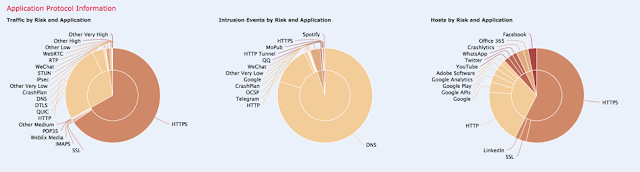
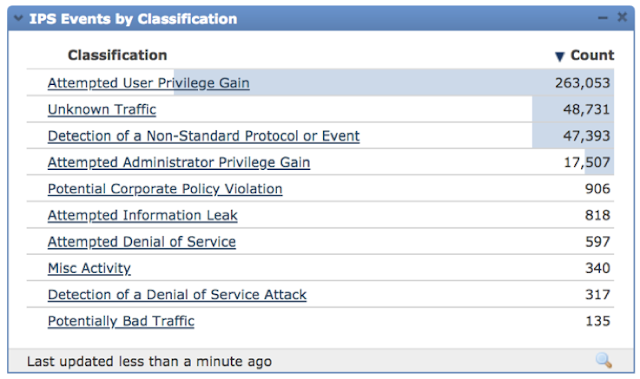
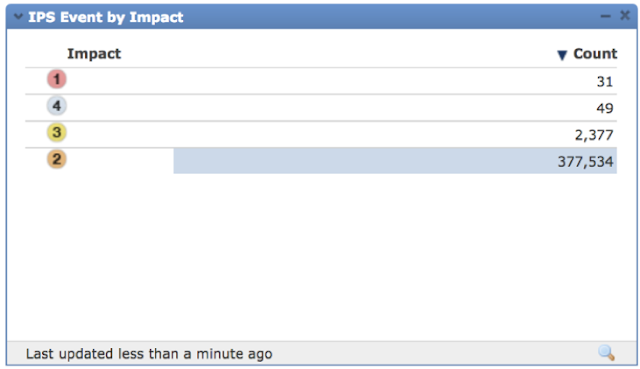
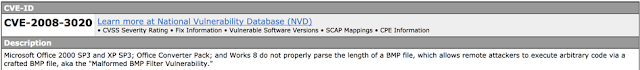
I still remember the day I first got ADSL at home in 2000. The top speed was only 2 Mbps, but I was purely fascinated by everything I could do at home, especially playing video games. Not before long, ADSL was replaced with VDSL, which changed my use of the internet from playing games to downloading video and music files in bulk, thanks to Napster and Torrent.
Putting memories aside, the general landscape of the internet has completely changed over the last decade. No longer are the days of one desktop serving an entire family, instead each family member has at least one smartphone and possibly a laptop which are used constantly for streaming videos, music and more. Businesses have an immense scale of data to process and share over the internet. What this means is that bandwidth is the key to keeping families happy and businesses running.
DSL innovation has been relentless when it comes to meeting the growing demand for higher bandwidth in the market. The latest form of DSL that has been introduced is G.fast, which is expanding aggressively in the UK and Switzerland. G.fast is a DSL technology that has stretched its frequency spectrum up to 106 MHz with the additional capability to increase up to 212 MHz. Compared to the common VDSL2 deployment with 17 MHz, G.fast at 106MHz is capable of offering throughput up to 1 Gbps. In addition to its high bandwidth, G.fast is a more affordable option compared to fiber, since it is deployed over copper wires.
Today’s internet landscape has also played a major role in propelling local governments and service providers to work hand-in-hand to provide faster internet services to the general public. For example, the EU has launched an initiative to support access to internet connections with 1 Gbps by 2025 for all schools, transport hubs and main providers of public services, as well as digitally intensive enterprises. In order to support this initiative, it is no surprise that G.fast is highly favored by many service providers in Europe. British Telecom and Swisscom are at the forefront in leading their services with G.fast.
G.fast is a DSL technology, but it sets itself apart in a few aspects from its predecessors, such as VDSL. First, the frequency spectrum used in G.fast is far wider compared to most profiles in VDSL2. The latest VDSL2 profile, deployed in Italy and Germany, is only at 35MHz, offering a throughput of 300 Mbps. Early G.fast deployments used a frequency spectrum of 22-106MHz to avoid interference from the range used by VDSL, which resulted in approximately 100 Mbps less throughput compared to using the full spectrum from 2 MHz. To increase the throughput on G.fast, the current frequency spectrum is being evaluated for an extension down to 2 MHz and up to 212 MHz. Particularly, 212MHz promises a peak aggregate throughput of 2 Gbps, which will enable 1Gbps for both downstream and upstream.
Another technical difference that makes G.fast unique is Time Domain Duplex (TDD). ADSL and VDSL have traditionally used Frequency Domain Duplex (FDD), where downstream and upstream had one frequency band for each to communicate. Since the frequency band for each direction of traffic was fixed, it was difficult to dynamically adjust the throughput per direction depending on need.
TDD enables both downstream and upstream to use the same frequency band, which allows G.fast to make throughput adjustments flexibly for both directions. The benefit of using TDD for G.fast is huge for service providers who have more flexibility to design different classes of service offerings on the same link.
DSL, by design, is vulnerable to attenuation occurring on copper wires, which means that throughput varies depending on the distance from the CPE to DSLAM. G.fast is no exception to attenuation. Though it is able to reach 1Gbps in theory, in a very short loop length, it is impossible to maintain such short loop length in an actual deployment. Different studies would show different throughput results over distance, but the throughput range between the distance of 200 to 400 meters falls between 500 Mbps to 200 Mbps. For this reason, current G.fast deployments in the UK and Switzerland are designed for the distance between 200 – 300 meters with a target throughput between 200 Mbps to 500 Mbps. With the introduction of 212 MHz in the future, the serviceable areas with G.fast will be extended with higher levels of throughput.
Cisco never shied away from accommodating new changes in the market and meeting the most challenging demands from the customers. Cisco’s flagship product family, the Integrated Services Router Series, has evolved ever since its inception to stay competitive and relevant in the market by adding new routers with the latest innovations.
Cisco introduced the ISR 1000 Series routers in late 2017. It was the latest addition to the Integrated Services Routers family. The routers perform at an unmatched level to meet today’s growing demand for high throughput while offering a diverse set of WAN connectivity options including LTE Advanced, VDSL, Ethernet and Fiber.
In July 2018, G.fast was added to the list of supported WAN options on the 8 LAN port ISR 1000 Series routers with the creation of new models: C1112 and C1113. G.fast on the C1112 and C1113 will be supported over both POTS and ISDN to serve a wider list of countries. In addition to G.fast, both models will support ADSL and VDSL, including Profile 35b, to provide customers with flexible DSL deployment options. As early as November 2018, C1112 and C1113 will also be integrated with Cisco SD-WAN.
C1112 and C1113 are the only enterprise-grade routers in the market to provide secure and reliable connection with the ability to provide the high bandwidth required by today’s G.fast deployments. Both routers will not only enable customers to expand their service offerings with G.fast, but help them to protect their investment in the existing infrastructure.
Putting memories aside, the general landscape of the internet has completely changed over the last decade. No longer are the days of one desktop serving an entire family, instead each family member has at least one smartphone and possibly a laptop which are used constantly for streaming videos, music and more. Businesses have an immense scale of data to process and share over the internet. What this means is that bandwidth is the key to keeping families happy and businesses running.
DSL innovation has been relentless when it comes to meeting the growing demand for higher bandwidth in the market. The latest form of DSL that has been introduced is G.fast, which is expanding aggressively in the UK and Switzerland. G.fast is a DSL technology that has stretched its frequency spectrum up to 106 MHz with the additional capability to increase up to 212 MHz. Compared to the common VDSL2 deployment with 17 MHz, G.fast at 106MHz is capable of offering throughput up to 1 Gbps. In addition to its high bandwidth, G.fast is a more affordable option compared to fiber, since it is deployed over copper wires.
Today’s internet landscape has also played a major role in propelling local governments and service providers to work hand-in-hand to provide faster internet services to the general public. For example, the EU has launched an initiative to support access to internet connections with 1 Gbps by 2025 for all schools, transport hubs and main providers of public services, as well as digitally intensive enterprises. In order to support this initiative, it is no surprise that G.fast is highly favored by many service providers in Europe. British Telecom and Swisscom are at the forefront in leading their services with G.fast.
G.fast in Detail
G.fast is a DSL technology, but it sets itself apart in a few aspects from its predecessors, such as VDSL. First, the frequency spectrum used in G.fast is far wider compared to most profiles in VDSL2. The latest VDSL2 profile, deployed in Italy and Germany, is only at 35MHz, offering a throughput of 300 Mbps. Early G.fast deployments used a frequency spectrum of 22-106MHz to avoid interference from the range used by VDSL, which resulted in approximately 100 Mbps less throughput compared to using the full spectrum from 2 MHz. To increase the throughput on G.fast, the current frequency spectrum is being evaluated for an extension down to 2 MHz and up to 212 MHz. Particularly, 212MHz promises a peak aggregate throughput of 2 Gbps, which will enable 1Gbps for both downstream and upstream.
Another technical difference that makes G.fast unique is Time Domain Duplex (TDD). ADSL and VDSL have traditionally used Frequency Domain Duplex (FDD), where downstream and upstream had one frequency band for each to communicate. Since the frequency band for each direction of traffic was fixed, it was difficult to dynamically adjust the throughput per direction depending on need.
TDD enables both downstream and upstream to use the same frequency band, which allows G.fast to make throughput adjustments flexibly for both directions. The benefit of using TDD for G.fast is huge for service providers who have more flexibility to design different classes of service offerings on the same link.
G.fast Deployment
DSL, by design, is vulnerable to attenuation occurring on copper wires, which means that throughput varies depending on the distance from the CPE to DSLAM. G.fast is no exception to attenuation. Though it is able to reach 1Gbps in theory, in a very short loop length, it is impossible to maintain such short loop length in an actual deployment. Different studies would show different throughput results over distance, but the throughput range between the distance of 200 to 400 meters falls between 500 Mbps to 200 Mbps. For this reason, current G.fast deployments in the UK and Switzerland are designed for the distance between 200 – 300 meters with a target throughput between 200 Mbps to 500 Mbps. With the introduction of 212 MHz in the future, the serviceable areas with G.fast will be extended with higher levels of throughput.
Cisco’s Solution
Cisco never shied away from accommodating new changes in the market and meeting the most challenging demands from the customers. Cisco’s flagship product family, the Integrated Services Router Series, has evolved ever since its inception to stay competitive and relevant in the market by adding new routers with the latest innovations.
Cisco introduced the ISR 1000 Series routers in late 2017. It was the latest addition to the Integrated Services Routers family. The routers perform at an unmatched level to meet today’s growing demand for high throughput while offering a diverse set of WAN connectivity options including LTE Advanced, VDSL, Ethernet and Fiber.
In July 2018, G.fast was added to the list of supported WAN options on the 8 LAN port ISR 1000 Series routers with the creation of new models: C1112 and C1113. G.fast on the C1112 and C1113 will be supported over both POTS and ISDN to serve a wider list of countries. In addition to G.fast, both models will support ADSL and VDSL, including Profile 35b, to provide customers with flexible DSL deployment options. As early as November 2018, C1112 and C1113 will also be integrated with Cisco SD-WAN.