I recently attended a session run by the Said Business School at Oxford along with an organisation called Istari. The discussion was based upon their research into at the view CEOs had of cyber resilience.
There were two immediate points which struck me. The first is that major cyber incidents are hugely traumatic for CEOs. It is an experience they are ill equipped to deal with when compared to other business challenges. This is not surprising considering the speed at which an incident can stop a business from operating and its relative recent appearance when compared to other risks. The second was that cyber security is not a topic to interest a CEO but cyber resilience certainly is. So, a lesson for security professionals is to “watch your language” and use more recognised terminology.
So, what practical steps can a CEO take to address Cyber Resilience rather than just heaving it on to the shoulders of the CISO.
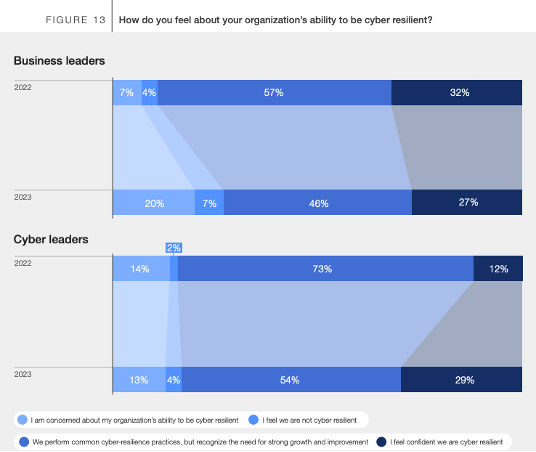
One of the issues could be a possible difference between views on Cyber Resilience between Business Leaders and CISOs. A recent report by the World Economic Forum showed a comparative difference between these two groups in their organisations cyber resilience capability. Whereas CISOs saw a definite improvement Business Leaders were not so sure.
One action could be is to define and agree what resilience means to the organisation. It can be very different according to the nature, risk and priorities of the organisation. In a key, regulated member of the CNI there will be a different idea of resilience when compared to a born in the cloud start up chasing market share. The former will be focused on ensuring stability and compliance, the latter on availability and speed of change. So different views of what it means to keep the business operating, adapting and innovating.
The CEO should be agreeing on a Risk based approach and clearly expressing the importance of this is at the start. One principle I was told to follow many years ago as a young consultant is that CEOs always make decision with a Risk vs Opportunity mind set. If we do this, what will we gain, what could we lose and how do we minimise the downside? So, security teams can always present an issue on those terms. What the priorities are, how should they be addressed and the identifiable benefits.
From the CISO perspective this can be a great help in practical terms. For example, during a discussion with a couple of CISOs, it became apparent that they had different levels of budgetary support from their CEO. One had aligned all expenditure with the Risk Register and was well funded. The other had a funding surge after an incident but interest had waned and now funding was harder to justify. The former had the support of the CEO for the security function whilst the latter was seen in the light of a specific incident which became less valid as memories faded.
This observation led me to another topic. A lot is talked about Culture, the soft art of improving security and resilience. This is increasingly referred to by CISOs but shouldn’t the CEO be leading this change? To draw a comparison. Over the years the concept of Health and Safety has increased in profile as CEOs committed to the principles especially in industries such as Oil and Gas. This developed into a clear set of ordered priorities, employees, customers, shareholders. Now the principles of Sustainability are also becoming fundamental to how an organisation operates. Cyber Resilience can likewise be developed into the fabric and values. Become part of the culture.
The best place to start is at the most senior level. Some years go the World Economic Forum produced a set of Board Principles to support CEOs and which are valid today. They encompass the basic needs which a Board to address from Accountability to Collaboration. Adopting an internationally recognised framework has been successful in the past and I am aware of a CISO who used these Principles to gain greater traction internally. Driven by the CEO this will create a sense of Cyber Resilience as part of the fundamental management of the business.
All preparation is improved by constant repetition and developing the ability to act when needed. Tabletop exercises are commonly carried out. But for the CEO to lead on these and ensure full cooperation is a further way to change the culture and thinking. Being trained in a situation will intuitively increase awareness of the importance of cyber resilience as well as building in response capabilities. Learning in the middle of an incident is not the best option.
When addressing culture at a more tactical, day to day, basis the CEO should ensure that the ELT have Security Champions working in all areas of the business. People who understand how colleagues work to and align security with them. Understanding the User Experience. The benefit of this will be to feed back to the security teams the needs of the business from a resilience perspective. Whether following set procedures is more important than being able to adapt quickly and securely for example. In addition, it makes security a cooperative rather than an antagonistic exercise where the security team impose controls.
As a final thought. The CEO could support the CISO in getting the right communications around the risk and benefits to the business by not holding the CISO responsible for communicating the ideas and principles. In other words, make it the responsibility for the business leaders to communicate what resilience means to them and their areas of responsibility.
One CISO was supported by the adoption of this approach and got the support from within the organisation they secured. The brand was of paramount importance to the business. Built up over years. A major corporate asset. The CISO asked the marketing team to define the impact and cost, tangible and intangible, of an incident on the brand and how resilience could be worked into the brand values as a positive element for customers. Whilst it may be a long trek for the CISO to achieve this support, for the CEO it could be a simple first step to inculcate cyber resilience into the culture and thinking of the organisation by asking the functional leads to take the initiative.
For the CEO an incident could be traumatic. But there are a range of proactive steps that could be taken at the most senior level through to daily operations.
There is an adage that the most expensive security is the security that is applied after the event. If the CEO leads Cyber Resilience journey, not only will security make the organisation more resilience, it could also save money. It will weigh the Risk vs Opportunity decision in favour of the opportunity by understanding and mitigating the risk. And by being part of the solution the CEO will find the traumatic impact of an incident is reduced.
Source: cisco.com