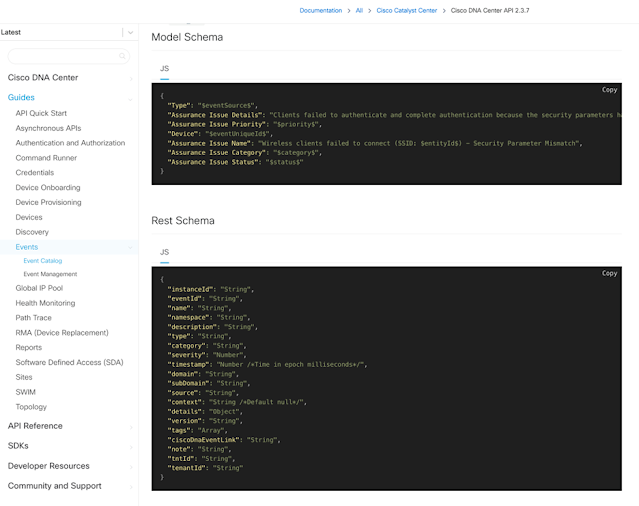
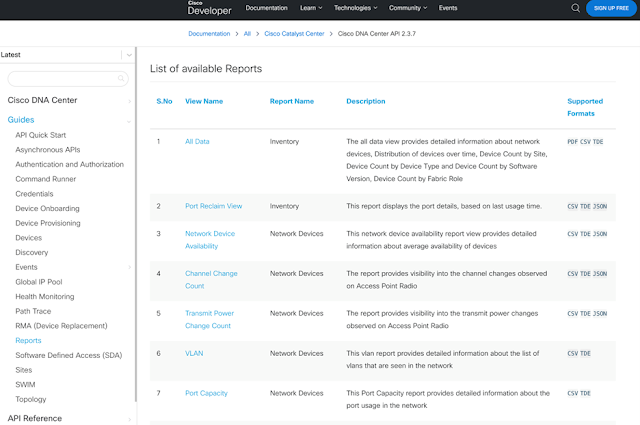
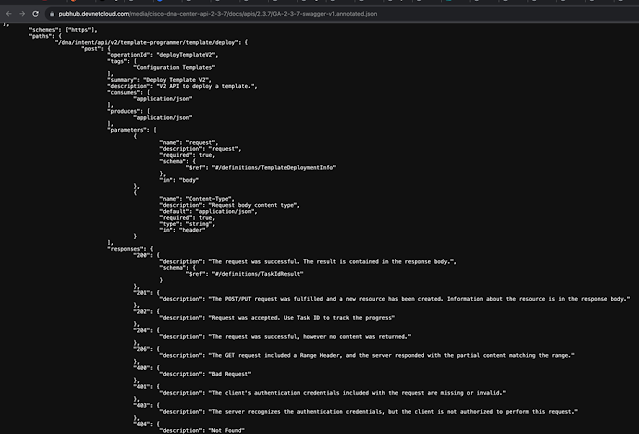
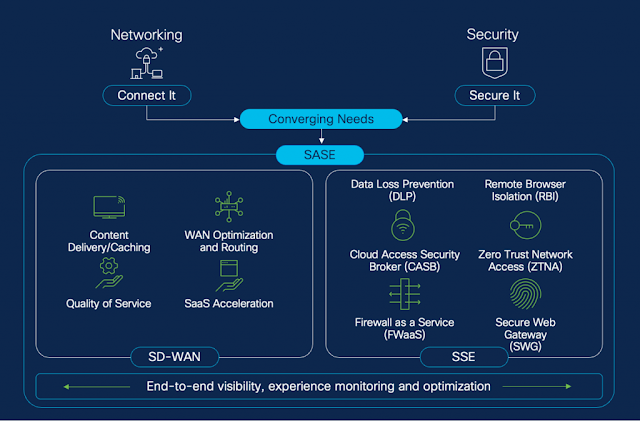
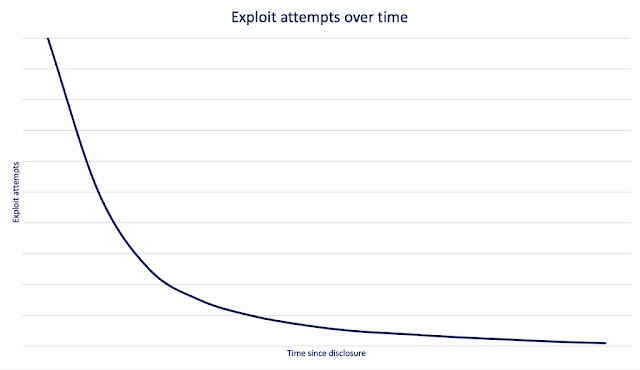
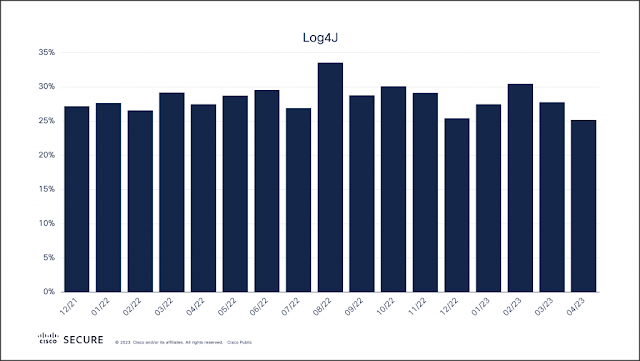
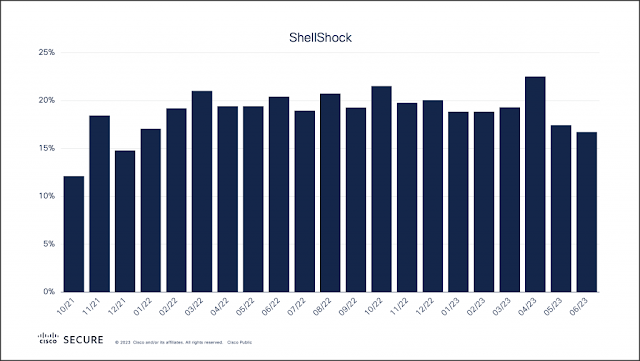
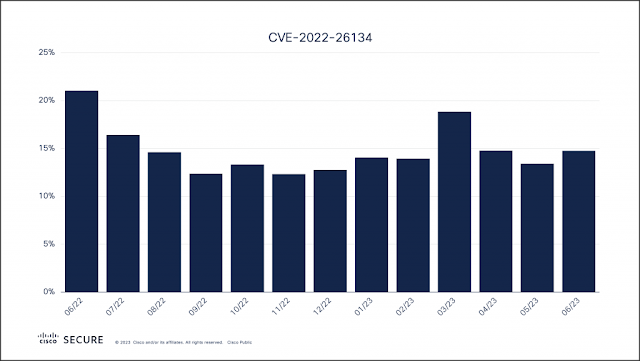
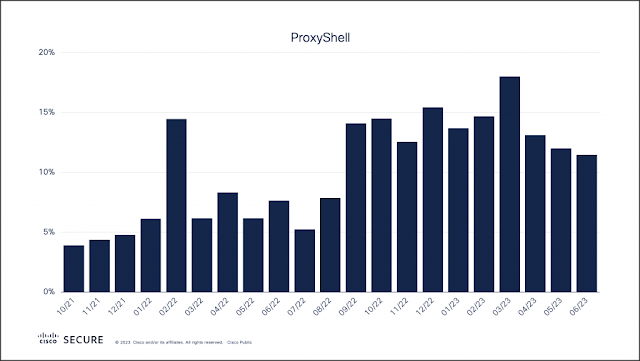
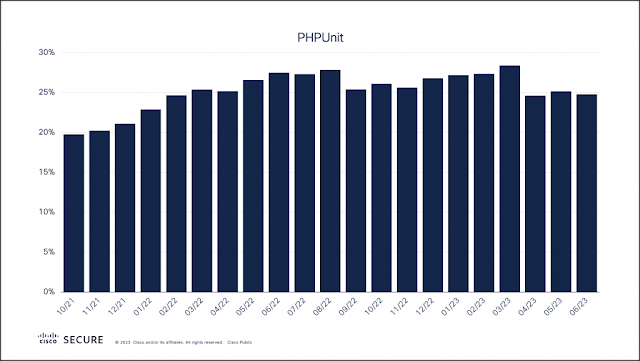
Cisco DNA Center is not only getting a name change to Cisco Catalyst Center, it also offers lots of new features, and add-ons in the API documentation. Let me tell about some of them.Version selection menuThe first improvement I want to mention is the API documentation version selection...