If the network is the skeleton, then applications are the lifeblood of today’s business. They connect organizations with their customers, employees, supply chains, partners, and even generate revenue. Safeguarding modern applications running across complex hybrid multicloud environments is paramount for every size and type of business. Cisco Secure Workload 3.8 brings a wealth of new capabilities to help security professionals protect critical application workloads by simplifying complexity and unifying network controls to improve their overall security posture.
Secure Workload protects the applications that power business in an infrastructure, location, and form factor agnostic manner. It does this by employing an agent and agentless approaches to give customers deep visibility into every workload interaction and uses powerful AI/ML-driven automation to handle tasks that are beyond human scale, delivering accurate and consistent microsegmentation and continuously monitoring compliance across the application landscape.
Secure Workload 3.8 improves productivity, lowers the overall TCO for existing and new customers by delivering a minimum of 50% greater scale on the existing platforms. It also provides consistent agent and agentless microsegmentation for workload deployment across hybrid multicloud, expanding the core microsegmentation use cases. And last but certainly not least it strengthens the integration with Cisco Secure Firewall and Cisco Identity Services Engine (ISE).
The latest version of Secure Workload continues to focus on enhancing the user experience with more automation, simplifying the onboarding process, and adding new platform APIs. The end-to-end workflow helps customers achieve zero trust faster, improve operator productivity by 50% or more, and significantly reduce the time to value.
In the digital economy, speed and information are the key currencies. The persona-based reporting dashboard introduced in the 3.8 release delivers actionable intelligence on demand, reports the overall security health of applications, illustrates emerging trends based on historical data, and introduces new Forensics alerts based on the MITRE ATT&CK framework.
Figure – 1 Alerts based on MITRE ATT&CK Framework
Secure Workload 3.8 supports greater scale on the existing platform and connectors which helps customers extend their hardware life and lowers the solution’s total cost of ownership. The updated scale numbers are shown below:
And in our continued effort to deliver a true multicloud zero trust solution with agent and agentless flexibility for our customers, the Google Cloud Platform (GCP) connector in the 3.8 release delivers agentless microsegmentation for applications deployed in Google Cloud, adding to our existing support for AWS and Azure cloud.
Since the early days of its inception, Secure Workload has integrated with Identity Services Engine (ISE) to address user/device identity-based segmentation scenarios in the customer environment. In the 3.8 release, Secure Workload integrates with the ISE Passive ID which helps ingest user, group, and other attributes from the customer Active Directory and/or Azure Directory and in turn enables endpoint identity-aware visibility and policy enforcement.
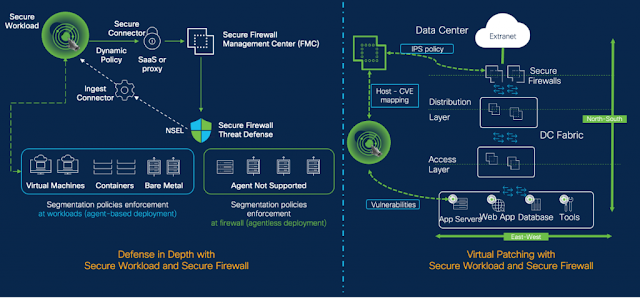
Two years ago, we launched the native integration between Secure Workload and Secure Firewall to provide defense in depth and an agentless approach for on-prem environments to achieve zero trust. With the 3.8 release, we are taking this integration to the next level with topology awareness, giving customers the granular control to discover, enforce, and automate select policies on a specific firewall or set of firewalls through Secure Workload.
Figure 2 – Defense in Depth and Virtual Patching – Secure Workload and Secure Firewall Integration
As you may know, it is not uncommon to have critical vulnerabilities unpatched in an environment despite best-of-breed vulnerability management solutions. While there are many factors, with virtual patching Secure Workload and Secure Firewall seamlessly share threat intelligence and ensure that the right SNORT signature is applied to protect against a known vulnerability present in the customer environment without breaking the application.
Source: cisco.com