How can you accurately track software licenses being consumed across your network and where? Smart licensing is the solution!
Smart licensing was created to simplify the customer experience and provide greater insight into software license ownership and consumption. It establishes a pool of licenses that can be used across your entire organization in an automated manner.
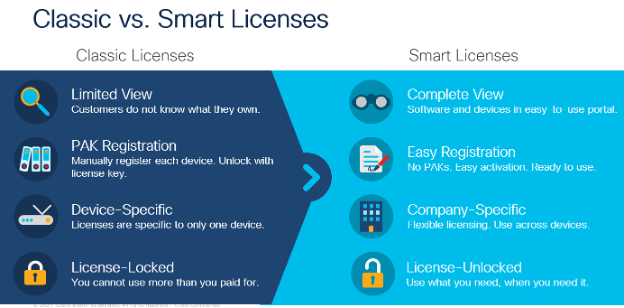
What is smart licensing?
Smart licensing is a flexible software licensing model that simplifies the way you activate and manage licenses across your organization. The smart licensing model makes it easier to procure, deploy, and manage your Cisco software licenses.
Smart licensing eliminates the need for PAK licenses and allows licenses to be easily shared across devices in the same organization. It also gives you the flexibility to use only what you need when you need it.
Why should I use smart licensing?
In today’s world, license portability and a flexible consumption model offer you the capability and flexibility to purchase software capacity as needed. This decreases OpEx and can eliminate stranded licenses. When installing high-density line cards or high-capacity fixed chassis, you don’t always need the full capacity of the hardware from day one and a simplified management tool allows you to fully utilize licenses and the dollars you spend.
| Customer Needs | IOS XR Flexible Consumption Model (FCM) |
| Customers want strategic partners who can provide commercial offers permitting them to pay incrementally to expand capacity as demand for their consumer and business services rises. | FCM is a pay-as-you-grow model which enables customers to invest in the network capacity as demand grows. Having this ability to add capacity as and when needed helps customers with their network and capacity planning. |
| Customers want investment protection with the portability of software across hardware resources to meet demand across any one of their markets. | FCM has a subscription component which includes software portability. This provides investment protection by enabling porting of licenses to next-generation hardware when a customer is ready. |
| Customers want a software license management experience that enables porting of licenses across the corporation to shift capacity to markets in demand. | FCM permits service providers to pool software licenses and lower initial investments required to incubate new services. |
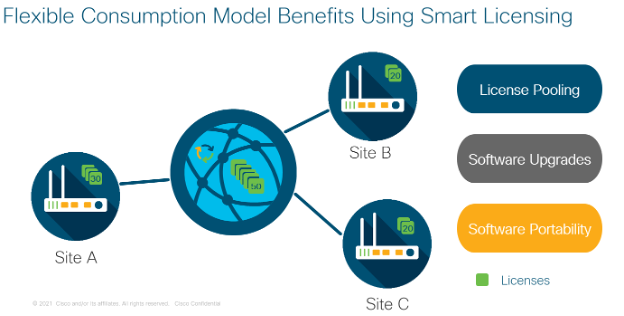
Flexible consumption model benefits using smart licensing
◉ Simplify operations. Two software suites, Essentials Software and Advantage Software, simplify license management while still providing the carrier-class Cisco IOS XR Software feature set.
◉ License pooling: You can efficiently share licenses network-wide with license pooling. This solution improves capacity planning by eliminating “stranded capacity” as you can use available capacity wherever needed in the IOS XR Flexible Consumption Model network. In this manner, you can potentially utilize your capital budgets to consume software innovations in IOS XR.
◉ Software upgrades: Software upgrades provide access to new features and enhancements to existing features.
◉ Software portability: Software portability provides investment protection by enabling porting of licenses to next-generation hardware when you’re ready. During decommissioning of hardware and transitioning to next generation hardware, you retain the ability to not decommission the investment in the software, and instead, port it to a newer hardware provided all necessary conditions are met.
Flexible consumption model and smart licensing are supported on the following products:
◉ Access – NCS 540, NCS 560
◉ Edge – ASR 9000
◉ Core – NCS 5500, NCS 5700, and 8000 Series routers
The flexible consumption model requires Cisco Smart Licensing registration and license usage reporting. A network under IOS XR FCM is considered compliant if the FCM-enabled devices in your network are registered to smart licensing and are reporting the usage. Starting from IOS XR 7.3.1, major and minor XR software upgrades will only be available once you’ve registered the devices and aren’t using more licenses than what was purchased. The registration process is a simple one-time event that can be automated using Cisco EZ-Register, an open-source solution.
Source: cisco.com