As part of the Industry 4.0 Initiative, many enterprises are working to improve their efficiency by increasingly digitalizing and connecting their business processes. This evolution calls for the aggressive adoption of networked sensors, robots, autonomous guided vehicles (AGVs), or other IoT devices. 5G, the latest generation of cellular technology, promises to meet the requirements that arise in such enterprise environments requiring extremely low latency and high reliability. But so far cellular networks have predominantly been operated by communication service providers (CSPs). So how can 5G be introduced into an enterprise setting with minimal risk and disruption to existing business processes?
Many enterprises are embarking on an Industry 4.0 journey, aiming to increase business efficiencies and workflow uptime and make informed business decisions. In this journey, existing processes are automated by deploying intelligent robots, AGVs, sensors, or other instruments that are networked together and supported by controllers providing real-time automation, visibility, and control. Examples of such processes in a manufacturing context include:
◉ Flexibly connecting manufacturing assets
◉ Deploying layout-free production lines, including autonomous robots and co-bots
◉ AGVs
◉ UHD cameras on high-speed uplinks combined with machine learning algorithms for predictive quality control and maintenance
◉ Augmented reality training
While this trend in Industry 4.0 promises to increase competitiveness and quality and reduce production costs, the required changes still present major challenges to predominantly risk-averse enterprises. Adjustments to existing processes are often quite intrusive, requiring deployment of new digitalized endpoints. Enterprise networks also need to support connectivity requirements beyond the carpeted space to include outdoor environments and allow partners and customers to participate in a fully digitalized workflow.
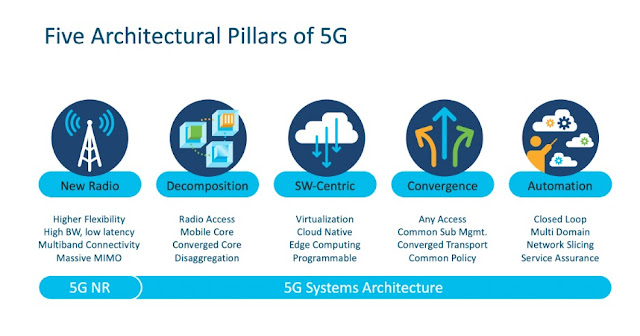
5G is emerging as a promising way to address these challenges. The latest generation of 3GPP cellular technology standards take an open architectural approach in addition to offering improvements in radio connectivity between endpoints and base stations. 5G offers deterministic real-time access to the network, broad geographic coverage, low latency, and high bandwidth communication to IoT devices. The figure below illustrates the five architectural pillars of 5G.
Cellular technologies have their roots in consumer mobile networks, using regulator-controlled licensed frequencies. Their sophisticated functional components support global roaming, high-speed handoffs between antennas, and detailed billing to name a few. To an enterprise operator, 5G as a technology may seem complex and unfamiliar. A major reason is that operators must consider several system design options in 5G, such as:
◉ Which radio spectrum to use, licensed, unlicensed, or shared (e.g., CBRS) — low-band (<1-GHz), mid-band (“sub-6-GHz”), high-band/mmWave (>24-GHz)?
◉ How to align the level of availability/reliability to the application/service level agreement (SLA)?
◉ How to cover the required area, be it campus (indoor/outdoor), branch offices, distributed remote sites, or industrial?
◉ Where to place the various 5G network functions for radios and the 5G packet core – is the network disaggregation centralized, private/on-prem, or hybrid?
◉ How to ensure security since disaggregation, open APIs, and 5G’s polyglot architecture represent new attack surfaces?
◉ How to meet data sovereignty and regulatory requirements?
◉ How to design for access determinism and what level of determinism is sufficient to meet application requirements?
◉ Ownership vs. partnership models, SLA impact on security, and resiliency models
◉ How to meet the requirements from different endpoint/user-equipment device-types such as phones, modems, sensors, worker wearables, drones, AGV/vehicle controllers, tools, fleet-management routers, industrial routers, etc.?
The introduction of 5G into the enterprise network may seem daunting to an enterprise operator, so it’s natural to look at the community of solution and managed service providers (MSPs) for help!
Three ways service providers can make the most of private 5G
From the perspective of a CSP or MSP, the above challenges that enterprises face in their journey to digitalization present opportunities to extend or enhance their managed service portfolio. Such providers typically have an opportunity to:
1. Offer a generalized 5G service that covers a broad market segment
2. Offer a vertical-specific, turnkey 5G service (e.g., for healthcare or manufacturing)
3. Offer a flexible 5G service integrated into an existing enterprise environment
An example of No. 1 is a CSP that offers 5G service throughout its entire service domain. Such operators could build the service based on their public network by devoting network functions to any subscribing enterprise. This approach is called network slicing in a 5G architecture, and it has the advantage of leveraging the existing technologies (5G packet core, radios) deployed for consumer services in a more service-differentiated manner. The service provider deploys multiple virtual networks on common network infrastructure end to end with control elements that are specific to the business purpose of each service slice.
An example of No. 2 would be an architecture where a systems integrator or MSP creates a turnkey service offer for a particular industry vertical. Dedicated 5G packet core and radios are integrated with vertical-specific endpoints (e.g., robots, AGVs) and deployed on enterprise premises. The systems integrator is typically responsible for the deployment and operation of the entire solution. The 5G network is dedicated to the enterprise’s solution use case and can thus offer the required SLAs. A drawback of such a turnkey solution can be the lack of integration with an existing enterprise network.
Option No. 3 offers a hybrid of the other two alternatives. In this model, the MSP offers a generic 5G access network dedicated to the enterprise without sharing critical resources with other enterprises. Such a network can be generic to multiple use cases, increasing the MSP’s target market. The service can also be tightly integrated into existing enterprise networks, for example by providing links into existing enterprise policy servers or by re-using the installed transport network to connect radios. This possibility of a tight integration with enterprise network operations makes this mode of consuming a 5G managed service particularly attractive.
Why choose an “as-a-service” model?
Each of the above three models have their place in the market and offer advantages. For all three, the “as-a-service” model offers a compelling alternative to a do-it-yourself approach.
We’re active in the public 5G core and transport domains and as such empower any service provider wishing to offer services as in option No. 1. The transport architecture of sliced services will be enabled by new IP routing technologies such as segment routing to address key slice characteristics like bandwidth and path forwarding policy. Core domain network slicing can also be enabled by 5G core orchestrators to govern containerized cloud-native 5G core network functions.
However, most enterprises embarking on the Industry 4.0 journey are looking for dedicated functions as outlined under the latter two options. The ability to retain control over access policies for 5G endpoints or to influence security and quality-of-service policies makes option No. 3 particularly attractive for risk-averse enterprises.
Cisco’s private 5G solution is based on a compelling variation of such an as-a-service approach. It offers critical functions of a 5G access network dedicated to the enterprise and positioned on-premises, but some control functions are also cloud delivered in a software-as-a-service model to the MSP. This allows the MSP to reduce time to market by avoiding deployment and operations complexities of the 5G packet core functions. MSPs can also enjoy the cloud management capabilities that have already been established with the Cisco IoT Control Center platform. We’re already hosting more than 200 million cellular devices on this cloud platform, making it a prime candidate to also extend the approach to the private 5G solution architecture.
Source: cisco.com