Digital transformation initiatives are driven by the desire to make data-driven business decisions. Whether you’re looking to increase production, reduce waste, or improve safety, the answer resides in your data: collecting it, analyzing it, and learning from it. But what happens when your data lives in extreme locations? Perhaps in places of severe heat, cold, humidity, salinity, or dust? How do you gather information with such harsh conditions? And how do you do it securely?
The first step is to converge to a single IP network. Network convergence is a proven formula for pulling together all the data in your environments. Cisco has been helping hundreds of thousands of organizations to converge their voice, video, data, and IoT networks to a single IP network. We’ve been doing this for over 30 years, and we know it works. A single network is easy to manage and operate and reduces your total cost of ownership. However, the primary challenge with a converged network is that it needs to be secure. There are three elements you need to securely connect an industrial network: 1) purpose-built hardware, 2) digitally signed and authentic security software, and 3) extensible architectures.
1. Choosing the right hardware
Start with the right hardware. For industrial internet of things (IIoT), the network hardware must satisfy the requirements of both the operational technology (OT) department and the IT department. At a high level, OT runs point on operations and understands how the organization produces its goods or services. IT connects the network and wants to make sure it’s done securely. OT and IT each have different priorities, goals, and concerns, yet the hardware has to meet both sets of requirements.
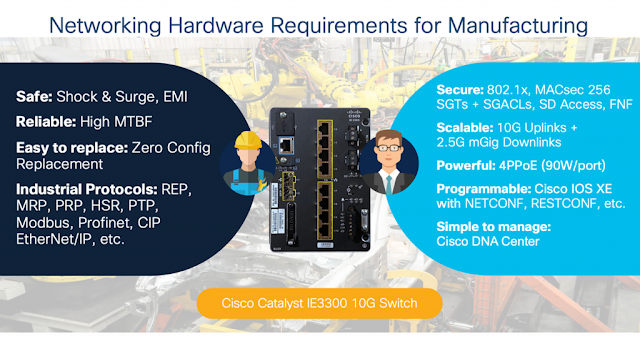
In addition to meeting the requirements of both OT and IT, the network hardware you select for connecting the industrial network should have a hardware trust anchor. A hardware trust anchor ensures that whatever software runs on the hardware will do so in a secure manner. To this end, the hardware should have an anti-theft, anti-counterfeiting, and anti-tamper chip that is completely immutable, meaning that it cannot change. Also look for built-in cryptography functions, secure storage for certificates and objects, and certifiable entropy for random number generators.
2. Selecting the right software
Going up the technology stack, the next component you need to securely connect the industrial network is the right software. Complement the secure hardware with digitally signed images, a secure boot process, and runtime defenses to ensure the software is secure and hasn’t been tampered with.
What is meant by digitally signed images? When we compile an image at Cisco, we execute a hash function on the binary code. The result of that hash function is encrypted using Cisco’s private key, and that signature is embedded right within the software image. At boot time, two things happen: 1) the local machine computes its own hash based on the binary of the software image, and 2) it decrypts the information they’re in, looking for that signature and making sure the two match. This process provides reassurance that the software hasn’t been tampered with and that it’s safe to boot up. Digitally signed images are an important component to a secure boot process.
Now that the software has securely loaded on the device, the network administrator has at his or her disposal the most powerful and secure networking operating system in the industry: Cisco IOS XE, which contains over 1,300 security feature commands and keyword options.
Cisco IOX XE also supports application-hosting in containers so that they can run on networking devices. Leveraging this application-hosting capability, Cisco has recently delivered an OT-specific security solution, namely
Cisco Cyber Vision.
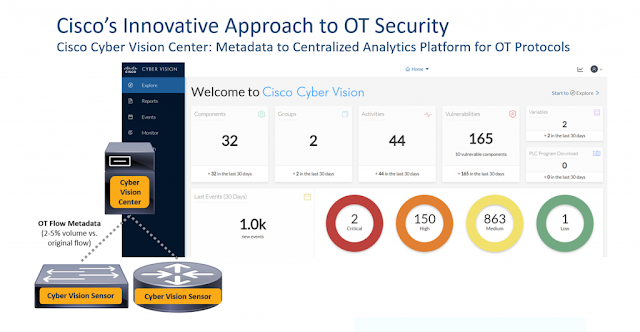
Cisco Cyber Vision provides innovation in OT security. For example, Cisco doesn’t require customers to install dedicated hardware sensors, but rather virtualizes their sensor to run as an application on network infrastructure, such as Cisco Catalyst Industrial Ethernet (IE) switches or Cisco ISR Industrial Routers (IR) or even Cisco Catalyst 9300 switches (which may be found in some industrial environments, albeit in temperature-controlled cabinets/rooms). Cisco’s unique approach of using a software sensor for OT protocols is not only an industry-first, but also the most scalable solution in this space, as it allows for the security solution to simply scale with the network infrastructure itself.
Another innovation that Cisco brings to OT security is the use of distributed analytics and OT flow metadata to minimize bandwidth impact. The Cyber Vision sensors running on the network devices perform deep packet inspection (DPI) on all OT flows. However, rather than mirroring these flows to a central analytics engine (i.e. the Cisco Cyber Vision Center) these sensors summarize OT flows as metadata, similar to NetFlow records (though the metadata Cyber Vision uses far exceeds the data contained in NetFlow records). Cisco Cyber Vision goes beyond NetFlow by detailing attributes of the devices sending and receiving the flows, the OT protocols used, the commands sent and received, and even the specific variables that these commands reference. As an analogy, while NetFlow can tell you who is talking to who, Cyber Vision metadata can tell you not only who is talking to who, but also the languages they are speaking, as well as specific details of their conversation. And the summary of these flows is highly efficient, typically consuming only 2-5 percent of incremental bandwidth.
3. Architectural integrations
The third piece in the tech stack is architectural integrations. Look for security solutions that leverage the existing network hardware to provide visibility into network traffic, and to identify and stop potential threats. Both IT and OT can benefit from having complete visibility of the OT environment, but IT cannot afford the operational overhead required to support a separate SPAN network. By integrating sensors into network hardware, IT can see anomalous behavior anywhere in the environment, while OT can obtain new and deeper insights into operations.
Ideally, the security solution also integrates with the technology used by the Security Operations Center (SOC) to monitor, investigate, and remediate security incidents in the IT environment. This way, the SOC has all the information it needs in one location to reduce the time to detect and respond to a security incident. Security analysts can see, for example, whether an attack originated in the IT environment and moved laterally to the OT environment, or if an attack entered the OT environment via something like a vulnerable device.
How Cisco can help
Cisco’s industrial-grade network hardware and
Cisco Cyber Vision are designed to work together to meet the three requirements for securely connecting an industrial network. Our ruggedized networking switches and routers are built to withstand the harshest environmental conditions while delivering enterprise-level networking capabilities, including a hardware trust anchor. Our software uses digitally signed images to validate that software has not been tampered with, and Cisco Cyber Vision leverages the network architecture to deliver visibility and control over the OT environment. Cyber Vision also provides real-time threat detection and integrates with the SOC.