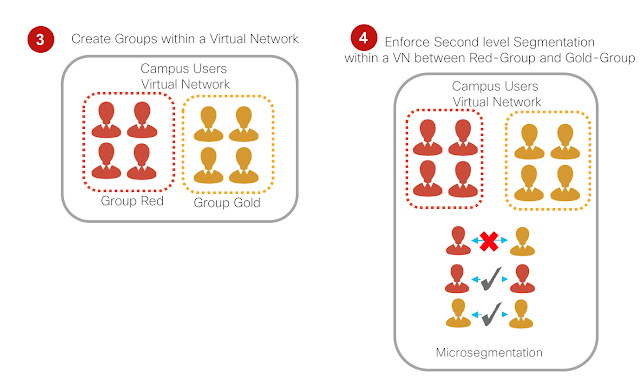
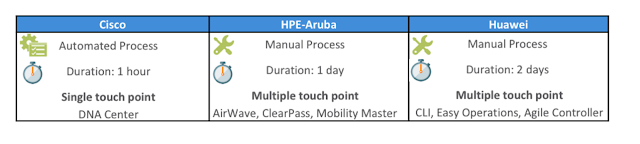
A short time ago I had the opportunity to participate in the AI Partner and Customer events that we had in our Innovation Centers in Paris, London and Berlin. The excitement and interest of both our customers and partners was palpable.
You might have seen some of the headlines in the news around Artificial Intelligence (AI) and Machine Learning (ML) and how in the US, the European Union and Asia many countries are increasing their public and private investment in this field. AI is present everywhere nowadays, from a simple semantic search on the internet to some of the latest self-driving vehicles already available in many places. It is expected that by the year 2022 worldwide spending in AI systems will reach 78 billion US dollars and that the spending in AI servers will grow from 5 billion to 18 billion US dollars. These figures alone represent a substantial opportunity for Cisco and for our Partners.
Another interesting learning from these events was that contrary to what most people might think, a larger percentage of Machine Learning deployments are deployed on-premise as opposed to on cloud. This poses an immediate opportunity for Cisco and our partners in terms of supporting our customers with their initial deployments in their own Data Centers. There are some intrinsic benefits for deploying ML on premise, among them we can list the data gravity integration and application performance, governance and TCO (Total Cost of Ownership), while on cloud deployments provide faster deployments and simplicity.
An AI/ML solution requires multidisciplinary skills and a deep collaboration between different stakeholders, including Data Scientists and Data Engineers, the CIO and the different business leaders as well as the IT team. Without all these different teams working together with a common and joint objective a successful deployment would be really difficult to realize.
The Cisco AI/ML offering focuses on Full Data Life Cycle, Simplicity, and Manageability and includes:
◈ A full portfolio for all AI/ML computing needs.
◈ Validated solutions with technology partners
◈ Natural extension of existing computing environment
The Cisco AI/ML Architecture includes UCS (Unified Computing Systems) Servers, Cisco Infrastructure Management and Cisco Networking Solutions that power a Virtualization Layer, a Converged Infrastructure for AI and Big Data Clusters which in turn sustain the AI/ML Software platforms which eventually provide the business outcomes that AI delivers. This Architecture helps to bridge the gap between IT and the Data Scientists.
There are some real use cases examples that were highlighted in these AI events which I found quite relevant and that our partners can leverage to initiate the discussion with their customers. Some of them include:
Banking
◈ Customer-Centric Marketing
◈ Product recommendation
◈ Experience personalization
◈ Attrition prediction
Operations
◈ Improve customer experience
◈ Predicting Failures
◈ Automatically Position Spares at Depots
◈ Optimizing Supply Chain and Customer Experience
Auto
◈ Autonomous Vehicle Simulations
◈ Complex simulation modelling
◈ Massive storage requirements
◈ High volume data inputs
AI/ML can also help resolve some of the Internet of Things new set of technical challenges such as:
◈ Harsh environments
◈ Hyper-scale
◈ Randomness and unpredictability
◈ Determinism
◈ Subject to (even subtle) attacks
We can also make use of AI/ML to predict performances of the IoT, detect subtle attacks, and make the network reactive at scale as well as for Cognitive and Predictive Analytics.
Another interesting learning from these events was that contrary to what most people might think, a larger percentage of Machine Learning deployments are deployed on-premise as opposed to on cloud. This poses an immediate opportunity for Cisco and our partners in terms of supporting our customers with their initial deployments in their own Data Centers. There are some intrinsic benefits for deploying ML on premise, among them we can list the data gravity integration and application performance, governance and TCO (Total Cost of Ownership), while on cloud deployments provide faster deployments and simplicity.
An AI/ML solution requires multidisciplinary skills and a deep collaboration between different stakeholders, including Data Scientists and Data Engineers, the CIO and the different business leaders as well as the IT team. Without all these different teams working together with a common and joint objective a successful deployment would be really difficult to realize.
The Cisco AI/ML offering focuses on Full Data Life Cycle, Simplicity, and Manageability and includes:
◈ A full portfolio for all AI/ML computing needs.
◈ Validated solutions with technology partners
◈ Natural extension of existing computing environment
The Cisco AI/ML Architecture includes UCS (Unified Computing Systems) Servers, Cisco Infrastructure Management and Cisco Networking Solutions that power a Virtualization Layer, a Converged Infrastructure for AI and Big Data Clusters which in turn sustain the AI/ML Software platforms which eventually provide the business outcomes that AI delivers. This Architecture helps to bridge the gap between IT and the Data Scientists.
There are some real use cases examples that were highlighted in these AI events which I found quite relevant and that our partners can leverage to initiate the discussion with their customers. Some of them include:
Banking
◈ Customer-Centric Marketing
◈ Product recommendation
◈ Experience personalization
◈ Attrition prediction
Operations
◈ Improve customer experience
◈ Predicting Failures
◈ Automatically Position Spares at Depots
◈ Optimizing Supply Chain and Customer Experience
Auto
◈ Autonomous Vehicle Simulations
◈ Complex simulation modelling
◈ Massive storage requirements
◈ High volume data inputs
AI/ML can also help resolve some of the Internet of Things new set of technical challenges such as:
◈ Harsh environments
◈ Hyper-scale
◈ Randomness and unpredictability
◈ Determinism
◈ Subject to (even subtle) attacks
We can also make use of AI/ML to predict performances of the IoT, detect subtle attacks, and make the network reactive at scale as well as for Cognitive and Predictive Analytics.