The Cisco IoT Operations Dashboard provides operations teams with a centralized, cloud-based dashboard to securely deploy, monitor, and troubleshoot device connectivity. Using this secure connectivity as a foundation, that same dashboard then enables you to extract, transform, govern and deliver data from IoT edge devices to the cloud with Cisco Edge Intelligence, install and manage your containerized edge applications and to deploy a broad range of industrial IoT sensors with Cisco Industrial Asset Vision.
Thursday, 21 October 2021
Secure and Simplify Your Programmable Edge and Industrial Sensors
Tuesday, 19 October 2021
Cisco IT accelerates its transformation with CX Cloud
As any CIO with a digital transformation agenda can attest, success relies upon establishing clearly defined objectives for each step of the journey – with visibility into the entire IT infrastructure. Also critical is the ability to receive the right information at the right time to help achieve desired outcomes faster. This was especially true during the pandemic when, for example, Cisco enabled – within 10 days – 140,000 employees and partners to work from home.
In Cisco IT, we’re meeting these goals with CX Cloud – a one-stop destination that combines Cisco expertise and best practices with telemetry, AI-/ML-driven insights, use cases, and contextual learning. This cloud-based Software as a Service (SaaS) portal is smoothing the bumps in our digital journey by removing complexity, filling skills gaps, and ultimately accelerating technology adoption.
It accomplishes this by providing:◉ Full visibility into all of our network assets and contracts
◉ Automated risk detection and mitigation
◉ Actionable data and insights
◉ Ready access to targeted learning resources and expertise, and much more
Let’s take a closer look at how we’re leveraging these and other CX Cloud capabilities to benefit our business.
‘Single source of truth’ with 360-degree insights
CX Cloud provides a secure, single source of truth that enables full visibility of our 100,000-plus IT assets (see Figure 1). CX Cloud’s telemetry ensures we always have the latest information pertaining to purchased and connected assets, security advisories, support cases, and individual success tracks.
Because we now have all of our asset information and security advisories in one place, our engineers no longer need to build reports manually or reconcile across platforms. As a result, they expect to boost their efficiency and improve their operational scale by 50 to 60 percent, allowing them to spend more time on innovation. The bottom line: We’re accomplishing much more with the same number of people.
CX Cloud also lets us keep track of on-premises and cloud-based infrastructure across multiple deployments — with tools to search, filter, and see a 360-degree view of an asset’s hardware and software details. We can access contract and coverage details with key support milestones, while also receiving on-demand diagnostic scans and updated advisories.
Timely expertise with quick resolution and enhanced security
Speedy resolution and simplified case management
Minimize risks with tailored recommendations and insights
Sunday, 17 October 2021
Create, Document, and Share Live Code Examples with Jupyter Notebook
Q: How do you eat a whale?
A: One bite at a time… or so the saying goes. Admittedly, I don’t know of anyone who eats whale one bite at a time (or any way otherwise for that matter). But we can all agree that breaking large problems into smaller pieces is a valuable arrow in the quiver of problem-solving techniques. It’s a practice that certainly applies in the world of programming.
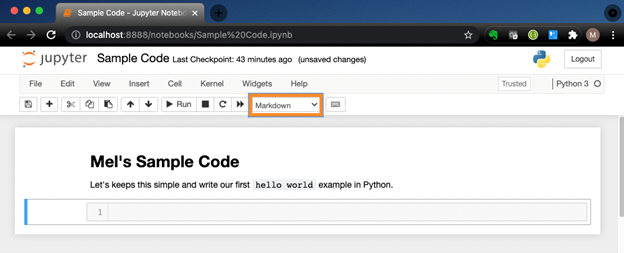
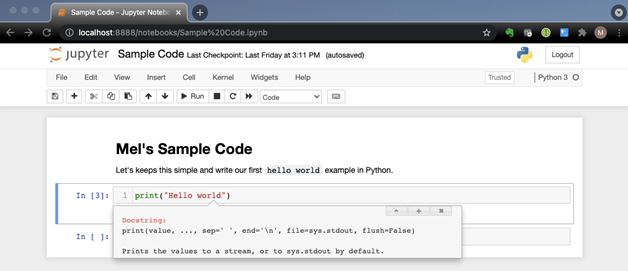
Once the problem is broken down and implemented, however, how can we convey what we learned to others? One way is using Jupyter Notebook to combine documentation authored in markdown together with live code. As an example, a developer writes small blocks of Python to vet an algorithm, a function, or syntax. Once verified, it is documented, saved, and the code is then added to the IDE, such as VSCode, where the main Python code is developed.
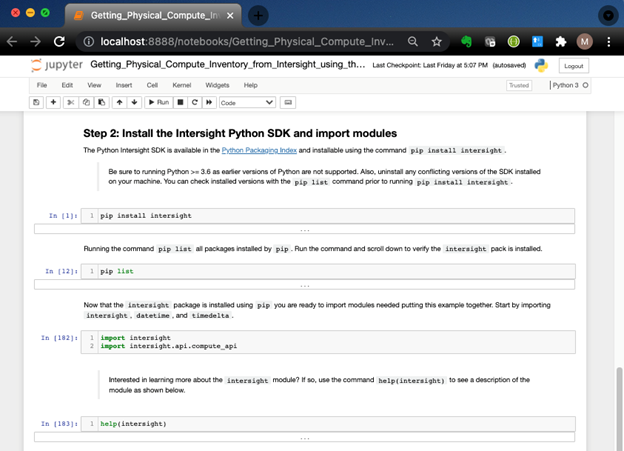
This post shows a simple Python example that retrieves physical compute inventory claimed in Cisco Intersight. In this example, the items in the inventory are UCS X-Series compute nodes managed by IMM (Cisco Intersight Managed Mode).
What is Jupyter Notebook?
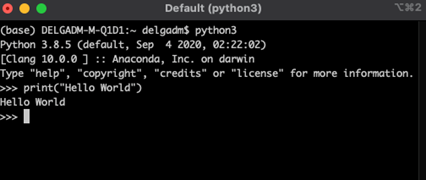
Jupyter Notebook is an open-source web application used to create and share code along with narrative text. It’s used extensively in academia especially by data scientists. If you have experience with Python you may be familiar with IDLE (see the screenshot below). IDLE lets you execute Python code directly from the command line without needing to run a *.py file. You run your line(s) of code and verify things work and when you are finished, you close your session with <cntrl><d> and you move on with life. What if you wanted to share what you tried with someone else? Assuming you copy/pasted the contents of your shell session, would someone else be able to understand what the flow of what you were trying? Could you refer to it later and understand the flow of what you did?
How Jupyter Notebook works – A very simple tutorial
Show Me a Real-World Example
Documenting and Executing Code
Saturday, 16 October 2021
Flexible Hybrid Cloud Networking with Infrastructure as Code and Cisco Nexus Dashboard
Applications are becoming the most visible aspect of an organization’s brand. The performance, usability, and reachability of branded apps are of utmost importance since they are a primary interface to customers. To keep up with evolving customer expectations, developers and operations teams are rapidly adopting design patterns using containers and microservices for continuous integration and continuous delivery (CI/CD). In order to enable these innovations to deliver a competitive customer experience, IT relies more and more on a hybrid cloud model.
The enterprise cloud network—including the WAN—keeps application components securely connected and operating in a predictable and performant way. In this sense, the network is an intrinsic part of modern application design and plays an essential role in maintaining KPIs that protect the brand as customers depend on applications to accomplish their daily tasks, including essential services where availability is crucial. Being able to safely automate workflows and have deep visibility into the cloud network, compute infrastructure, and applications has always been a critical need for IT organizations—and even more so in the new hybrid world.
But Hybrid Cloud Gets Challenging
Deploying applications in the cloud is relatively simple for new cloud-native applications. According to IDC research, to gain business agility, enterprises are committing to modernize more than half of their existing applications by 2022, leveraging cloud-native application architectures as a means of achieving their goals.* That’s a significant portion of existing application deployments. For many organizations refactoring these applications to a cloud-native foundation will include integration with exisiting data center services and data repositories, while taking advantage of embedded security policies to protect payment and personal information. This is accelerating the rise of hybrid applications.
The transition to hybrid-cloud introduces new challenges, like the many individual services on a smart watch pulling data from a plethora of sources, but hyper-scaled to serve millions of clients. Established services in an on-premises data center need to be easily accessible to cloud application containers, such as when a cloud-native shopping cart needs to access the payment information on the PCI island in the private data center. The entire communication path needs protection with guaranteed levels of service.
Hybrid cloud requires a simple-to-use, centralized cloud networking platform built to support multiple operator personas—NetOps, DevOps, and CloudOps—to manage a constantly changing constellation of services, data sources, and connections. Historically, provisioning a new application required a handshake between DevOps and NetOps, with NetOps configuring the network before DevOps could deploy the application. This was a manual, error prone process, assuming static dependencies, thus reducing the velocity of change. Thankfully, the increasing adoption of Infrastructure as Code (IaC) tools is helping automate and simplify management of the complex interactions among data centers, hybrid-clouds, networks, and compute infrastructure.
Infrastructure as Code Is the Operational Link Between DevOps and NetOps
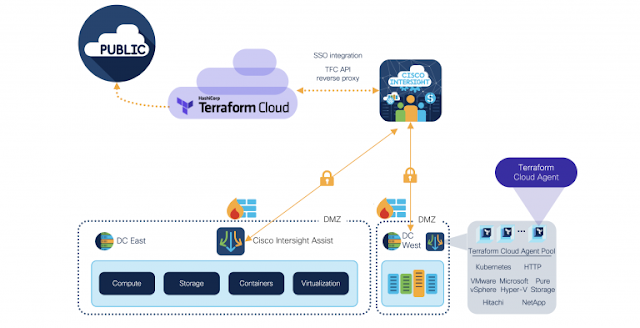
IaC automation capabilities are critical for DevOps teams for automating provisioning of cloud infrastructure. DevOps teams can rely on a consistent automation model for infrastructure and workloads across the edge, co-locations, data centers, and public clouds. Depending on the desired outcome, IT teams can leverage IaC tools such as HashiCorp Terraform and Red Hat Ansible, interacting with either Cisco Nexus Dashboard for managing cloud networking services or through Cisco Intersight to manage compute resources.
NetOps can now expose infrastructure services for consumption by the DevOps and CloudOps teams via the Cisco Nexus Dashboard. Using HashiCorp Consul Terraform Sync with Nexus Dashboard, DevOps can directly drive the infrastructure changes needed for application deployment and management while enabling NetOps to monitor the progress in real time, across the global infrastructure. This is made possible by the automation capabilities of Cisco Nexus Dashboard enabling rapid deployment of services, CI/CD pipelines, and seamless collaboration between DevOps, CloudOps, and NetOps.
Take, for example, a Development Team working with the Nexus Dashboard owner to package connectivity permissions for a hybrid-cloud application in an IaC Plan/Playbook. NetOps can use Nexus Dashboard to define the secure connections needed for the application to function among clouds and on-premises services—and only those services. This alleviates the need for DevOps to define and keep track of the network permissions needed for the application. DevOps can make functional changes to a Plan/Playbook using the existing infrastructure and connectivity requirements or NetOps can add new resource connections as needed for updates.
Learning the Ways of IaC for Network Operations
Working Together with Cisco Nexus Dashboard and Cisco Intersight
Thursday, 14 October 2021
Emerging trends in IoT gateway and edge application management in a cloud native paradigm
The COVID-19 pandemic has thrust the world into an era of massive digital business transformation across industries like manufacturing, utilities, smart cities, oil and gas, and transportation. To meet these new challenges and keep business operations running smoothly, we need cost-effective solutions. Traditionally, IoT solutions were typically used to reduce operational expenses and increase operational equipment efficiency (OEE). With the onset of the pandemic however, the need for managing business operations remotely across these IoT verticals has increased rapidly. This has led to a sudden, unprecedented shift towards an increased adoption of cloud native IoT management applications hosted by public cloud providers in partnership with IoT SaaS vendors. An example for such a use case is remotely managing operations of IOT gateways and edge compute applications deployed on a manufacturing floor. This migration from having personnel onsite managing and accessing devices, IoT gateways, and edge compute applications to remote cloud based management brings a new set of IoT security challenges that are primarily seen in a cloud native application. While cloud native applications are considered reasonably secure in general, there is still room for improvement. Containers, orchestrators, and APIs present in an application’s surrounding infrastructure represent new attack surfaces. In addition to the cloud service itself, each of these layers has an array of user-defined configuration settings intended to help users apply their security policies. This manual configuration is often fraught with opportunities for user error and misconfiguration, opening the IoT applications to potential security attacks.
In addition, new technology and architectural trends are emerging within the functionality of IoT management applications. These new trends change the way gateway management, security, and network management is done for IOT networks. They also alter how edge compute applications run on IoT gateways and integrate with public cloud-based platforms like Amazon Web Services, Microsoft Azure, and Google Cloud. In this technical blog we will discuss some of the emerging architectural trends in the IoT industry. They are classified as the six critical pillars of cloud native IoT management application in a hybrid cloud and multi cloud environment:
◉ Compute scalability
◉ High frequency data processing
◉ Low latency data processing
◉ Robust data processing pipeline
◉ Variety of IoT protocols
◉ Cloud native IoT messaging service
We will discuss these six critical pillars further in detail, but first let’s look at the challenges they are solving.
Challenges of distributed edge IoT data infrastructure
Distributed edge computing makes sense for a variety of use cases in IoT applications. Consider the following challenges with a cloud native integration for the distributed IoT edge:
◉ Bandwidth – traditionally the available WAN network bandwidth is a focus for data centers. However, this focus will shift towards IoT edge computing use cases as many distributed edge IoT deployments emerge.
◉ Latency tradeoff – some IoT use cases would experience increased latency if data processing happened in a cloud or fog layer and there should be a tradeoff to do it in a distributed edge paradigm.
◉ Heterogeneity– in a cluster of gateways deployed at the edge, heterogeneous compute capability of these individual gateways could affect the overall efficiency by adding dissimilar components to handle tasks for the edge compute scenario.
◉ Transparency– conceals the separated components in a distributed edge network to allow the disparate pieces to work in sync.
◉ Concurrency– allows several IoT clients to access shared resources at the edge, which creates concurrent access related problems.
◉ Security– is simpler when all compute resources are consolidated in a centralized data center but not in a distributed edge as in IoT network architectures.
◉ Backup – of dispersed IoT data requires new data protection strategies in a distributed edge IoT to cloud data pipeline paradigm.
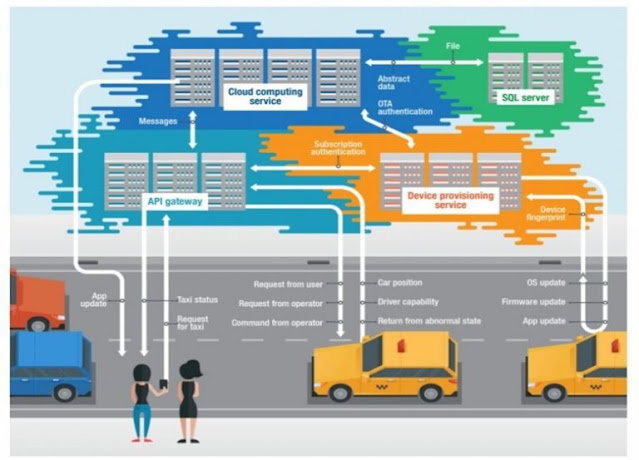
5G enabled IoT applications require a highly dynamic response from the end to end IoT system, which creates the need for a distributed event driven edge compute service. To meet these demands, IoT application developers need a flexible and agile development environment like the cloud native approach to quickly create event driven edge compute applications running on IoT gateways. However, introducing such a cloud native approach can come with its own challenges. Take for example fleet management use cases. IoT gateways are deployed on vehicles for continuous monitoring of GPS location, collecting telemetry, and other diagnostic health information. Adding an additional distributed event processing component at the edge for communicating to a cloud native IoT application to manage these gateways could lead to an increased latency, which may eventually create OT operational issues for the end customer. Therefore, it is very important to design the edge application in a resilient and robust manner. Cisco Edge Device Management offers such capability to seamlessly integrate with Cisco IoT Operations Dashboard.
Real-world cloud native IoT illustration of transportation use case
Cisco IR829 Industrial Integrated Services Routers, Cisco Catalyst IR1100 Rugged Series Routers, and Cisco Catalyst IR1835 Rugged Series Router
Possible solutions
Cisco IoT architectural solution
Key takeaways
Saturday, 9 October 2021
Cisco 200-201 CBROPS Exam: How to Succeed and Advantages
Have you been seeking an opportunity to have your skills recognized and approved? If yes, then you have landed on the right webpage. Get the acknowledgment you have always desired by earning the relevant certification. Get your Cisco CyberOps Associate 200-201 certification, and you can prove to your peers and organizations that you can stay abreast and stay current with your job position.
Taking the Cisco 200-201 CBROPS exam is proven to get essential skills to work in the Cisco Cybersecurity Operation domain. The applicants for this exam are the IT professionals who are accountable for networking work. They are likely to have a perfect knowledge of the networking functionalities and features in the CyberOps environment of the Associate level.
The Cisco 200-201 Exam Overview
In this section, you will come across what this exam covers and what to expect in an actual exam concerning a number of questions, time duration, exam cost, and exam topics.
Cisco 200-201 exam also known as Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS). You can schedule the exam through the Pearson VUE platform. Cisco 200-201 exam cost is $300. The exam is taken in the English language and consisting of 95-105 questions that need to be answered in 120 minutes.
Topics Covered in Cisco 200-201 Exam Is As Follow:
- Network Intrusion Analysis;
- Security Monitoring;
- Security Policies and Procedures;
- Security Concepts;
- Host-Based Analysis
Exam 200-201 is associated with the Cisco Certified CyberOps Associate certification, so its core purpose is to verify that the applicant has essential knowledge of cybersecurity operations and methods. You will notice that all exam questions are related to security, along with basic concepts, monitoring process, policies and procedures, and host-based and intrusion analysis.
Keeping this in mind, it is not surprising that most applicants do not know how to study for such a challenging exam appropriately. And if you are one of them, here are some tips you can follow.
Tips for Cisco 200-201 Exam
1. Assess Time and Work Needed Before Scheduling Exam
Everyone owns different training and experience, and so everyone learns differently. As per your familiarity with the exam topics and expertise, you should have time between your exam preparation and the scheduled date. You must understand the exam structure and topics to perceive how much you will require to study well.
Also Read: Help Your Career with Cisco CyberOps Associate 200-201 Exam
2. Make A Practical Timetable and Follow It
Without a proper study plan, it isn’t easy to pass any Cisco certification exam. So, make creating a timetable your priority, considering your work life. Devote at least one to two hours every day, rather than studying for eight to nine hours at one sitting. Studying every day will make you stay focused and dedicated. And assign more time to the topics you are weak in to improve your knowledge. In the case of studying for such a critical Cisco exam, consistency is necessary.
3. Take Cisco 200-201 Practice Test
One month before your scheduled exam, start taking practice test. Cisco 200-201 practice test to evaluate your learning and find out your knowledge gap. Practicing questions will acquaint you with the type of questions and exam environment. Exam anxiety will go away with consistent practice. Also, they gauge your conceptual knowledge of topics and develop an exam temperament.
Advantages of Passing Cisco CyberOps Associate 200-201 Exam
With the Cisco 200-201 exam, you will have the chance to learn the basic skills and get the appropriate knowledge of carrying out Cisco Cybersecurity Operations. Cisco CyberOps Associate certification will demonstrate that you can work with both an upgraded and new understanding of the expected fundamentals.
Passing the Cisco 200-201 exam is the only thing being in your way to establishing the career everyone wants. Here are some of the related job profiles, which you can get after passing your CBROPS exam:
- Network Analyst;
- Systems Administrator;
- Network Administrator.
And this is the most insignificant that you will be able to employ for and receive.
Conclusion
Cisco certification can help you develop and expand your skills and stay updated and more employable. Use Cisco 200-201 practice tests in your preparation journey. They can help you pass this certification exam so you can break into the excellent career opportunities that come with certification. So, don’t miss the opportunity and take it now!
Strategize Wi-Fi 6 upgrade with Cisco DNA Center
It is super exciting to see the rich set of features that Wi-Fi 6 has brought to the table. With the likes of high throughput, power optimization, and broadened security, Wi-Fi 6, as a technology that got enough to tempt the network upgrade. As a result, these promising capabilities could knock off an array of challenging access issues seen in the enterprise network.
In a typical enterprise setup, the network administrator is liable for leading the upgrade with no consequences. It warrants the admin to do due diligence in the planning phase to deal with the task smoothly.
Read More: 300-815: Implementing Cisco Advanced Call Control and Mobility Services (CLACCM)
Following are the top-of-the-mind questions of the administrator on the upgrade.
1. Which areas need immediate access point upgrade
2. What sort of Wi-Fi 6 Access points are the best fitting in the region
3. When and how to migrate without network interruption
What, do they sound like inhibitors? How relieving it may be if there is an efficient tool that provides sufficient insights and guidance for successful upgrades? Here it is. We have the Cisco DNA Center at our disposal to accomplish the purpose. Cisco DNA Center has a wide range of features that help right from planning to execution stage of the upgrade tasks.
Planning phase
During the planning phase, the administrator determines the various regions facing different access issues and prioritizes accordingly. Following are some of the typical access issues
◉ The chokepoints in the access network in the form of excess congestion
◉ Areas that operate high power starving IoT devices
◉ Places where mobile devices struggle uplink performance
◉ Areas having higher interference, and so on.
Cisco DNA Center Assurance has an exclusive dashboard to give insights into the Wi-Fi 6 readiness of the enterprise network and a set of AI/ML-driven dashboards to detect the regions where the Wi-Fi 6 upgrade makes a difference. With Wi-Fi 6 dashboard, the administrator will get the pattern of which level of Wi-Fi 6 enabled clients are noticed in the network and the regions where they are spotted regularly. This dashboard additionally gives insights into what infra level upgrade is needed to enable Wi-Fi 6 in the network.