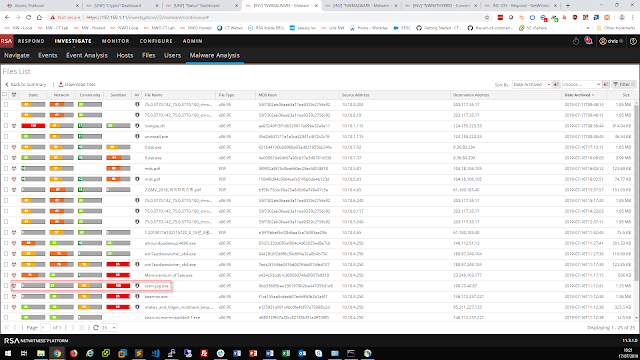
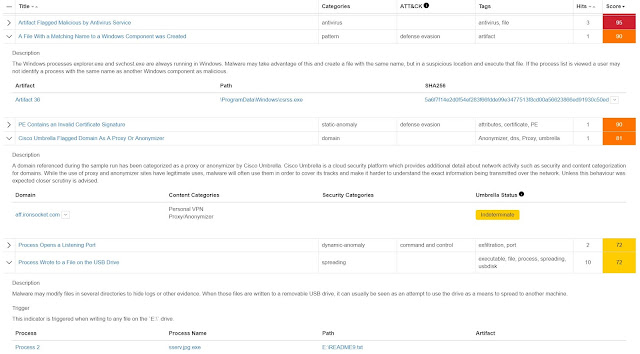
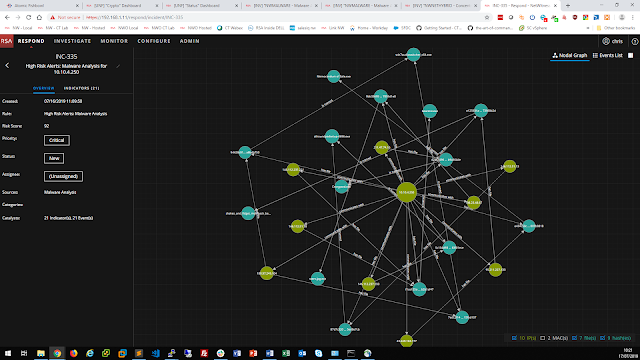
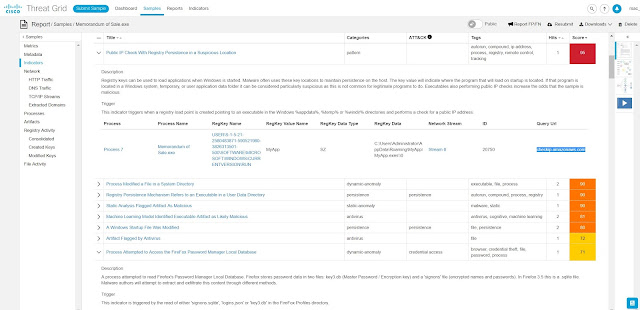
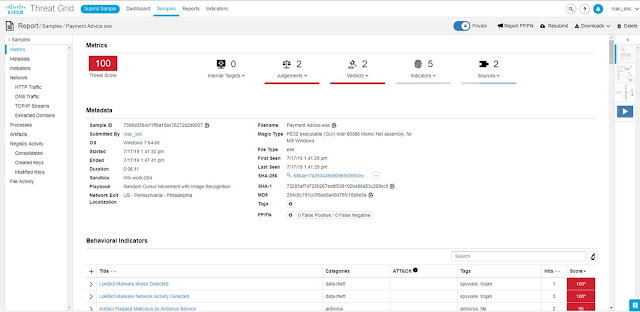
A configuration mistake or purposeful mis-configuration is no joke. But it does illustrate how a misconfigured network can quickly become a security event (or it may already be one and your team does not know it). But how do you distinguish normal network activity from abnormal? Without visibility into every corner of the network (including the virtual world of the data center), and some ability to compare current vs. baseline, it can be extremely difficult and there may be many “little events” that remain hidden to you.
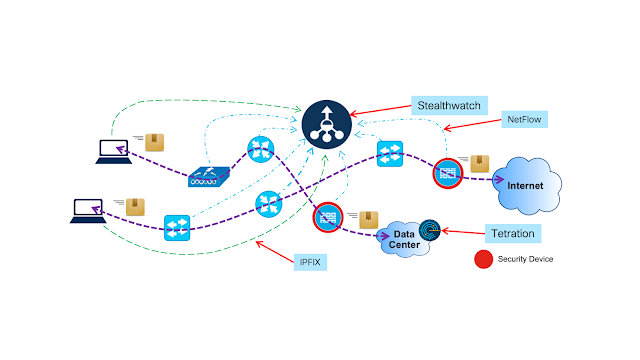
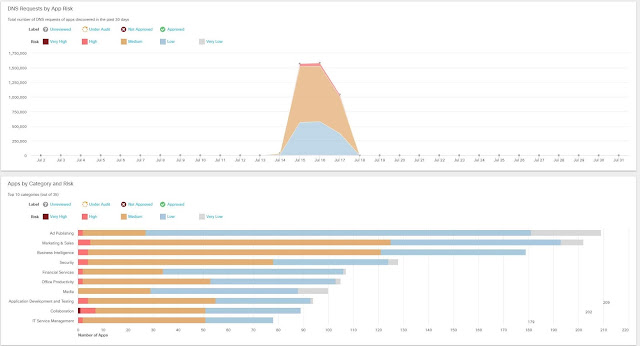
This story does raise the question, how do you enable the benefits of deeper network visibility? That capability is provided by Cisco Stealthwatch. It enables you to strategically analyze the collective telemetry from NetFlow and IP Flow Information Export (IPFIX), two protocols every network device can export (see figure 1).
Deeper network visibility enabled
This story does raise the question, how do you enable the benefits of deeper network visibility? That capability is provided by Cisco Stealthwatch. It enables you to strategically analyze the collective telemetry from NetFlow and IP Flow Information Export (IPFIX), two protocols every network device can export (see figure 1).
Figure 1. Stealthwatch collects NetFlow and IPFIX from every network device for Visibility.
You can also add value to your data center through Cisco Tetration. It provides unmatched visibility into behavioral deviations, whether terrestrial or cloud-based. While “behavioral visibility” is a bit different than the visibility discussion so far, it is critical to the protection and operation of the modern data center. A good example is one we saw recently with one of our customers, where a seemingly insignificant and otherwise undetected data stream out of the data center turned out to be a command and control channel. Thankfully for the customer, Tetration uncovered the threat in less than 30 seconds.
Deeper visibility + identity = attribution
Visibility in modern IT networks must go beyond the mere identification of packet flows. User identity should also be linked to packet flows wherever possible. Look at it this way, if you want to reach max visibility, think:
Visibility + Identity = Attribution
With attribution, you can see unexpected or undesired network behavior, plus you can link that behavior back to individual actors on your network. It is no longer just “some machine that did something weird.” Instead it is a concrete action with a concrete identity: such as “RedGuy” at “3:20pm” reached out to a “Command and Control” site (whether he meant to or not), becoming patient zero for your next computer epidemic.
The power of deeper visibility into your network
To help illustrate the power of deeper visibility on your network, consider another actual event we can all relate to. A contractor (let’s call him BlueGuy) goes to work. It’s Saturday and the office is empty. In the quiet loneliness all around, he begins downloading terabytes of data from another site. This continues, with downloads sprinkled throughout the day. Some may consider this suspicious behavior.
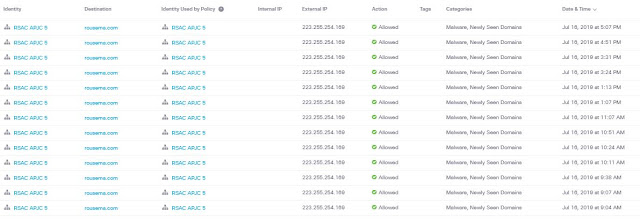
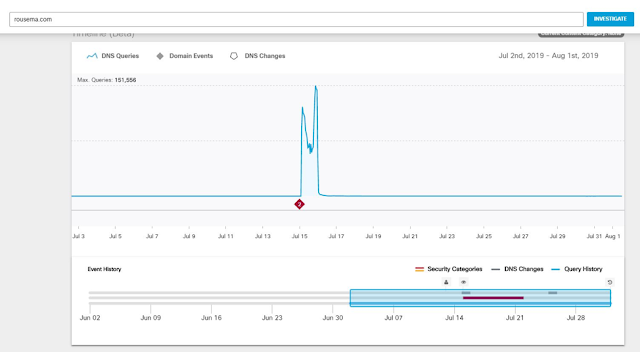
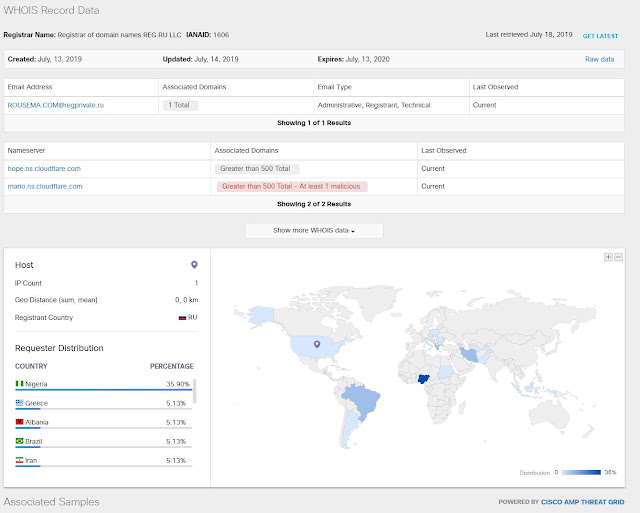
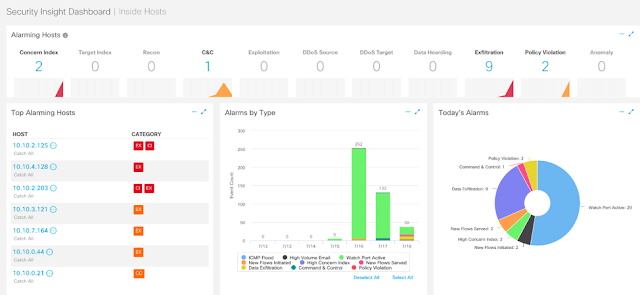
On most networks this might go unnoticed. But as Stealthwatch observes network activity in its entirety, it understands this behavior is not normal, based on previous baselines. As a result, this behavior is considered excessive. As Stealthwatch constantly monitors all the network transactions, it detects BlueGuy’s activity and it reports on it. In its communication with the Cisco Identity Services Engine (ISE), individual identity is assigned to the network data flows, and attribution is achieved. BlueGuy is busted.
Initially, it may seem that no good can come of this type of network activity. But upon further investigation, it turns out that BlueGuy uses the office on weekends to study for his Cisco CCNA. While he does this on his own time, he must do so from the office network because the courseware is on a corporate network at another site (this explains the enormous data exchanges). So it is revealed as a harmless event, rather than a massive data breach. Yet the entire episode would have remained unknown without complete network visibility. What if it had been a breach? Would your network have seen it?
SGTs, NetFlow, IPFIX and the world of packet flow
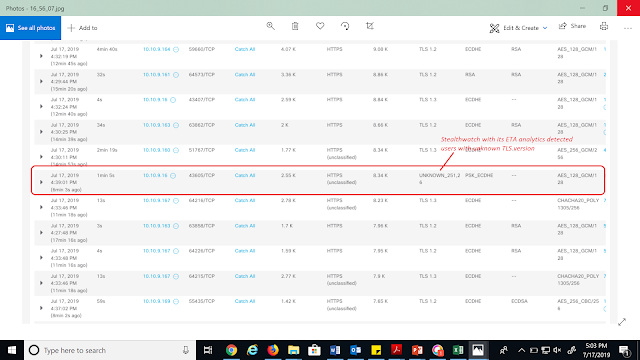
In this latest example, the two primary tools used are Cisco Stealthwatch and Cisco ISE. ISE adds attribution to the NetFlow/IPFIX packet flow collected by Stealthwatch. With Scalable Group Tags (SGTs), ISE tags all packets as they enter the network. SGTs can be used for both identification and enforcement anywhere in the network.
Of course, Stealthwatch sees all packet flows via NetFlow/IPFIX and performs analysis based on all network data, including the SGTs. Individual attribution is achieved via pxGrid communications between Stealthwatch and ISE. These results can then be presented to an administrator for disposition, including quarantine (see Figure 2).
Figure 2 – ISE adds Attribution to the Visibility story.
What about firewalls?
You may have noticed in both Figures 1 and 2 there are far more network devices than there are security devices. This is typical in any network. However, both visibility and attribution must rely on the entire network fabric to assist with the goal of complete visibility.
As you can see in the diagrams, putting your faith in security devices alone for visibility can fail (or certainly fall short). While the deployment of additional firewalls (or other assorted security devices) may add more points of visibility, no number of firewalls can achieve what you can by using the entire network as a sensor.
The Zero Trust wasteland
When it comes to securing Federal government networks, a few Zero Trust models have emerged recently, along with the thought that a network should be viewed as an untrusted wasteland of packet freeways where all security should focus on data. But it would be unwise to simply dismiss the incredible power of identity and visibility combined (attribution).
For IT leaders, the track record is clear: controlling entry and monitoring activity of users in the corporate/government network is the best way to track offensive behavior or bad actors. This approach can give you the capability to control, or even eliminate, threats before they reach your data.
Or, to relate it in everyday language, when we let strangers into our homes, we don’t pause and quickly weld the refrigerator door shut and disable the WiFi. Instead, we use common sense: screening them before they enter, watching their behavior as they do so and ensuring their actions inside our home are acceptable. If they do take a peek into our fridge, we may trust (thanks to attribution) that they are not necessarily going after the last of the cupcakes. But if they do, we’ll be ready.