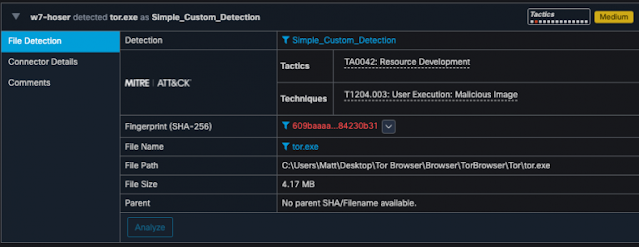
Like most companies, Cisco is committed to continually improving security while simultaneously simplifying the user experience.
We’ve learned some important lessons along the way.
There are multiple points where user ID and password credentials can be potentially compromised. For example, employees sometimes chose to ignore best practices by utilizing easy-to-remember passwords such as “123456.” Others would share their Cisco passwords or use them externally for non-business-related applications—essentially utilizing their passwords everywhere.
When we relied only on the password login process, it is estimated that about 80 percent of all hacks were caused by credentials/identity theft. Other points of concern included new-hire onboarding or credentials delivery, password resets on behalf of users, password-related communications, and overall handling or management of password details. All can contribute to potential risks.
Further complicating matters, when most of our workforce went remote in early 2020, it became confusing and taxing for users to know how to access different applications. For example, some apps required a Virtual Private Network (VPN) connection, while others could be accessed directly. Like many other companies, Cisco invested in VPN expansion to support employees working from home, while also rolling out Zero Trust on a limited basis initially (more details below).
As the lines increasingly blurred between work and home life, many remote workers became frustrated at connecting via VPN and enduring the authentication process potentially multiple times a day. It can be tiring for users to keep track of which applications need VPN and which don’t – reducing their productivity. Ultimately, using a VPN when the workforce is almost fully remote can be inefficient, especially when we’re sending data back over the corporate network, only to have it eventually return to the cloud.
Zero Trust framework delivers secure, uniform user experience
As a result, Cisco decided to move from a traditional, network-based perimeter and VPN model to a Zero Trust model. Zero trust is not a single solution but a framework of solutions that verify a device, establish policy, and continually monitor device behavior. Multi-Factor Authentication is a key element of this approach. We started deploying multi-factor authentication in November 2020 for several applications, then expanded its coverage in 2021 to many additional applications, including Microsoft Office 365.
Our overall goal for Zero Trust and multi-factor authentication is to provide a secure, uniform experience while accessing applications, wherever users or applications are located. From a technical perspective, we had four objectives:
1. Implement an architecture that would allow secure, VPN-free access to some of our most-visited internal and SaaS applications
2. Validate user and device trust on a per-app basis, with an ability to set per-app access policies
3. Improve our authentication experience by reducing the burden on users
4. Build this transition seamlessly, requiring zero user action, and without any outages or distractions
Zero Trust helps us achieve these goals by incorporating user/device trust policies for remotely accessing applications. Users enjoy a “borderless experience” by accessing the network from anywhere, without having to connect through a VPN.
Instead of relying only on user ID and password credentials, Zero Trust adds a layer of protection. It leverages a user-identity certificate that is securely deployed to managed endpoints by our device management suite. This certificate then acts as the first factor of authentication, saving users the step of having to type in their username and password. This also reduces the likelihood that users will save their corporate identity and password in their browser for convenience.
After establishing user trust, the solution validates device trust and health—starting with the assumption that if a device is managed by our corporate device management platforms, then it must have a good baseline security posture. We perform an additional device health check during every authentication transaction to ensure that the device is running the latest software, screen lock, disk encryption, firewall, and anti-virus agent. This real-time check is conducted by the Duo Beyond Device Health app, which continuously operates in the device’s background.
With Zero Trust, when a user tries to log in to an application, our corporate SSO identity engine checks the user and device certificate, does a real-time health assessment of the device, and finally triggers a second-factor notification before allowing user access.
Zero Trust saves time, boosts productivity
Since Zero Trust was implemented, adoption metrics show that it is saving Cisco employees more than 410,000 VPN authentications per month. Based on Cisco IT internal analyses, it takes about 45 seconds for each VPN authentication. This represents 307,500 minutes, or 5,125 hours, saved per month – an annual savings of 61,500 hours. Assuming an average hourly cost per employee of $55, we can value this productivity improvement at $3.4 million per year for Cisco employees. This also represents an optimization of the application information traffic flowing over the company’s core network and offloaded through direct internet access.
Since incorporating controls for device health and trust at the application layer, we’ve substantially improved our ability to react to device risk. For example, we’re conducting approximately 5.76 million device health checks automatically per month. This has allowed us to identify 86,000 devices per month that users have self-remediated. That’s 86,000 potential compromises effortlessly averted.
While there were some concerns about increased support call volume when introducing device health checks for borderless access, only 0.6 percent of users have contacted our help desk for support—which is actually less than the 7 percent rate of help-desk requests for security deployment, password reset, device remediation, and support calls for authentication based on internal benchmark. We feel that the easy-to-follow remediation steps within the Duo Device Health App played a key role in minimizing our support numbers. The deployment had a minimal impact, keeping overall costs low and providing a better user experience.
Subsequently, fewer analysts have been required to provide support, leading to an estimated $500,000 per year savings in helpdesk support costs. In addition to cutting support costs and improving security, the Zero Trust Multi-Factor Authentication framework has improved productivity because users don’t need to waste time logging in to the VPN.
Figure 1. Duo Zero Trust benefits
The future of Zero Trust
Implementing Zero Trust as a critical framework and adopting a more rigorous security posture will continue providing opportunities for Cisco. For example, the remote working capabilities that Zero Trust enables has over the past two years allowed Cisco to expand access to a diverse talent pool. According to Darcie Gainer, Cisco’s Security Product Marketing Leader, the remote working capabilities with borderless access and without VPN have already allowed Cisco to grow its intern classes in 2021 and 2022.
Source: cisco.com