Security Operations Center at RSAC APJ 2019
For the 3rd year, RSAConference 2019 APJ created an educational exhibit, sponsored by RSA, Cisco and M.Tech, to monitor the RSA Conference public Wi-Fi network provided by the Marina Bay Sands (MBS). This exhibit was created in the form of the RSA Conference Security Operations Center (SOC). RSA and Cisco provided technology and staffing to monitor the network for threats, but also to educate attendees on the risks of free Wi-Fi.
What is the difference between a SOC and a NOC?
Network Operations Center
The NOC is usually responsible for monitoring and maintaining the overall network infrastructure—its primary function is to ensure uninterrupted network service
Security Operations Center
The SOC is responsible for protecting networks, as well as web sites, applications, databases, servers and data centers and other technologies
RSA and Cisco provided the SOC. The NOC was provided by the MBS.
The mission of the RSAC SOC was to ensure the conference Wi-Fi is not attacked (denial of service, laterally spreading malware, etc.). We did not block malicious DNS traffic, downloads or attachments; as this was a learning and demonstration environment. We make sure that network is protected from attackers. We locate (when we can) and advise users when they are at risk.
What technology is in the RSAC SOC?
MBS provided the RSAC SOC a span of all network traffic from the .RSACONFERENCE network, which was passed through the Cisco Next Generation Firewall / ISP and then split the traffic to NetWitness Packets NetWitness Packets and the Cisco Stealthwatch teams.
RSA used NetWitness Packets to collect and investigate all traffic on the Wi-Fi network, from the firewall; to detect deviations from normal behavior and create a probability-weighted risk score for alerts based on these results. NetWitness inspects every network packet session for threat indicators at time of collection and enriches this data with threat intelligence and business context. At the end of the conference, all of this data was wiped from NetWitness.
For suspicious files that might be malicious, NetWitness Packets checks a community AV lookup, some static analysis and its own network intelligence. Then NetWitness Malware Analysis sends the files to Cisco Threat Grid for dynamic malware analysis.
Threat Grid combines advanced sandboxing with threat intelligence into one unified solution to protect organizations from malware. Threat Grid analyzes the behavior of a file against millions of samples and billions of malware artifacts. The SOC team had a global and historical view of the malware, what it’s doing and how large a threat it posed to the RSAC network.
Threat Grid identifies key behavioral indicators of malware and their associated campaigns. The SOC team was able to save time by quickly prioritizing attacks with the biggest potential impact. We used tools like Glovebox, to safely interact with samples and observe malware behavior directly. In addition, we used Cisco Umbrella to have visibility in all DNS activity. We also used the Threat Intelligence of Cisco Threat Response and Talos Intelligence.
When the Cisco team found a potential threat, they handed it off to the RSA team for further investigation. In summary, the technology stack was:
◈ Firewall – Cisco Next Generation Firewall with IPS
◈ Full Packet Capture and Investigation – RSA NetWitness Packets
◈ Dynamic File Analysis – Cisco Threat Grid
◈ DNS / IP Intelligence – Cisco Umbrella / Cisco Umbrella Investigate
◈ Encrypted Traffic Analytics – Cisco Stealthwatch
◈ Threat Intelligence – Cisco Threat Response / Talos Intelligence
Perimeter Defences: Stopping Threats That Matter
Cisco’s Next-Generation Firewall running Firepower Threat Defence (FTD) software was set up as the perimeter security device. The firewall inspected all wireless guest traffic from event attendees, configured in monitor-only mode. FTD offers breach detection, threat discovery and security automation. Rich contextual information (such as Applications, Operating Systems, Vulnerabilities, Intrusions, and Transferred Files) served the SOC to help uncover threats lurking in the environment.
Discovered Applications
Discovered Files
Intrusion Information
During the conference, several intrusion events were recorded by FTD. Automated event analysis correlated threat events with contextual endpoint data, to identify IPS events that require immediate investigation. Whenever a working exploit targeted a vulnerable host on the guest network, an Impact 1 event was raised. For the SOC, that helped cut through the noise and focus attention to save previous time.
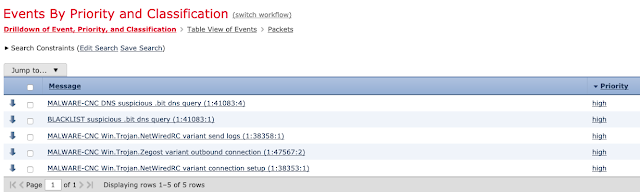
Multiple events were categorized as high priority.
One of the Impact Flag 1 events shown below, signalling about suspicious .bit query going over DNS, and associated with a Network Trojan.
The FTD would drop this communication, if it were in a production environment and configured in the active blocking mode. Reviewing the host profile, we confirmed that the target host had a large number of high-severity vulnerabilities associated with unpatched software versions. It may have been infected by malware attempting to control it remotely.
When you request a .jpg and get ransomware
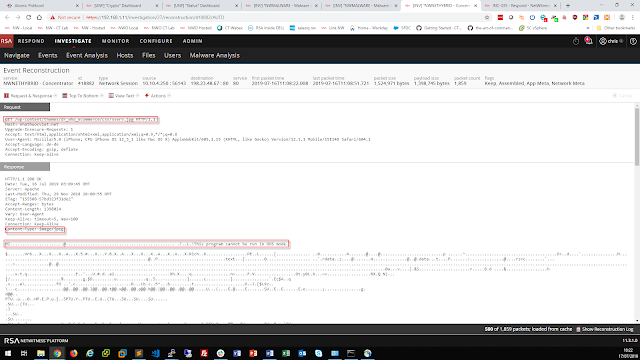
On the first day of the Conference, the SOC team observed a .JPG file served to a conference attendee who connected to a website. The .JPG file was extracted by NetWitness and found to actually have a file header of MZ, used for executables.
Since it was an executable, it was automatically sent for analysis. The static analysis had a score of 0 and 50 from the RSA Malware Analysis Community lookup, meaning it had never been detected by dozens of AV vendors.
The Dynamic Analysis/Sandbox score from Threat Grid was 100, meaning confirmed malicious based on behavior. The team went into action to assess the threat.
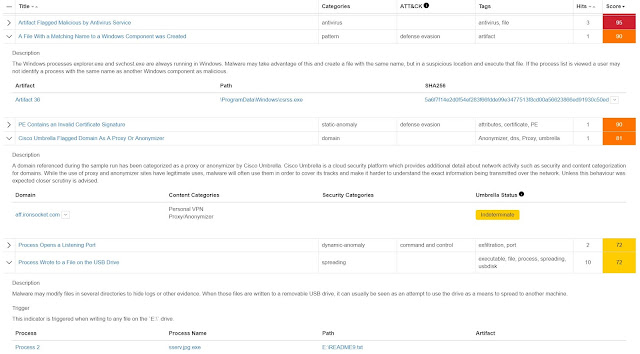
The supposed .JPG file was assigned a Threat Score of 100 for the Behavior of Troldesh Ransomware Detected. Troldesh, also known as Shade, is a Russian-targeted Ransomware variant written in Visual Basic. It will encrypt user files and request a ransom to be delivered after contacting a supplied e-mail address. All encrypted files will have an .xtbl extension appended to them.
We also noted the sample attempted to hide itself as a Windows system file, opened up a Personal VPN – Proxy/Anonymizer and wrote files to a USB drive.
We pivoted to Threat Response to learn more and determine if it had been seen before.
With Threat Response we were able to have a global view of the file, that it was first seen November 2018. In a production environment, this threat intelligence would have blocked the file on all integrated Cisco Security platforms.
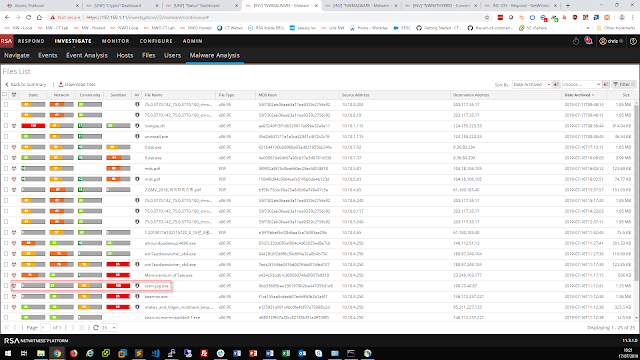
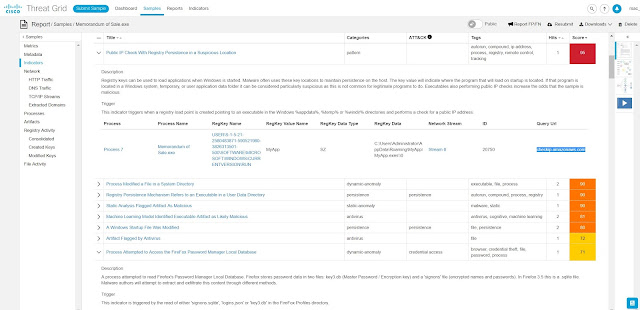
The NetWitness team investigated the machine that requested the .jpg and confirmed it downloaded other suspicious files.
One of those was titled Memorandum of Sale, but also was an executable that attempts to steal Firefox passwords.
Phishing attack
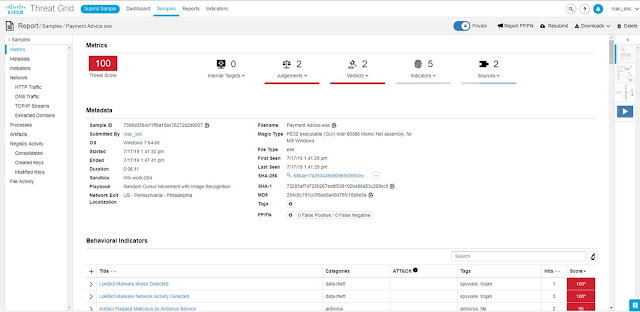
We also saw a phishing attack, masquerading as a banking email. NetWitness reconstructed the email and sent the attachments to Threat Grid for analysis.
The Payment Advice attachment was actually the LokiBot malware.
Standing up a malicious domain for 24 hours
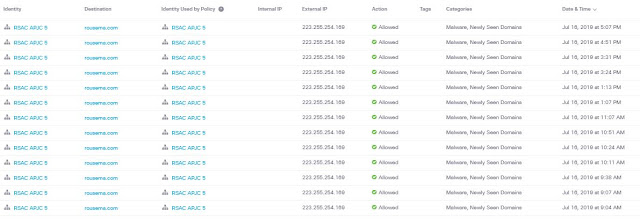
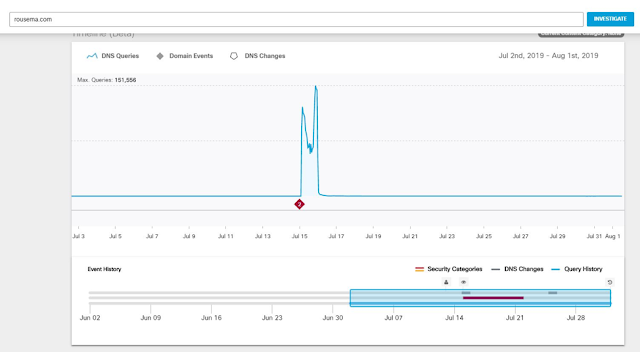
On the first day of the conference, we noticed some suspicious DNS traffic in Umbrella to a newly created domain. The requests happened throughout the day.
We moved to Umbrella Investigate to learn more and confirmed the sudden malicious activity of 0 DNS requests to over 120,000 global requests.
The requests spiked to 151,000 over the 24-hour period and then they stopped, globally.
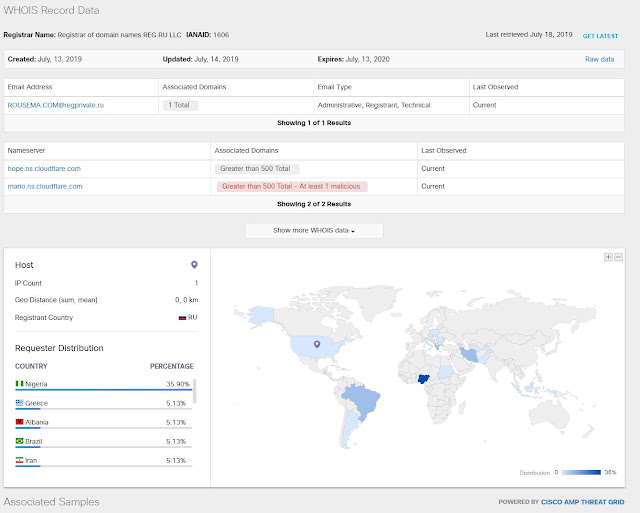
We could see the domain was registered in Russia and the distribution of the requesters.
Looking at the NetWitness logs, we could see all requests from RSAC came from Android devices.
Outbound traffic for hostname rousema[.]com [208.67.220.220] we can see 13 sessions from 10:50 AM - 16:50 PM SGT Tues 16th/Jul.
service type UDP DNS & HTTPS
This is originating from 3 IPs
10.10.1.143 Android 9 Samsung Phone sm-g955f running dalvik/2.1.0, Samsung M1client daylite/3.0.05.9 & x86_64 Linux - 11:06 AM SGT - 15:23 PM - (All traffic from IP from 10:31 AM - 16:59 PM)
10.10.5.9 Android 7.0 Phone trt-l21a running dalvik/2.1.0 & Android 2.2 - 10:50 AM SGT - 17:06 PM - (All traffic from IP from 10:51 AM - 23:19 PM)
10.10.2.31 x86_64 Linux & Android 9 Samsung Phone sm-n950f running dalvik/2.1.0(13:12 AM SGT - 13:12 PM - (All traffic from IP from 10:31 AM - 14:16 PM)
Dalvik is the discontinued process Virtual Machine in Android 4.4 and earlier
It was a textbook example of a temporary domain infrastructure that would be blocked in a production environment.
Overall, we saw over 5m DNS requests during RSAC APJ. A couple of thousand would have been blocked in a production environment.
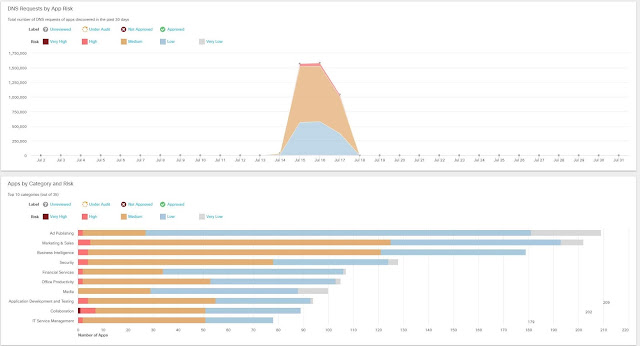
We were also able to have visibility in the 2,001 apps that had DNS activity during the conference.
Stealthwatch brings additional network visibility
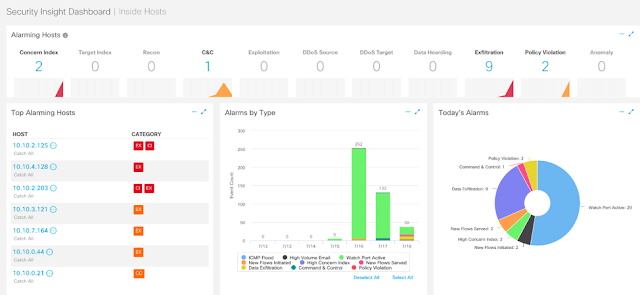
Stealthwatch detected insider threat activities like Command & Control activity and Data Exfiltration just over the baseline period of two days, indicating potential threats on the network.
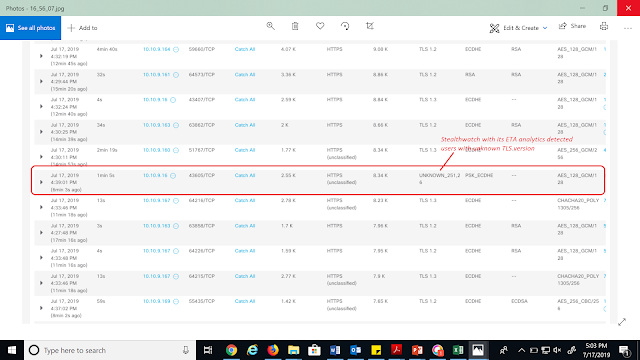
The solution with its unique ability to look at encrypted traffic without decryption, also detected users with unknown TLS version.
Now we can extend this comprehensive visibility to cloud networks as well with an offering called Stealthwatch Cloud.