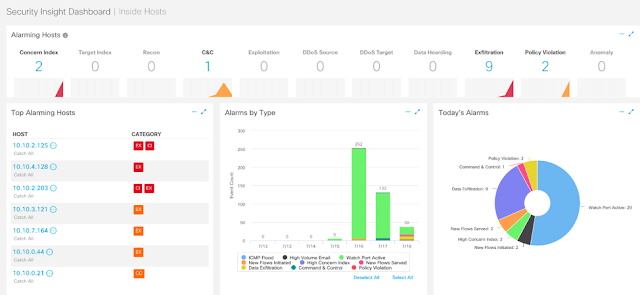
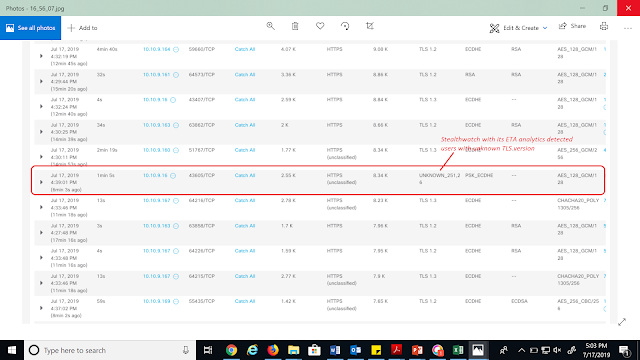
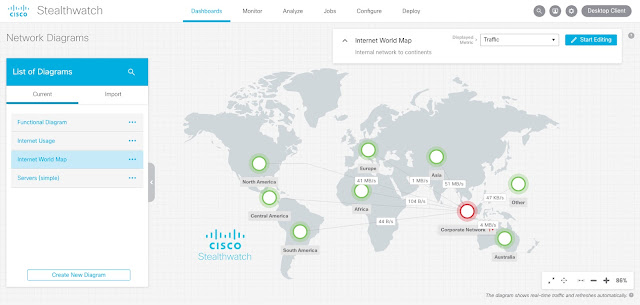
Every time you interact with a business of any type, you have an idea or an inkling of how that interaction will go. That’s the expectation. If the business exceeds your expectation in a noticeable way, you have a great experience. If the business falls short of your expectation, you think the opposite.
The best companies in the world, don’t do a lot of marketing. Do you know why? They operationalize something about their business that motivates their customers to become volunteer marketers on their behalf.
Word of mouth is more important than ever. We trust each other twice as much as we trust brands. It’s the most powerful and persuasive form of marketing.
Everybody thinks word of mouth is important. Between 50 and 91% of all purchases are influenced by word of mouth, but very few companies have a strategy for it. We assume our customers will talk about us, but will they? The biggest mistake we make is assuming that competency creates conversation, that being a good business is enough to get people to tell the story. But all your competitors are also good. Good enough is not enough.
A talk trigger is a strategic, operational differentiator that compels word of mouth. It causes your customers to involuntarily talk about your business. A Talk Trigger isn’t a surprise-and-delight social media tactic, nor is it a gimmick. It doesn’t involve Drake, Rhianna or Cardi B. Oftentimes, it’s something quite ordinary, like a business card, company hold music, or a pre-meeting phone call, that you choose to make different.
A Talk Trigger can also help you exceed customer expectations. Why? Because your customers aren’t expecting it. There are the five distinct types of Talk Triggers. These are the conversational levers you can pull:
You can be more human than your customers expect.
You can be more useful than your customers expect.
You can be more generous than your customers expect.
You can be more responsive than your customers expect.
You can be more playful than your customers expect.
Each of these types of Talk Triggers is talkable. One isn’t more advantageous than the other. However, one might be a better fit for your business or for your brand, and that’s a key ingredient of creating a Talk Trigger that will have word of mouth success. Let’s take a look at each one.
Be More Human Than Your Customers Expect
These days, empathy from business is in short supply for two main reasons. The first is empathy requires inconsistency and listening. It requires interacting with customers as individuals. This approach, by definition, drives up the per-interaction cost every time a business intersects with the customer. The second reason is that empathetic interactions means that employees must have permission to work outside of a script. For many companies, the concern of risk involved is too great.
This is why, when businesses choose the opposite approach, being empathetic and human can have a massive word of mouth impact.
Be More Useful Than Your Customers Expect
Not all businesses and organizations have the heart to be disproportionately empathetic, and that’s OK. For those companies, it may make more sense create a word of mouth engine that is more logical and useful. In 2013, I wrote Youtility: Why Smart Marketing is About Help, Not Hype that showed businesses how to attract customers by providing online content that informs and educates. This idea can work as a Talk Trigger, too.
This Talk Trigger archetype is most-likely to be noticed in an industry or business-setting that is not known for being helpful or making customers’ lives easier. Being different than what’s expected creates a Talk Trigger and helps your business solve the customer experience formula.
Be More Generous Than Your Customers Expect
Consumers are besieged by companies giving them less for the same price, or worse, for a higher price. We are surrounded by this phenomenon, also known as “shrinkflation.” According to a study by the National Statistics in the United Kingdom, 2,529 products decreased in size between 2012 and 2017. The ubiquity of shrinkflation is why showing your customers the opposite, showing generosity, can be an effective Talk Trigger.
Generosity creates conversation because customers are stunned that, as a business, you’ve decided to give something away… for free.
Be More Responsive Than Your Customers Expect
Forty-one percent of consumers say that when they contact a business, getting their issue quickly is the most important element of that customer service interaction. Nine out of ten American consumers refuse to wait on hold for more than five minutes when they’ve called a business.
Speed matters, but it’s also a moving target. What was considered “fast” in 2000 is now slow. What was considered “fast” in 2010 is table stakes for most businesses in 2019. This relentlessness of the changing pace and expectations around speed and responsiveness means there’s an exceptionally high standard for a company to make this a Talk Trigger.
Be More Playful Than Your Customers Expect
When asked to describe a business, most customers don’t think to mention the word “fun” or “amusing.” Most businesses are difficult to describe because there are a limited number of synonyms for the word “fine.”
Like the other Talk Trigger archetypes on this list, this fact presents an opportunity for businesses. The expectation is that your business will be vanilla, which means adding a little flair will create chatter.
Whichever Talk Trigger archetype is right for your business, we’re trying to do the same thing. We’re creating a circumstance where your customers say these words, “You won’t believe what happened to me when [FILL IN THE BLANK]…”
Your customer experience is what fills in that blank.