The iDMZ (industrial demilitarized zone) is a critical layer in a comprehensive end-to-end security strategy for an industrial operations environment. The primary function of the iDMZ is the enforcement of a secure boundary between the internal trusted operations environment and external entities that may need to exchange data with services that support the operation.
One of the challenges with an exclusively on-site iDMZ is the limited ability around expansion to meet future demand and capabilities. With the growth of Industrial IoT (IIoT), it will be necessary for hardware and resource growth to meet the demands of increasing data. This translates to a consistently increasing hardware footprint and utilities to provide cooling and power, which can be in limited supply on premises. In addition, operators must explore new ways to obtain deeper insights and introduce enhancements to the operation, which may require tighter alignment with partners and/or the ability to securely consume XaaS offers.
Operators also have a safety-first culture, keeping people out of the “line of fire.” Vendors and partners may need to maintain on-site hardware, applications and services, potentially exposing people to risk through their presence on-site. For heavy industry environments, accessibility to site and the equipment residing on it is not necessarily an easily accomplished task. Many industrial sites require site safety training and approved work permits as a prerequisite for physical access.
Finally, a lack of iDMZ consistency when comparing multiple sites, from a hardware and feature composition, creates challenges for operations staff. In some instances, product and feature selection is made locally. This impacts the ability to deliver consistent policies and end user experiences. It also complicates support across the operation for staff responsible for troubleshooting and minimizing time to resolution and maintaining different SOPs and training documents.
Operators exploring options to gain operational efficiencies through modern service offerings may benefit from exploring how to extend their iDMZ beyond the “four walls” of the operation.
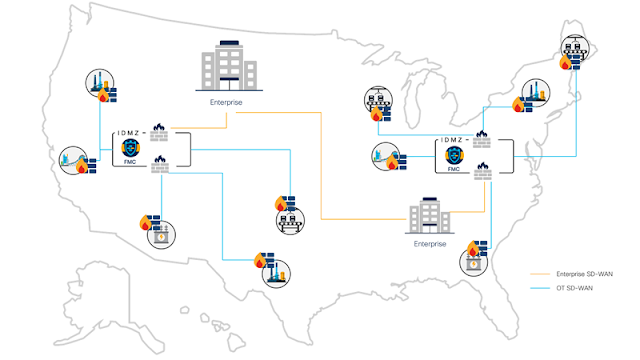
One deployment alternative for iDMZ is extending the architecture to leverage a hybrid-cloud model. A hybrid cloud iDMZ model can be deployed as a centralized model or repeated regionally, based on geographic presence and/or regulatory or compliance requirements. While migrating the entirety of the iDMZ and its capabilities to the cloud may not be an option, a hybrid cloud iDMZ architecture does offer operational benefits and mitigates previously raised challenges.
First, the hybrid cloud iDMZ can secure the operation, and mitigate risk and exposure. Similar to an on-prem iDMZ, multiple tools and applications should be leveraged to take a holistic approach for enforcing security. This can include:
◉ Services that support a secure and encrypted pipe between an operations site and a regional iDMZ
◉ Segmentation and possible options for multi-tenancy
◉ Visibility to monitor applications and flows traversing the industrial zone
The solution should also include tools for consistently configuring, deploying, enforcing policies, and managing assets.
In addition to providing a holistic security strategy, a hybrid cloud iDMZ offers the benefit of shared resources and assets, as opposed to entirely duplicating unique stand-alone iDMZ deployments per site. The regional based approach offers a more repeatable and consistent architecture, delivering consistent policies, as well as easing the operational overhead and complexity mentioned previously.
A hybrid cloud solution offers more flexibility to expand, and contract based on evolving requirements and demand. By leveraging public cloud services as part of the iDMZ architecture, operators have the ability to increase capabilities without physically maintaining hardware and space to house equipment. This approach affords the unique opportunity to foster tighter engagements with partners and ecosystem vendors, while leveraging cloud services to drive innovation, deeper operational insights and efficiencies. Adding tools like Thousand Eyes and App Dynamics, operators can verify adherence to application SLAs/SLOs, in accordance with operational requirements.
Finally, a hybrid cloud iDMZ aligns with the concept of the ROC (Regional Operations Center), which is top of mind for some industrial organizations, especially those with a global footprint. A ROC model seeks to leverage more automation and remote operations, thus reducing on-site headcount to mission essential resources, improving on-site safety and driving more operational efficiencies. With a regional based iDMZ deployment, the process of aggregating and presenting the status and data for operations within the region can become more streamlined and a regionally distributed model can facilitate compliance with local industry regulations, if applicable.
For more details on how to build a hybrid cloud iDMZ architecture and its benefits for securing industrial operations, we have just published a short white paper that you should read on the Hybrid Cloud Industrial DMZ. We’ll also be discussing this in a free webinar on September 20, 2022.
Source: cisco.com





0 comments:
Post a Comment