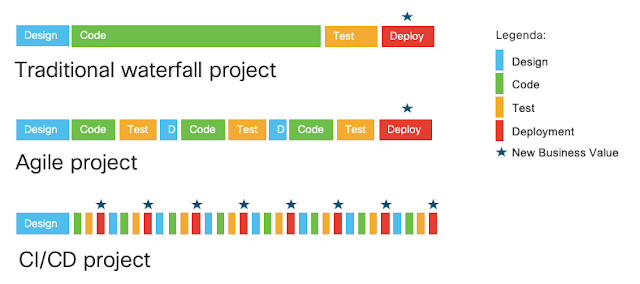
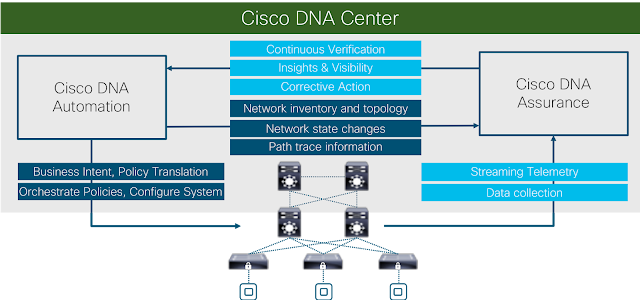
The most expensive cyber security event ever, started with a software accounting package from the Ukraine. In its wake 25% of the world’s shipping was shut down, major automobile and pharmaceutical companies came to a stop. And now a major lawsuit between an insurance provider and its customer has come forward with the phrase “act of war” as a major point of contention.
What factory manager saw that coming?
Chances are nobody did, and that’s why Cisco, Schneider Electric, and Aveva are working together to mitigate the risks of digital manufacturing so their connected industrial customers can seize IIoT’s many rewards.
“What previously was protected by proprietary OT protocols and hard-wired connectivity across the factory floor is now open game to hackers trying to do their dirty work through targeted IoT endpoints — whether a smartphone, field engineer’s tablet, connected variable speed drive, or any IoT-enabled asset.”
So what to do? Where to start.
Let’s start with an attitude adjustment. While most ICS environments have an implicit trust model, we need to surround them with a resilient architecture built on a zero-trust approach. In short: allow only the absolutely necessary access to equipment and applications. It is a significant change and will require significant buy-in from all involved.
How to get there.
Segmentation gives you the opportunity to stop those outbreaks while controlling access, whether it be a whole department or an individual switch port connected to a robot.
Start high – where the attacks first enter the factory – through the industrial DMZ. It is shocking how many modern Fortune 500 factories lack a properly managed firewall separating it from the enterprise network. Much of the impact of WannaCry /NotPetya could have been addressed with a properly configured firewall. The world’s most widely deployed next-generation firewall, FirePower, can help.
Next, work your way down through the Purdue model: Levels 3 down to individual machines, increasing granular control (micro-segmentation) along the way. You will need to understand the production lines, their relationships, and componentry. To do that you have to have visibility.
Visibility into your factory and processes is requisite for your segmentation decisions. You MUST find the process communication trails and work with the automation engineers to determine what is critical to ongoing operations. Cisco Stealthwatch can trace the full range of manufacturing communication patterns, from the factory floor, across the IDMZ to corporate ERP systems, to your favorite robot vendor’s cloud based analytics platform.
With an understanding of system communications, now build out a network architecture with modern network equipment. Look to resilient design concepts with multiple possible paths. Build for the future with Software Defined Networking for Software Defined Access (SDA). Cisco drives these policies through ISE (Identity Services Engine) which takes device or user identities directly or through pxGrid integrations with other Cisco products like IND (Industrial Network Director) or third party tools like Nozomi and others.
Visibility also drives understanding of process challenges including security threats.
Your DMZ NGFW should be able to determine if telemetry feeds are to be queried or simply pushed to analysis tools in the cloud or back at the research lab. Coupling your historians connection history at the plant with what is seen at the enterprise and beyond to the cloud based analysis site can cross numerous organizational and network boundaries through the stitching capabilities of Stealthwatch and Stealthwatch Cloud.
Visibility includes understanding the end-points in the factory. Are your engineering workstations or historians running without endpoint protections, making them potentially vulnerable to malware? ISE can tell you if end point protections are there, and of course you can remediate that threat with the deployment of AMP (Advanced Malware Protection). And the plant floor itself? With the knowledge that your metal press has a vulnerable HMI (as determined by IND and ISE) and that the next maintenance outage is seven months away (as determined by the production calendar), you can quickly apply a Talos-produced SNORT rule to protect that machine via an ISA 3000 industrial NGFW at its gateway edge.
Just as a control loop takes inputs and adjusts the process, so, too, should your security see the state of your process system’s security and actuate the proper controls. Proper security controls are dynamic and adaptable. A microsegmentation capable architecture and network is the base from which you enable visibility into new equipment and behaviors. Visibility provides the knowledge (with help from the operations team) to drive the policies which the network and security controls will enforce. And this process is as connected as your modern factory because we can stitch together the factory activity with the enterprise – crossing former boundaries to create stronger and more secure bonds.
All this represents a dramatic shift for manufacturers, OT professionals, and even IT departments.
At Cisco, we’re proud to stand at the forefront of the effort, alongside our partners at Schneider Electric and Aveva, to secure digital manufacturing and prevent negative outcomes.
Chances are nobody did, and that’s why Cisco, Schneider Electric, and Aveva are working together to mitigate the risks of digital manufacturing so their connected industrial customers can seize IIoT’s many rewards.
Designing IT/OT networks with cybersecurity in mind
“What previously was protected by proprietary OT protocols and hard-wired connectivity across the factory floor is now open game to hackers trying to do their dirty work through targeted IoT endpoints — whether a smartphone, field engineer’s tablet, connected variable speed drive, or any IoT-enabled asset.”
So what to do? Where to start.
Let’s start with an attitude adjustment. While most ICS environments have an implicit trust model, we need to surround them with a resilient architecture built on a zero-trust approach. In short: allow only the absolutely necessary access to equipment and applications. It is a significant change and will require significant buy-in from all involved.
How to get there.
Segmentation – contain outbreaks and control access
Segmentation gives you the opportunity to stop those outbreaks while controlling access, whether it be a whole department or an individual switch port connected to a robot.
Start high – where the attacks first enter the factory – through the industrial DMZ. It is shocking how many modern Fortune 500 factories lack a properly managed firewall separating it from the enterprise network. Much of the impact of WannaCry /NotPetya could have been addressed with a properly configured firewall. The world’s most widely deployed next-generation firewall, FirePower, can help.
Next, work your way down through the Purdue model: Levels 3 down to individual machines, increasing granular control (micro-segmentation) along the way. You will need to understand the production lines, their relationships, and componentry. To do that you have to have visibility.
Visibility builds better segmentation
Visibility into your factory and processes is requisite for your segmentation decisions. You MUST find the process communication trails and work with the automation engineers to determine what is critical to ongoing operations. Cisco Stealthwatch can trace the full range of manufacturing communication patterns, from the factory floor, across the IDMZ to corporate ERP systems, to your favorite robot vendor’s cloud based analytics platform.
With an understanding of system communications, now build out a network architecture with modern network equipment. Look to resilient design concepts with multiple possible paths. Build for the future with Software Defined Networking for Software Defined Access (SDA). Cisco drives these policies through ISE (Identity Services Engine) which takes device or user identities directly or through pxGrid integrations with other Cisco products like IND (Industrial Network Director) or third party tools like Nozomi and others.
Visibility for the big picture
Visibility also drives understanding of process challenges including security threats.
Your DMZ NGFW should be able to determine if telemetry feeds are to be queried or simply pushed to analysis tools in the cloud or back at the research lab. Coupling your historians connection history at the plant with what is seen at the enterprise and beyond to the cloud based analysis site can cross numerous organizational and network boundaries through the stitching capabilities of Stealthwatch and Stealthwatch Cloud.
Visibility includes understanding the end-points in the factory. Are your engineering workstations or historians running without endpoint protections, making them potentially vulnerable to malware? ISE can tell you if end point protections are there, and of course you can remediate that threat with the deployment of AMP (Advanced Malware Protection). And the plant floor itself? With the knowledge that your metal press has a vulnerable HMI (as determined by IND and ISE) and that the next maintenance outage is seven months away (as determined by the production calendar), you can quickly apply a Talos-produced SNORT rule to protect that machine via an ISA 3000 industrial NGFW at its gateway edge.
Close the loop with a security control loop
Just as a control loop takes inputs and adjusts the process, so, too, should your security see the state of your process system’s security and actuate the proper controls. Proper security controls are dynamic and adaptable. A microsegmentation capable architecture and network is the base from which you enable visibility into new equipment and behaviors. Visibility provides the knowledge (with help from the operations team) to drive the policies which the network and security controls will enforce. And this process is as connected as your modern factory because we can stitch together the factory activity with the enterprise – crossing former boundaries to create stronger and more secure bonds.
Now’s the time to secure your factory floor
All this represents a dramatic shift for manufacturers, OT professionals, and even IT departments.
At Cisco, we’re proud to stand at the forefront of the effort, alongside our partners at Schneider Electric and Aveva, to secure digital manufacturing and prevent negative outcomes.