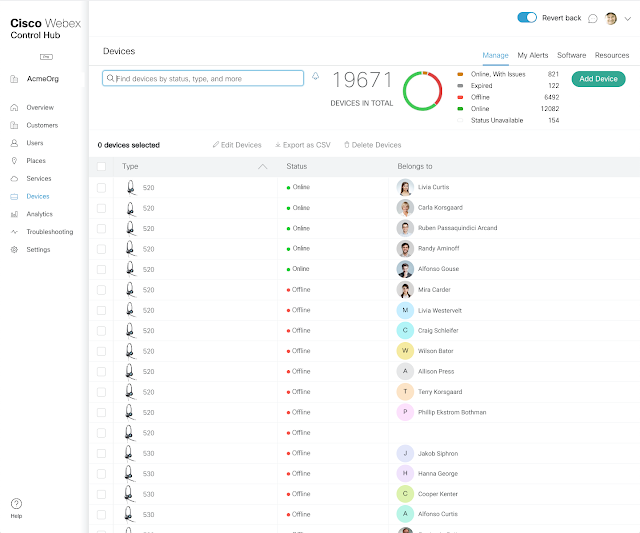
“I need the business agility, flexibility, and speed of new feature delivery that cloud offers while protecting my contact center investments.”
“I need to modernize my customer and agent experiences to remain competitive.”
“I need easy access to cloud-based applications that work seamlessly with my on-premises contact center infrastructure”
You’re not alone! Many of our customers across the globe and from many industries have shared with us their struggle to balance the need for innovation with cloud-based capabilities powered by artificial intelligence (AI) to stay competitive while maximizing their valuable on-premises contact center investments in people, process, and technology.
They’ve expressed their desire for an open and secure platform that gives them reliability and business continuity, with new flexibility and agility needed to meet the ever-changing demands of their business. And they’re looking for unique ways to create differentiated experiences for both their employees and customers that will result in better customer experiences, repeat business, and improved performance of their contact center.
Cisco is addressing these needs with Release 12.5 – our latest software for Unified Contact Center Enterprise, Packaged Contact Center Enterprise, Unified Contact Center Express, and Hosted Collaboration Solution for Contact Center. We’re introducing some exciting new capabilities designed to simplify how you manage your contact center, make your agents more productive, and create better experiences for your customers.
◉ Webex Experience Management (formerly CloudCherry), our new customer experience management solution, is integrated into the Cisco agent desktop providing agents and supervisors with customer sentiment, journey insights, and feedback metrics in real-time.
◉ An intuitive conversational IVR, powered by Google Dialogflow improves customer self-service experiences over the phone by easily adding modern speech interfaces to existing self-service options.
◉ Customer Journey Analyzer, our cloud-based advanced analytics reporting solution is now available for trial to all our on-premises contact center customers.
◉ AI-based Voicea call transcript and summary are also available for trials to improve agent productivity, call wrap-up and accuracy of action items.
◉ Smart Licensing provides a simple, automated way to add/activate new software licenses to keep up with fluctuating interaction volumes.
“I need to modernize my customer and agent experiences to remain competitive.”
“I need easy access to cloud-based applications that work seamlessly with my on-premises contact center infrastructure”
Do These Challenges Sound Familiar?
You’re not alone! Many of our customers across the globe and from many industries have shared with us their struggle to balance the need for innovation with cloud-based capabilities powered by artificial intelligence (AI) to stay competitive while maximizing their valuable on-premises contact center investments in people, process, and technology.
They’ve expressed their desire for an open and secure platform that gives them reliability and business continuity, with new flexibility and agility needed to meet the ever-changing demands of their business. And they’re looking for unique ways to create differentiated experiences for both their employees and customers that will result in better customer experiences, repeat business, and improved performance of their contact center.
Cisco is addressing these needs with Release 12.5 – our latest software for Unified Contact Center Enterprise, Packaged Contact Center Enterprise, Unified Contact Center Express, and Hosted Collaboration Solution for Contact Center. We’re introducing some exciting new capabilities designed to simplify how you manage your contact center, make your agents more productive, and create better experiences for your customers.
Highlights of What’s New
◉ Webex Experience Management (formerly CloudCherry), our new customer experience management solution, is integrated into the Cisco agent desktop providing agents and supervisors with customer sentiment, journey insights, and feedback metrics in real-time.
◉ An intuitive conversational IVR, powered by Google Dialogflow improves customer self-service experiences over the phone by easily adding modern speech interfaces to existing self-service options.
◉ Customer Journey Analyzer, our cloud-based advanced analytics reporting solution is now available for trial to all our on-premises contact center customers.
◉ AI-based Voicea call transcript and summary are also available for trials to improve agent productivity, call wrap-up and accuracy of action items.
◉ Smart Licensing provides a simple, automated way to add/activate new software licenses to keep up with fluctuating interaction volumes.
Integration with Webex Experience Management (formerly CloudCherry)
Our new AI-powered, cloud-based customer experience solution can be integrated with your contact center via two new agent desktop gadgets. The solution enables contact centers to capture customer feedback utilizing an easy-to-use survey designer. Once feedback is captured, agents have the ability to view customer feedback scores within their agent desktop via the new Customer Experience Journey gadget, giving them real-time visibility into customer sentiment and past journey experiences so they can truly understand how the customer is feeling and be able to personalize their interaction with the customer. The Customer Experience Analytics gadget displays the overall pulse of customer feedback through industry-standard metrics, such as NPS, CSAT, and CES.
Innovative AI-Powered Self-Service
Our Cisco Unified Customer Voice Portal leverages Google Dialogflow, allowing AI to bring speech-to-text, NLU-based intent detection, and text-to-speech capabilities to create an efficient conversational self-service experience for your customers while relieving agents of simple and repetitive tasks.
Business Insights via Cloud Analytics
Bringing the power of cloud analytics to all Cisco on-premises contact centers, Customer Journey Analyzer provides advanced out-of-the-box reporting, arming contact center managers with historical data from multiple contact center deployments to generate specific business views across the business. It displays trends to help supervisors identify patterns and gain insights for making continuous improvements, and it includes an Abandoned Contacts dashboard to identify where customers are abandoning the journey so that appropriate and proactive actions can be taken. Available for trial now.
Voicea Call Transcript
We’ve created a new Cisco agent desktop gadget that uses our very own Voicea AI, leveraging accurate speech-to-text technology to provide a complete transcription of the interaction between agent and customer. This exciting new feature, which is available now for field trial with Cisco Unified Contact Center Enterprise, simplifies call wrap-up and helps agents accurately capture the details of the conversation, improving call continuity and agent productivity.
Licensing Made Simple
Smart Licensing enables contact centers to remain agile and quickly add/activate new software licenses to keep up with fluctuating interaction volumes. Using the Cisco Smart Software Management Portal, our customers can easily see in real-time how many total licenses they have and how many are in use, giving them peace of mind and an accurate measure of their license inventory.
Improved Agent Experience
We’re making your agents more productive and their experience more intuitive with new keyboard shortcuts, drag and drop desktop gadgets, and the ability to update call variables during interactions. Agents can also view their statistics in real-time now.
Secure and Scalable
Our new release also includes a variety of security-related enhancements that further harden the solution against potential vulnerabilities. At the same time, we continue stretching scale limits by doubling outbound calls per second and total supported dialer ports, and 2.5 times increase in simultaneous active campaigns.
All Our Customers Benefit
I’m excited about how the cloud brings all these enhancements to our on-premises customers. Our goal continues to be to bring all our customers the latest technological innovations available today, regardless of whether they own their contact center system or subscribe to it as a service, and to give them a practical and simple path to the cloud at a pace that’s just right for them.