’re like most IT people, never does a day go by that you’re not working on multiple tasks at once: ensuring on prem data centers and public cloud networks are running smoothly; monitoring the consistency of network security policies; and making sure all of it meets compliance demands. And that doesn’t even begin to address the enormous pressure applications have begun to put on the underlying network infrastructure. As a result, data centers are no longer a fixed entity, but rather a mesh of intelligent infrastructure that spans multiple clouds and geographies. With new applications constantly being added to an infrastructure, roadblocks are beginning to arise, making the role of IT teams more complicated than ever.
The network industry has recognized its unique set of challenges and is addressing them in the form of an intent-based networking architectural approach that builds on software-defined networking to allow continuous, dynamic network alignment with IT and business policies. This means that application, security, and compliance policies can be defined once then enforced and monitored between any groups of users or things and any application or service – or even between application services themselves – wherever they are located.
Forward-looking companies are now using applications not just as a way to engage with customers but also as a means for employees and the organizations themselves to communicate and work together efficiently. To create a more streamlined infrastructure, Cisco has integrated Application Centric Infrastructure (ACI) with the application layer and the enterprise campus to help large and medium-sized organizations that need to adopt a holistic network infrastructure strategy. Designed to help businesses cope with the unique performance, security, and management challenges of highly distributed applications, data, users, and devices, Cisco ACI also addresses the issue of legacy approaches. Having relied on manual processes to secure data and applications and control access, these approaches are no longer adequate or sustainable, and therefore need to be modernized.
With the ACI and AppDynamics (AppD) integration, application performance correlates with network health, while the Cisco DNA Center and the Identity Services Engine (ISE) work together to deliver end-to-end identity-based policy and access control between users or devices on campus and applications or data anywhere.
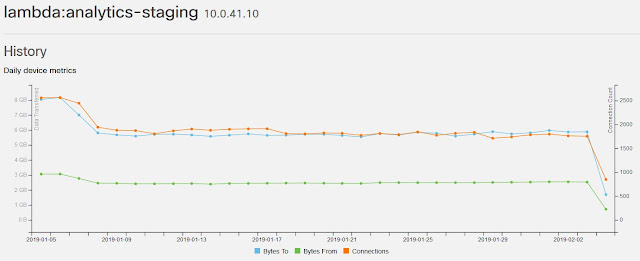
Simplifying the deployments and management of applications requires more than just providing and managing the infrastructure that supports them. Cicso’s AppD provides IT teams with the application-layer visibility and monitoring required in an intent-based architecture to validate that IT and business policies are being met across the network. The Cisco ACI and AppDynamics solution also offers high-quality app performance monitoring, richer diagnostic capability for app and network performance, and faster root-cause analysis of problems, with immediate triage sent to the right people quickly.
Dynamic Network Alignment with IT and Business Policies
The network industry has recognized its unique set of challenges and is addressing them in the form of an intent-based networking architectural approach that builds on software-defined networking to allow continuous, dynamic network alignment with IT and business policies. This means that application, security, and compliance policies can be defined once then enforced and monitored between any groups of users or things and any application or service – or even between application services themselves – wherever they are located.
Forward-looking companies are now using applications not just as a way to engage with customers but also as a means for employees and the organizations themselves to communicate and work together efficiently. To create a more streamlined infrastructure, Cisco has integrated Application Centric Infrastructure (ACI) with the application layer and the enterprise campus to help large and medium-sized organizations that need to adopt a holistic network infrastructure strategy. Designed to help businesses cope with the unique performance, security, and management challenges of highly distributed applications, data, users, and devices, Cisco ACI also addresses the issue of legacy approaches. Having relied on manual processes to secure data and applications and control access, these approaches are no longer adequate or sustainable, and therefore need to be modernized.
With the ACI and AppDynamics (AppD) integration, application performance correlates with network health, while the Cisco DNA Center and the Identity Services Engine (ISE) work together to deliver end-to-end identity-based policy and access control between users or devices on campus and applications or data anywhere.
Richer Diagnostic Capabilities for Healthier Networks and Apps
Simplifying the deployments and management of applications requires more than just providing and managing the infrastructure that supports them. Cicso’s AppD provides IT teams with the application-layer visibility and monitoring required in an intent-based architecture to validate that IT and business policies are being met across the network. The Cisco ACI and AppDynamics solution also offers high-quality app performance monitoring, richer diagnostic capability for app and network performance, and faster root-cause analysis of problems, with immediate triage sent to the right people quickly.
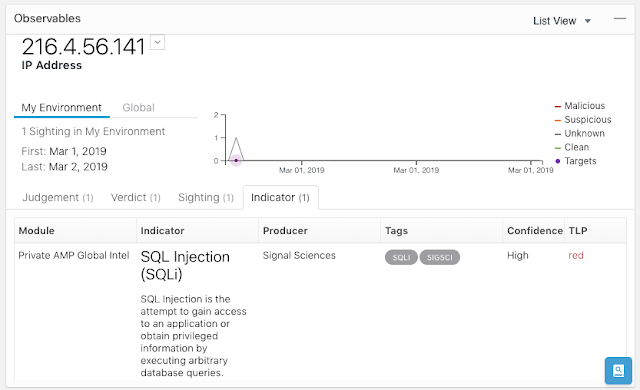
That said, failures in applications can happen for a variety of reasons, often leading to what’s commonly known as “the blame game,” with people asking questions like, “Is it the network failure or the application failure? Who is responsible – the network team or the apps team?” Manual methods are slow, cumbersome and oftentimes simply impossible to detect failures in an assertive fashion. The ACI and AppD integration offers deep visibility into the application processes andenables faster root cause analysis bytaking the ambiguity out and pinpointing the problem – saving time, money, and, most importantly, getting the application back up and running right away.
Network Segmentation is a Must
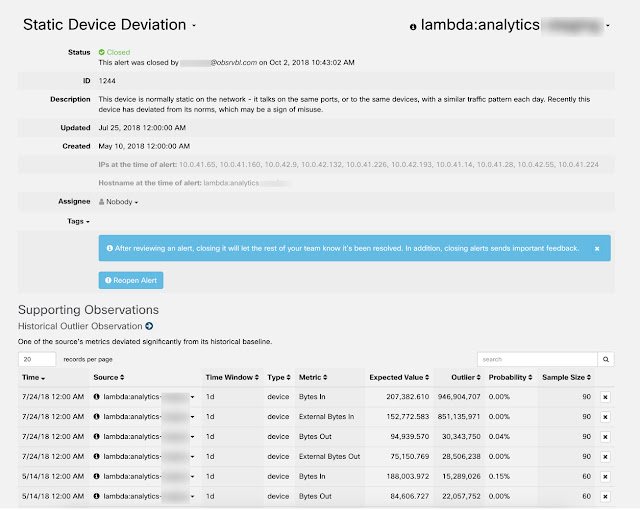
Hyper-distributed applications and highly mobile users, increased cyber-security threats, and even more regulatory requirements make network segmentation a must for reducing risk and better compliance. Cisco ACI and Cisco DNA Center/ISE policy integration allows the marrying of Cisco ACI’s application-based microsegmentation in the data center, with Cisco SD Access user-group based segmentation across the campus and branch. This integration automates the mapping and enforcement of segmentation policy based on the user’s security profile as they access resources within the data center, enabling security administrators to manage end-to-end, user-to-application segmentation seamlessly. A common and consistent identity-based microsegmentation capability is then provided from the user to the application.
Experience ACI Integrations for Yourself
To practice using Cisco ACI, we’ve put together two-minute walkthroughs to help you experience the impact of the integrations and see first-hand how they can make an IT team’s life easier.
Watch how Cisco Cloud ACI helps policy-driven connectivity between on-premises data centers and AWS and Azure public clouds. The aim is to simplify routing and to ensure consistency of network security policies, ultimately helping to meet compliance demands.
Learn how to correlate application health and network constructs for optimal app performance, deeper monitoring, and faster root cause analysis with Cisco ACI and AppDynamics integration.
See how Cisco ACI and Cisco DNA Center/ISE policy integration allows the marrying of ACI’s application-based micro-segmentation in the data center with Cisco SD-Access and user group-based segmentation across the campus and branch.
Source: Cisco.com