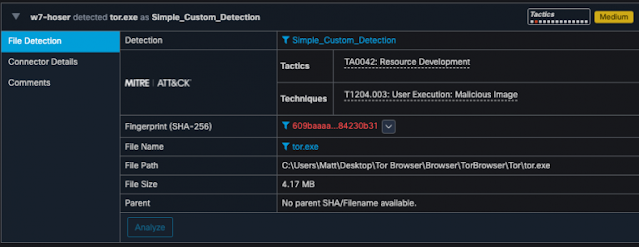
5G adoption is causing mobile networks to grow at unprecedented rates. This brings with it significant new business opportunities but can also increase the complexity and cost of deployment and operations. An intelligent, programmable network enables communication service providers to take advantage of the growth that 5G offers while streamlining their operations to maximize return on investment.
Cisco is addressing these challenges head-on with our industry-leading NCS 500 portfolio. New enhancements enable simultaneous support of both traditional architectures RAN and open, virtualized RAN, with full interoperability.
Challenges for Brownfield Operators
Using an open architecture provides many cost benefits to service providers, leveraging a Commercial Off-the-Shelf (COTS) based infrastructure, automation features, and an open ecosystem to promote a competitive market.
While it is relatively easy for greenfield service providers to adopt 5G open RAN interfaces and architectures, it is extremely difficult for brownfield operators who have already widely deployed 4G.
One of the main challenges for brownfield operators is the lack of interoperability available when using legacy RAN interfaces with an open RAN solution. Replacing all existing 4G CPRI radios in the network with eCPRI based radios is not feasible, which makes adoption of an open RAN and DU virtualization very difficult.
When 4G and 5G are being deployed in the same cell site but running on two different architectures (proprietary 4G eNB and virtualized open 5G DU), it is cost-prohibitive for the provider.
Brownfield Interoperability
Cisco has been working with various Standard Development Organizations (SDO) to define an open and fully interoperable 5G RAN architecture.
Through collaboration, we were able to create a solution that could seamlessly integrate legacy radios on Cisco’s Converged SDN Transport architecture, while also standardizing the specifications to make it fully interoperable.
As a contribution to the O-RAN ALLIANCE, we drove the creation of an open Fronthaul gateway specification (O-RAN.WG7.FHGW-HRD.0-v02.00) to address deployment challenges for brownfield providers. This specification allows legacy CPRI based radios to communicate with open RAN 7.2x eCPRI based DU.
Cisco NCS 540 Fronthaul Routers, a key element to the Converged SDN Transport architecture, provide an open and programmable solution to host RAN network functions like Fronthaul Gateway (FHGW) and RAN resource configuration.
O-RAN PlugFest in India
We were able to demonstrate this successful integration during the O-RAN Global PlugFest 2021 hosted by Bharti Airtel in India. Through our multivendor demo, Cisco NCS 540 platform hosted the FHGW network function provided by VVDN technologies and verified the solution using Keysight Open RAN Studio and Signal Analyzer.
Fig: O-RAN PlugFest demo setup at Bharti Airtel
Cisco’s solution approach is vendor agnostic, helping service providers to consolidate functions, optimize network inventory, and reduce the cost of deployment.
FHGW allows seamless integration of legacy radios to ORAN 7.2x DU enabling operators to adopt ORAN architecture for existing 4G networks. Although the FHGW is deployed at the cell site, it can provide approximately nine times the optimization to transport bandwidth in a centralized RAN architecture.
Open hardware and API definition helps overcome proprietary dependencies of RAN functions and allows seamless integration in a multi-vendor environment.
A programmable platform promotes innovation and protects investment. The same platform can be programmed to function as a Fronthaul MUX / De-MUX for shared cell deployment.
Joint European O-RAN and TIP PlugFest
Cisco also participated in the O-RAN European PlugFest 2021 hosted by TIM OTIC laboratory in Torino, Italy. We were challenged to build two end-to-end, interoperability solutions leveraging multi-vendor O-DU / O-CU radio software components and O-RU elements for both 4G (LTE B7) and 5G (n3, n78).
In both cases, the NCS 540 Series Router was used to provide packet-based fronthaul to connect O-RU to O-DU and to distribute timing and synchronization taken from the TIM network to O-RU using PTP and SyncE protocols according to the O-RAN LLS-C3 model.
We successfully demonstrated compliance to O-RAN transport characteristics in multivendor environments including time synchronization, packet fronthaul, latency and jitter, telemetry, and packet-based fronthaul network automation.
Powering Open, Virtualized RAN in Brownfield Deployments Today
As service providers continue to deploy 5G, the benefits of adopting a virtualized RAN are becoming increasingly evident. By providing secure and zero-touch infrastructure over a resilient transport architecture, we can simplify the deployment of virtualized DU servers at cell sites.
Virtualized infrastructure requires the following interfaces for management and zero-touch operations:
1. Out of Band (OOB) interface for server management and infrastructure onboarding
2. The management interface for server, radio, and virtual DU OAM
3. Management interfaces for Kubernetes or virtual machine infrastructure and container management.
Secure infrastructure using well-defined quality of service (QoS) is key to ensuring traffic protection and traceability in a multivendor environment. Cisco NCS 540 Series Routers are based on proven hardware and software, which is necessary to provide a secure environment for cell site virtualization.
A mature QoS architecture provides traffic separation and defined service protection. Secure and encrypted algorithms support SSH, AAA, DHCP, ZTP, SNMP, IPv4/IPv6, MACsec, IPsec, gRPC, MPP, and rich access control list features.
Cisco secure zero-touch provisioning enables a secure automation framework not only for the router but also for virtualized DU and open Radio deployment at the cell site.
Programmability and Automation
Cisco offers a flexible and programmable architecture that service providers can begin to take advantage of today. With rich streaming telemetry support, networks can be monitored with streamed configuration and operational telemetry data on a centralized data virtualization tool. The platform provides extensive support for YANG and IETF Models, and OpenConfig.
With open management interfaces and APIs, we can enable end-to-end network management functions through the operational lifecycle of the brownfield cell site. Cisco offers off-the-shelf and customized Cisco Network Services Orchestrator (NSO) function packs to automate the provisioning of each mobile network domain including radio, virtualized functions, and transport.
Committed to Continued Innovation
Cisco continues to focus on technological enhancements that will help brownfield service providers reduce deployment costs. By providing a transport infrastructure that is open, programmable, secure, and verified against standards, we are empowering providers to seamlessly adopt virtualization and open, disaggregated RAN solutions in multivendor environments.

Source: cisco.com