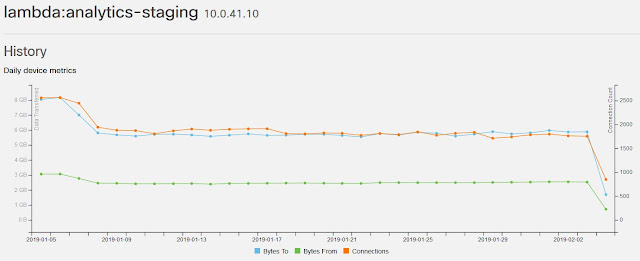
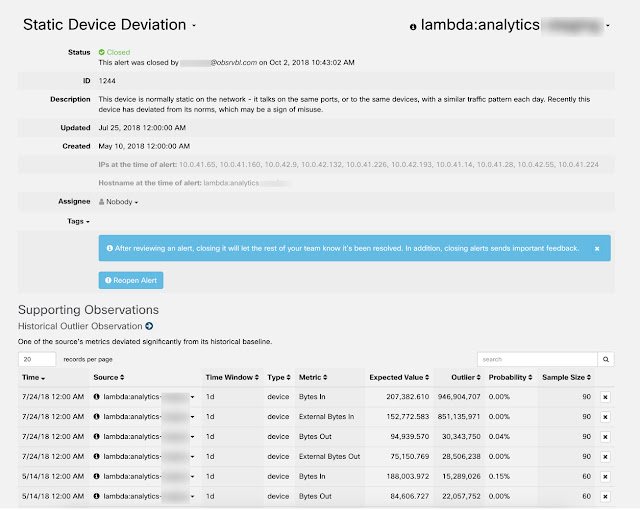
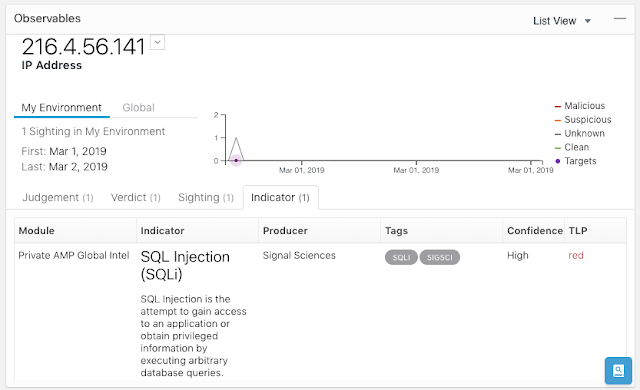
We just finished working with the analyst firm Analysys Mason on a white paper exploring the factors behind successful automation projects. They talked to a number of tier 1 operators to capture lessons learned from the rollouts of their respective automation projects. The white paper is more focused on process than technology and I think it’s a worthwhile read for anyone embarking on any automation project.
Automation projects tend to inspire an equal mix of excitement and fear and folks often come to us for advice on what to do. Unfortunately, there is no one right answer to this; however, as the white paper establishes, there are a few guiding principles to keep in mind:
◈ Automation is not a “Big Bang” endeavor. Successful companies view their automation initiatives as a series of discrete steps. Like a staircase, each step builds upon the ones before it to increase scope and capabilties of the whole over time.
◈ Each step should have its own payoff, be it cost savings, increased efficiency or something else. Having a backloaded payoff after several years of effort is seldom a great idea for a few reasons: 1) at some point, your leadership is going to wonder why they are spending money on a project with no apparent payoff, 2) your team will get tired of the churn, also with no apparent payoff, and 3) the needs of the organization will inevitably evolve and change and your initial plan will likely be dated in under a year. Instead, view your overall automation objective as a series of individual steps and make sure each step has tangible, measurable outcomes. At the completion of each step, use what you learned along the way to re-asses the whole project. By doing this, you gain credibility by showing the project is doing what you said it would do, your leadership is happy that they are seeing a return on their spend, your teams’ lives are getting better in measurable ways and they feel like their value to the company in growing, and you can be sure you are never too far out of sync with the business strategy.
◈ Of the three components of the infamous people, process, technology triangle, “technology” is probably the most straightforward. A successful project is also going to entail investing in your teams’ skills. It’s critical to remember this is a non-compressible process: while you can install new tools in a matter of hours, your team can only absorb and operationalize new technologies at a given rate and you need to take that into account in your plans. In addition, you need processes that can be automated: spaghetti logic, gappy processes and disparate ways of doing the same task are all going to create friction in your quest to automate. The good news is that an automation initiative is an excellent excuse to clean these all up as they are currently hurting your business whether you automate or not. Again, allow time to do this: if you get three engineers in a room, you will have four opinions on how a task should be accomplished.
◈ Recognize that there is no one true path to automation. Look at the image below. Some folks will follow the green line and focus on automating technical domains (i.e. data center networking, firewall policy) and then eventually stitch them all together. Others will focus on automating specific business processes (i.e. auto-scaling video delivery, new employee on-boarding) and plan to eventually cover all the company’s activities. Both approaches offer immediate benefits and both have longer-term implications. Neither is right nor wrong, it’s simply which a matter of which approach best matches the needs of the company at the time.
Finally, and perhaps most importantly, it’s OK to try things and it’s OK if every step is not a complete success—it’s how you are going to learn. Internalize this but also set the expectation with your team and your leadership. Learn things and adapt. Expect to change tack–while the green and blue lines are nice and neat and look good on slides, reality more likely looks like the grey line going down the middle!
Automation projects tend to inspire an equal mix of excitement and fear and folks often come to us for advice on what to do. Unfortunately, there is no one right answer to this; however, as the white paper establishes, there are a few guiding principles to keep in mind:
◈ Automation is not a “Big Bang” endeavor. Successful companies view their automation initiatives as a series of discrete steps. Like a staircase, each step builds upon the ones before it to increase scope and capabilties of the whole over time.
◈ Each step should have its own payoff, be it cost savings, increased efficiency or something else. Having a backloaded payoff after several years of effort is seldom a great idea for a few reasons: 1) at some point, your leadership is going to wonder why they are spending money on a project with no apparent payoff, 2) your team will get tired of the churn, also with no apparent payoff, and 3) the needs of the organization will inevitably evolve and change and your initial plan will likely be dated in under a year. Instead, view your overall automation objective as a series of individual steps and make sure each step has tangible, measurable outcomes. At the completion of each step, use what you learned along the way to re-asses the whole project. By doing this, you gain credibility by showing the project is doing what you said it would do, your leadership is happy that they are seeing a return on their spend, your teams’ lives are getting better in measurable ways and they feel like their value to the company in growing, and you can be sure you are never too far out of sync with the business strategy.
◈ Of the three components of the infamous people, process, technology triangle, “technology” is probably the most straightforward. A successful project is also going to entail investing in your teams’ skills. It’s critical to remember this is a non-compressible process: while you can install new tools in a matter of hours, your team can only absorb and operationalize new technologies at a given rate and you need to take that into account in your plans. In addition, you need processes that can be automated: spaghetti logic, gappy processes and disparate ways of doing the same task are all going to create friction in your quest to automate. The good news is that an automation initiative is an excellent excuse to clean these all up as they are currently hurting your business whether you automate or not. Again, allow time to do this: if you get three engineers in a room, you will have four opinions on how a task should be accomplished.
◈ Recognize that there is no one true path to automation. Look at the image below. Some folks will follow the green line and focus on automating technical domains (i.e. data center networking, firewall policy) and then eventually stitch them all together. Others will focus on automating specific business processes (i.e. auto-scaling video delivery, new employee on-boarding) and plan to eventually cover all the company’s activities. Both approaches offer immediate benefits and both have longer-term implications. Neither is right nor wrong, it’s simply which a matter of which approach best matches the needs of the company at the time.
Finally, and perhaps most importantly, it’s OK to try things and it’s OK if every step is not a complete success—it’s how you are going to learn. Internalize this but also set the expectation with your team and your leadership. Learn things and adapt. Expect to change tack–while the green and blue lines are nice and neat and look good on slides, reality more likely looks like the grey line going down the middle!