Wi-Fi 6E is here and the worldwide Wi-Fi community is buzzing about it. But why is it a major change? What does it mean for people’s Wi-Fi experience and infrastructure vendors like Cisco? And why are Cisco engineers excited about the opportunities for innovation? Read on to learn about the details of 6E and how this technology transition can enhance your career too.
Wi-Fi 6E is More Than Just “A Bit More Spectrum”
At its heart, Wi-Fi 6E extends Wi-Fi to the 6 GHz band of the wireless spectrum. This may not sound very impressive if you know that Wi-Fi currently uses many other bands. Regulatory bodies, like the FCC in the US and ETSI in the European community, allocate to each radio technology the right to transmit in segments of the spectrum and specify the allowed transmission characteristics, such as maximum power or the shape and size of the signal. For example:
◉ In the 2.4 GHz band, Wi-Fi is allowed over a bit more of the 80 MHz of spectrum, with typically up to 3 channels, each 20 MHz-wide.
◉ In the 5 GHz band, Wi-Fi is allowed over up to 500 MHz of spectrum, which enables 25 20-MHz-wide channels. These channels can be configured to be larger, 40 or 80 MHz, at the cost of a lower count of possible non-overlapping channels—12 and 6 for 40 and 80 MHz respectively.
Larger channels are often preferred because they enable the concurrent transmission of more data—much like a larger water pipe carries more water by unit of time—resulting in higher capacity and a better experience for bandwidth-intensive applications like video and AR/VR.
However, even with these options, two neighboring Wi-Fi access points (APs) should not be on overlapping channels because their signals will collide unless one AP waits for the other to finish transmitting before commencing its own transmission. This issue reduces the performance of the overall system. In dense environments—like university lecture halls or enterprise conference rooms—there is always a difficult negotiation to be made between the need for more APs to accommodate more people and their devices by allocating them across many networking pipes, and the need to maximize the size of each AP channel which, in turn, limits the number of APs that can be in the range of each other.
In the US FCC domain, Wi-Fi 6E adds 1200 MHz of new spectrum, creating 59 20-MHz-wide channels, more than tripling the number of channels available. This is great news for any Wi-Fi-dense deployment.
Even in domains where the new allocation is narrower—for example, in Europe with the ETSI domain currently planning to allocate 500 MHz—the number of channels available to Wi-Fi doubles. This means that any place that had 40 MHz channels will soon be able to switch to 80 MHz channels, doubling the capacity and enabling a 1080P video to be upscaled to 4K while maintaining the same experience.
New Band, New Rules
The 6 GHz band was of course not waiting for someone to need it. The 6 GHz space is in fact composed of 4 sub-bands, defined as U-NII 5 to U-NII 8 in the US. All of them are already actively in use by fixed, outdoor devices such as ground-to-space satellite services and point-to-point microwave links. U-NII6 and U-NII 8 are also used by mobile devices—think cable television field trucks sending video back to the main station. Wi-Fi will need to share these spectrum spaces and avoid disrupting the incumbents. For this reason, the rules for Wi-Fi devices depend on the sub-band where they operate.
Figure 1. 6 GHz allocation in the US (FCC domain)
In all 4 sub-bands, APs and clients can operate at a low power mode when located inside buildings. Lower power means shorter transmission distances and thus smaller Wi-Fi cells, but also higher chances that one AP or Wi-Fi client will not hear another unit well enough, causing packet losses or retries.
In two of the 4 sub-bands, APs and clients can operate at higher power—called Standard Power, with a max power comparable to Wi-Fi in part of the 5 GHz band—only if the APs first make sure that they are not disrupting an incumbent transmitter. This verification is not possible in UNII-6 and UNII-8 because, for example, it is difficult to predict where TV trucks will be at any one time, so only indoor and low power are allowed in those cases. But in UNII-5 and UNII-7 bands, for any outdoor operation and any operation at standard power, the AP must verify at boot time, and confirm every 24 hours, that it is not broadcasting on a frequency used by a fixed incumbent. The AP runs this verification by providing its geographical location to a central server—the Automated Frequency Coordinator, or AFC—that returns the 6GHz frequencies allowed in the immediate area. The maximum power allowed for Low Power Indoor (LPI) APs is half the max power of Automated Frequency Coordination (AFC) APs. And since client devices must operate at half the power of the APs, this power puzzle creates interesting Wi-Fi cell design challenges.
Power Spectral Density You Say?
The 6 GHz rules bring another interesting twist. In 5 GHz and 2.4 GHz, the transmission rules are driven by the notion of maximum Effective Isotropic Radiated Power (EIRP), which is the maximum quantity of energy emitted by a client or an AP. As the max EIRP is fixed, a system that transmits over a 20-MHz channel transmits more energy per unit of frequency (per MHz) than a system that radiates the same total amount of energy, but over a wider channel, for example, 80 MHz.
The idea is the same as a water hose. If your hose delivers 1 liter per second, it will spray less water per unit of surface if you spread the jet as a flat 3-meter-wide mist than if you focus the water, power washer style, over just a half square centimeter target. A direct, and sometimes hidden consequence of this rule is that if you set your AP channel to a width of 80 MHz (instead of 20 MHz), your cell size is mechanically reduced because the amount of signal available over each MHz of the channel at a given distance is now lower. A common way to express this reduction is to say that the signal-to-noise ratio (SNR), over each MHz of frequency, reduces as the channel width increases.
The Wi-Fi community expressed this concern when the 6 GHz allocation was being discussed by worldwide regulatory bodies. The great news is that the community was heard, and the rules are different for 6 GHz band. In this new band, the max power is no longer a ‘total max’ EIRP but is defined as max Power Spectral Density (PSD) or the max power per MHz—in the hose analogy, that’s the water delivered per unit of surface. This limit is per MHz and does not change as the channel width changes. In practice, this means that a 6 GHz system can send the same amount of energy per MHz in an 80 MHz channel as it would in a 20 MHz channel, and therefore that the cell size stays the same, regardless of the channel width. It just sends more total energy as the channel size increases.
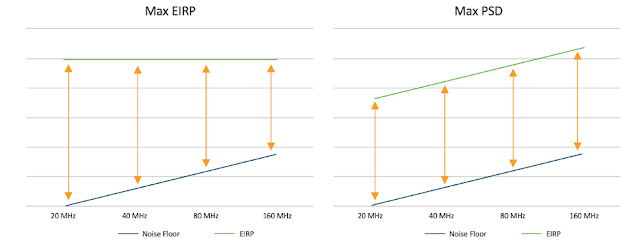
Figure 2. Power rule comparison between 5 GHz (left) and 6 GHz (right)
A New Golden Age for Wireless Engineering
Another exciting property of the new 6 GHz band is that…well, it is new. This may sound like a repeat, but what it really means is that the industry does not have to design compatibility rules for older devices.
In the 5 GHz band, for example, you may want the benefits of all the goodness of Wi-Fi 6, including efficient scheduling, extremely high throughput, and multi-user simultaneous transmissions, but your network may see older Wi-Fi 5 devices around or even older Wi-Fi 2 devices from the early 2000s. These were probably already obsolete 15 years ago, but the mere fact that they may be there forces all later versions of Wi-Fi, including Wi-Fi 6, to send frames that can be partially understood by older devices so they will detect transmissions and refrain from transmitting at the same time.
This problem does not exist in the new band, so it can be optimized for maximum performance. The clients still have to discover it, which again brings many interesting challenges. For example, scanning 25 channels in 5 GHz, then 59 more in 6 GHz, does not sound like a great idea for fast roaming between APs. So, the discovery mechanism has to have built-in intelligence. Similarly, you may want to keep 6 GHz for efficient traffic, such as your Augmented Reality applications, and send the less urgent traffic, like your background photo sync to the cloud, to the other bands. But this requires a clever exchange mechanism between the client and the AP on resources availability, traffic type, etc.
As you can see, there are a lot of opportunities to innovate and design wireless clients that can benefit from new 6E opportunities.
Join Cisco to Design the Future of Wi-Fi
At Cisco, we have been at the forefront of Wi-Fi innovation for more than two decades. Building the future of Wi-Fi starts by designing
great access points, and smart engines to optimize the experience that wireless clients can gain from optimized networks. Engineers working at Cisco take pride in designing the smartest AI-driven
Radio Resource Management engine on the market to dynamically assign channels and power levels to neighboring APs. This creates smooth continuous Wi-Fi coverage from small branch networks to large venues like Mobile World Congress, where 1500 APs and 75K+ simultaneous radio communication professionals expect nothing less than a perfect Wi-Fi experience. Other Cisco innovations include
OpenRoaming to automate onboarding, and
Fastlane+ to optimize the experience of your Apple iPhone and iPad in a Cisco Wi-Fi 6 network. The full list of Cisco wireless innovations would take a book to enumerate. And with a brand-new 6E band available on our
new access points, the opportunities to innovate are bounded only by your imagination and talent.
Source: cisco.com