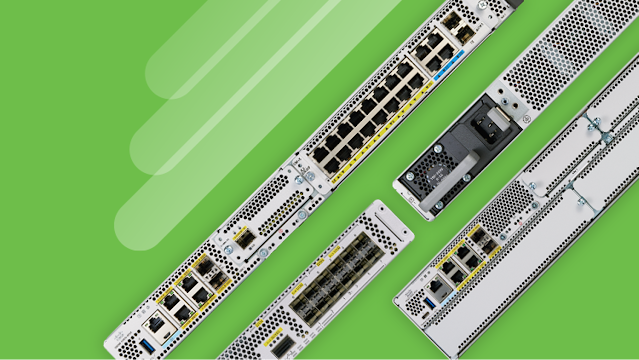
On October 20, Cisco announced the new Catalyst 8000 Edge Platforms Family, to help customers deliver secure connectivity to hybrid and multicloud applications across cloud, data center and edge locations. The new Portfolio transforms the WAN edge so customers have secure access, agility and the best experiences when connecting to applications anywhere. These new platforms support customers’ move to a SASE architecture by converging cloud-managed SD-WAN and cloud-delivered security (Cisco Umbrella) into one solution. Customers will also have access to the full SD-WAN security stack for on-prem deployments.
As part of launching the new Catalyst 8000 family, I’ve had the opportunity to talk to a number of industry analysts, media, channel partners and customers. I would like to address a few questions that have come up in my briefings.
With the new Catalyst edge platforms, we are meeting the requirements of the WAN edge, and providing another foundational piece of our intent-based network strategy that spans every domain of the network.
Cisco launched its Intent Based Networking (IBN) initiative targeted for enterprises a few years ago. This initiative was meant to address the complexity that spans campus, wireless and WAN, by transforming the usually static network fabric into a controller-led architecture that captures business intent and translates it into policies that can be automated and applied consistently across the network. The programmability of the fabric combined with integrated analytics allows it to be agile and elastic to help deliver desired business outcomes.
The Catalyst 8000 family was given the “Catalyst” name because as we continue to grow and build upon our intent-based networking (IBN) portfolio it is important that there is product, branding and messaging alignment across Access (LAN) and WAN and that customers view the IBN portfolio as a set of products that unify their enterprise networks and provide software-defined capabilities via a common IOS-XE operating system. With the new naming, the Catalyst brand is now part of the Intent Based Portfolio along with Catalyst Switches and Catalyst APs.
Why is the new portfolio called an Edge device and not a Router?
Enterprise WANs have transformed over the last decade. As Enterprises across various industry segments are looking at digitalization for gaining business advantage, Cloud, IOT, 5G and Edge Compute are quickly becoming key pillars of their digitalization strategies.
The WAN edge hence has become critical to digital businesses, particularly the edge of the WAN where the traditional black-box router no longer serves the needs of the modern enterprise. Speeds and feeds remain important, but today’s networks require a WAN edge platform that is agile, flexible, and open to host multi-service edge functionality.
We are calling these devices “edge platforms” versus “routers” because the definition of a router has evolved over the past few years to be more of a WAN edge device; providing connectivity from distributed locations to both data centers and the cloud, service flexibility for on-prem or cloud deployments as well as containerized hosting of local network services and business applications.
How is a new hardware portfolio a relevant, differentiator, when the WAN world is going software-defined?
With its IBN initiative, Cisco has significantly inverted its development model to be a software led model first with user experience as a key focus area.
The Catalyst 8000 family includes the Catalyst 8000V Edge Software, a virtual platform for anyone that wants to deploy Cisco routing as a virtual network function (VNF) on a general-purpose hardware or in cloud deployments. For environments outside of cloud, our customers, however, prefer a customized solution from Cisco to deliver software innovations for better performance, scale, security, reliability, and flexibility.
High-end aggregation deployments need performance and scale which cannot be fulfilled with a general-purpose CPU architecture. Cisco’s investment in the custom ASIC (QuantumFlow Processor 3.0) allows us to deliver industry leading performance, SD-WAN tunnel scale, and 40/100G interfaces in a compact, one rack unit form factor for the Catalyst 8500 Series Edge Platforms.
In keeping with the industry trend, Cisco’s access portfolio leverages an x86 architecture that gives us flexibility to run containerized services, while also providing the choice of connectivity and flexibility much needed in a global deployment. The new Catalyst 8300 Series Edge Platforms provide 70+ different interface choices including network interface cards, cellular interface cards, voice modules (industry’s only SD-WAN solution that offers support for IP telephony), switch modules, service modules as well as an edge compute module to host local apps and service VNFs. This flexibility is much needed in customer environments to address a variety of deployment needs.
The hard reality of today’s deployments are that most SD-WAN vendors focus on the software functions of building WAN overlays but have been missing out on addressing the underlay needs – variety of interfaces, transport choices with associated protocols, performance, scale, flexibility to add services. Thus, these solutions often end up becoming an add on to an existing Cisco router for the underlay. This adds cost to the overall solution which is often missed in the analysis.
In closing, with the Catalyst 8000 Edge Platforms Family, we are helping you adapt to the requirements of the new WAN edge and providing another foundational piece of our intent-based network strategy that spans every domain of the network — campus, branch, WAN and DC/cloud. The Catalyst 8000 family is the best-in-class platform for SASE, SD-WAN, and 5G in the future; built to address today’s most pressing WAN edge issues, and flexible enough to tackle the challenges of tomorrow.