Saturday, 1 April 2023
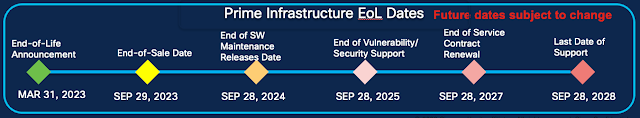
Good Friends Say Goodbye as Prime Infrastructure Sunsets
Thursday, 30 March 2023
Failing Forward – What We Learned at Cisco from a “Failed” Digital Orchestration Pilot
Our Digital Orchestration Goals
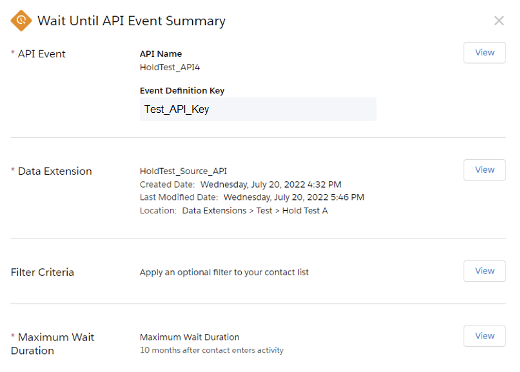
Use Case #1: Seamlessly connect prescriptive actions across channels to our sellers, partners, and customers.
Use Case #2: Pause and resume a digital email journey based on triggers from other channels.
Use Case #3: Connect analytics across the multichannel customer journey.
Use Case #4: Easily integrate data science to branch and personalize the customer journey.
Finding Success
Tuesday, 28 March 2023
Cisco Modeling Labs 2.5: Now with Resource Limiting
What is resource limiting in CML 2.5?
How to configure CML resource limits
Create and assign resource pools
Create and define your template(s)
Limit access to external connectors
How to check resource usage
Highlights and benefits of CML 2.5 resource limits
Monday, 27 March 2023
Everything You Need to Know About Cisco 300-215: The Exam and Certification Guide
Are you planning to take the Cisco 300-215 exam to enhance your career prospects as a security engineer? If yes, then this article is for you. This article will cover all the essential information you need to know about the Cisco 300-215 exam, including the exam syllabus, preparation tips, and the certification process.
Know About Cisco 300-215 CBRFIR Exam
Cisco 300-215 CBRFIR exam, also known as Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps, is designed to test the knowledge and skills of security engineers in conducting forensic analysis and incident response using Cisco technologies. The exam duration is 90 minutes and consists of 55-65 questions.
300-215 CBRFIR Exam Syllabus
The Cisco 300-215 CBRFIR exam syllabus is divided into six domains, each covering different topics related to forensic analysis and incident response. The domains are:
Fundamentals- 20%
Forensics Technique- 20%
Incident Response Techniques- 30%
Forensics Processes- 15%
Incident Response Processes- 15%
Target Audience
The target audience for the Cisco 300-215 certification exam is security engineers who want to specialize in conducting forensic analysis and incident response using Cisco technologies. This certification is ideal for professionals protecting and securing organizational assets, including networks, endpoints, and data.
The certification is also suitable for professionals who want to enhance their knowledge and skills in forensic analysis and incident response, regardless of their current job title or industry. It can benefit professionals in various fields, including:
- Cybersecurity: Cybersecurity professionals who want to specialize in conducting forensic analysis and incident response using Cisco technologies can benefit from earning the Cisco 300-215 certification. It demonstrates their expertise and enhances their credibility in the field.
- IT Operations: IT operations professionals responsible for managing and securing IT infrastructure can benefit from earning the Cisco 300-215 certification. It gives them the necessary knowledge and skills to effectively detect and respond to security incidents.
- Law Enforcement: Law enforcement professionals who are involved in investigating cybercrime can benefit from earning the Cisco 300-215 certification. It gives them the necessary knowledge and skills to conduct forensic analysis and incident response using Cisco technologies.
- Compliance: Compliance professionals are responsible for ensuring that organizations that comply with regulatory requirements can benefit from earning the Cisco 300-215 certification. It provides them with the necessary knowledge and skills to conduct forensic analysis and incident response to meet regulatory requirements.
300-215 Certification Process
Top 5 Cisco 300-215 CBRFIR Preparation Tips
1. Study the Exam Syllabus:
The exam syllabus is your roadmap to success. Make sure to study each domain thoroughly and understand the topics covered.
2. Use Study Materials:
Cisco provides official study materials, including books, videos, and practice tests, to help you prepare for the exam. You can also use third-party study materials from reputable sources.
3. Practice, Practice, Practice:
Practice is essential to passing the exam. Use practice tests to assess your knowledge and identify areas of improvement.
4. Join Study Groups:
Studying groups can help you learn from other candidates and share your knowledge and experiences.
5. Latest 300-215 Questions:
300-215 exam questions are confidential and not publicly available. Candidates should study the exam objectives and topics thoroughly and keep up with the latest trends and technologies in forensic analysis and incident response to prepare effectively for the exam.
Cisco 300-215 CBRFIR Benefits
- Career Advancement: Cisco 300-215 certification is recognized by industry leaders and can help you advance your career in cybersecurity and related fields. It demonstrates your knowledge and skills in conducting forensic analysis and incident response using Cisco technologies, making you a valuable asset to any organization.
- Competitive Edge: The cybersecurity industry is highly competitive, and earning Cisco 300-215 certification can give you a competitive edge over other candidates. It shows you have the necessary knowledge and skills to perform the job at a high level.
- Enhanced Skills and Knowledge: Preparing for the Cisco 300-215 exam requires a comprehensive study plan and a structured approach. Studying for the exam will enhance your skills and knowledge in conducting forensic analysis and incident response using Cisco technologies.
- Increased Earning Potential: According to PayScale, the average salary for a security engineer with Cisco Certified CyberOps Professional certification is around $106k annually. Earning this certification can increase your earning potential and lead to higher-paying job opportunities.
- Professional Development: Cisco 300-215 certification is valuable to your professional portfolio and can help you stand out in the job market. It demonstrates your commitment to professional development and lifelong learning.
Cisco 300-215 Scope
The Cisco 300-215 CBRFIR exam covers various topics related to conducting forensic analysis and incident response using Cisco technologies. The exam syllabus is divided into six domains, each covering different areas of expertise. Here is an overview of the scope of the Cisco 300-215 exam:
- Fundamentals of Forensic Analysis and Incident Response: This domain covers the basic concepts and principles of forensic analysis and incident response. It includes forensic investigation, evidence collection, and legal considerations.
- Network Forensics and Traffic Analysis: This domain covers network-based forensic analysis and incident response. It includes network traffic analysis, protocol analysis, and intrusion detection and prevention.
- Endpoint Forensics and Analysis: This domain covers endpoint-based forensic analysis and incident response. It includes malware analysis, memory forensics, and disk forensics.
- Incident Response: This domain covers incident response procedures and methodologies. It includes incident detection and analysis, classification and prioritization, and incident response planning.
- Incident Handling: This domain covers the practical aspects of incident handling. It includes containment, eradication, recovery, and communication and coordination with stakeholders.
- Incident Response Teams: This domain covers the organization and management of incident response teams. It includes team roles and responsibilities, incident response plan development and maintenance, and incident response team training and exercises.
The Cisco 300-215 exam covers various topics related to forensic analysis and incident response using Cisco technologies. The domains cover the field's theoretical and practical aspects, making it a comprehensive certification for security engineers.
Conclusion
The Cisco 300-215 CBRFIR exam is an essential certification for security engineers who want to specialize in conducting forensic analysis and incident response using Cisco technologies. Following the tips and guidelines in this article, you can prepare for the exam and pass it with flying colors.
Good luck!
Saturday, 25 March 2023
Designing and Deploying Cisco AI Spoofing Detection – Part 2
AI Spoofing Detection Architecture and Deployment
Our previous blog post, Designing and Deploying Cisco AI Spoofing Detection, Part 1: From Device to Behavioral Model, introduced a hybrid cloud/on-premises service that detects spoofing attacks using behavioral traffic models of endpoints. In that post, we discussed the motivation and the need for this service and the scope of its operation. We then provided an overview of our Machine Learning development and maintenance process. This post will detail the global architecture of Cisco AISD, the mode of operation, and how IT incorporates the results into its security workflow.
Since Cisco AISD is a security product, minimizing detection delay is of significant importance. With that in mind, several infrastructure choices were designed into the service. Most Cisco AI Analytics services use Spark as a processing engine. However, in Cisco AISD, we use an AWS Lambda function instead of Spark because the warmup time of a Lambda function is typically shorter, enabling a quicker generation of results and, therefore a shorter detection delay. While this design choice reduces the computational capacity of the process, that has not been a problem thanks to a custom-made caching strategy that reduces processing to only new data on each Lambda execution.
Global AI Spoofing Detection Architecture Overview
Cisco AISD is deployed on a Cisco DNA Center network controller using a hybrid architecture of an on-premises controller tethered to a cloud service. The service consists of on-premises processes as well as cloud-based components.
The on-premises components on the Cisco DNA Center controller perform several vital functions. On the outbound data path, the service continually receives and processes raw data captured from network devices, anonymizes customer PII, and exports it to cloud processes over a secure channel. On the inbound data path, it receives any new endpoint spoofing alerts generated by the Machine Learning algorithms in the cloud, deanonymizes any relevant customer PII, and triggers any Changes of Authorization (CoA) via Cisco Identity Services Engine (ISE) on affected endpoints.
The cloud components perform several key functions focused primarily on processing the high volume data flowing from all on-premises deployments and running Machine Learning inference. In particular, the evaluation and detection mechanism has three steps:
1. Apache Airflow is the underlying orchestrator and scheduler to initiate compute functions. An Airflow DAG frequently enqueues computation requests for each active customer to a queuing service.
2. As each computation request is dequeued, a corresponding serverless compute function is invoked. Using serverless functions enables us to control compute costs at scale. This is a highly efficient multi-step, compute-intensive, short-running function that performs an ETL step by reading raw anonymized customer data from data buckets and transforming them into a set of input feature vectors to be used for inference by our Machine Learning models for spoof detection. This compute function leverages some of cloud providers’ common Function as a Service architecture.
3. This function then also performs the model inference step on the feature vectors produced in the previous step, ultimately leading to the detection of spoofing attempts if they are present. If a spoof attempt is detected, the details of the finding are pushed to a database that is queried by the on-premises components of Cisco DNA Center and finally presented to administrators for action.
Cisco AI Spoofing Detection in Action
Protecting the Network from Spoofing Attacks with Cisco DNA Center
Tuesday, 21 March 2023
Designing and Deploying Cisco AI Spoofing Detection – Part 1
The network faces new security threats every day. Adversaries are constantly evolving and using increasingly novel mechanisms to breach corporate networks and hold intellectual property hostage. Breaches and security incidents that make the headlines are usually preceded by considerable recceing by the perpetrators. During this phase, typically one or several compromised endpoints in the network are used to observe traffic patterns, discover services, determine connectivity, and gather information for further exploit.
Compromised endpoints are legitimately part of the network but are typically devices that do not have a healthy cycle of security patches, such as IoT controllers, printers, or custom-built hardware running custom firmware or an off-the-shelf operating system that has been stripped down to run on minimal hardware resources. From a security perspective, the challenge is to detect when a compromise of these devices has taken place, even if no malicious activity is in progress.
In the first part of this two-part blog series, we discuss some of the methods by which compromised endpoints can get access to restricted segments of the network and how Cisco AI Spoofing Detection is designed used to detect such endpoints by modeling and monitoring their behavior.
Part 1: From Device to Behavioral Model
One of the ways modern network access control systems allow endpoints into the network is by analyzing identity signatures generated by the endpoints. Unfortunately, a well-crafted identity signature generated from a compromised endpoint can effectively spoof the endpoint to elevate its privileges, allowing it access to previously unauthorized segments of the network and sensitive resources. This behavior can easily slip detection as it’s within the normal operating parameters of Network Access Control (NAC) systems and endpoint behavior. Generally, these identity signatures are captured through declarative probes that contain endpoint-specific parameters (e.g., OUI, CDP, HTTP, User-Agent). A combination of these probes is then used to associate an identity with endpoints.
Any probe that can be controlled (i.e., declared) by an endpoint is subject to being spoofed. Since, in some environments, the endpoint type is used to assign access rights and privileges, this type of spoofing attempt can lead to critical security risks. For example, if a compromised endpoint can be made to look like a printer by crafting the probes it generates, then it can get access to the printer network/VLAN with access to print servers that in turn could open the network to the endpoint via lateral movements.
There are three common ways in which an endpoint on the network can get privileged access to restricted segments of network:
1. MAC spoofing: an attacker impersonates a specific endpoint to obtain the same privileges.
2. Probe spoofing: an attacker forges specific packets to impersonate a given endpoint type.
3. Malware: a legitimate endpoint is infected with a virus, trojan, or other types of malware that allows an attacker to leverage the permissions of the endpoint to access restricted systems.
Cisco AI Spoofing Detection (AISD) focuses primarily on the detection of endpoints employing probe spoofing, most instances of MAC spoofing, and some cases of Malware infection. Contrary to the traditional rule-based systems for spoofing detection, Cisco AISD relies on behavioral models to detect endpoints that do not behave as the type of device they claim to be. These behavioral models are built and trained on anonymized data from hundreds of thousands of endpoints deployed in multiple customer networks. This Machine Learning-based, data-driven approach enables Cisco AISD to build models that capture the full gamut of behavior of many device types in various environments.