While ZTA is already present in many cybersecurity policies and programs that sought to restrict access to data and resources, this document is intended to both “abstractly define” ZTA and provide more guidance on deployment models, uses cases and roadmaps to implementation.
What’s the problem they’re trying to solve? Agencies and enterprise networks have given authorized users broad access to resources, since they’ve traditionally focused on perimeter defenses. But that’s led to lateral movement within the network – one of the biggest security challenges for federal agencies.
Realistically, NIST recognizes that the migration to a ZTA is more of a journey rather than a complete replacement of an enterprise’s infrastructure. Most enterprises will likely continue to operate in a hybrid model – of both zero trust + legacy mode – for awhile as they continue their IT modernization investments.
And despite the misleading name, they state that ZTA is not a single network architecture, but rather a set of guiding principles.
◉ A shift away from wide network perimeters to a narrower focus on protecting individual or small groups of resources
◉ No implicit trust is granted to systems based on their physical or network location
While traditional methods block attacks coming from the internet, they may not be effective at detecting or blocking attacks originating from inside the network.
ZTA seeks to focus on the crux of the issue, which NIST defines as two main objectives:
1. Eliminate unauthorized access to data and services
2. Make the access control enforcement as granular as possible
NIST lists out a few conceptual guidelines that the design and deployment of a ZTA should align with (summarized for brevity below):
1. All data and computing services are considered resources. For example, an enterprise might classify personally-owned devices as resources, if they’re allowed to access enterprise resources.
2. All communication is secure regardless of network location. This means access requests from within the network must meet the same security requirements as those from outside of it, and communication must be encrypted and authenticated.
3. Access to individual enterprise resources is granted on a per-connection basis. The trust of whatever is requesting access is evaluated before granted access – authentication to one resource doesn’t automatically mean they get access to another resource.
4. Access to resources is determined by policy, including the state of user identity and the requesting system, and may include other behavioral attributes. NIST defines ‘user identity’ as a network account used to request access, plus any enterprise-assigned attributes to that account. A ‘requesting system’ refers to device characteristics (software versions, network location, etc.). ‘Behavioral attributes’ include user & device analytics, any behavior deviations from baselined patterns.
5. The enterprise ensures all owned and associated systems are in the most secure state possible, while monitoring systems to ensure they remain secure. Enterprises need to monitor the state of systems and apply patches or fixes as needed – any systems discovered to be vulnerable or non-enterprise owned may be denied access to enterprise resources.
6. User authentication is dynamic and strictly enforced before access is allowed. NIST refers to this as a ‘constant cycle of access’ of threat assessment and continuous authentication, requiring user provisioning and authorization (the use of MFA for access to enterprise resources), as well as continuous monitoring and re-authentication throughout user interaction.
What follows is a summary of some of the key potential ZTA threats listed in the publication:
Insider Threat
To reduce the risk of an insider threat, a ZTA can:
◉ Prevent a compromised account or system from accessing resources outside of how it’s intended
◉ MFA for network access can reduce the risk of access from a compromised account
◉ Prevent compromised accounts or systems from moving laterally through the network
◉ Using context to detect any access activity outside of the norm and block account or system access
To prevent the threat of unauthorized access, Duo provides MFA for every application, as part of the Cisco Zero Trust framework. An additional layer of identity verification can help mitigate attacker access using stolen passwords or brute-force attacks. That paired with Duo’s device insight and policies provides a solid foundation for zero trust for the workforce.
Learn more about Duo’s new federal editions tailored to align with:
◉ FedRAMP/FISMA security controls
◉ NIST’s Digital Identity Guidelines (NIST SP 800-63-3)
◉ FIPS 140-2 compliance
Network Visibility
In a ZTA, all traffic should be inspected, logged and analyzed to identify and respond to network attacks against the enterprise. But some enterprise network traffic may be difficult to monitor, as it comes from third-party systems or applications that cannot be examined due to encrypted traffic.
In this situation, NIST recommends collecting encrypted traffic metadata and analyzing it to detect malware or attackers on the network. It also references Cisco’s research on machine learning techniques for encrypted traffic (section 5.4, page 22):
“The enterprise can collect metadata about the encrypted traffic and use that to detect possible malware communicating on the network or an active attacker. Machine learning techniques [Anderson] can be used to analyze traffic that cannot be decrypted and examined. Employing this type of machine learning would allow the enterprise to categorize traffic as valid or possibly malicious and subject to remediation.”
Cisco Encrypted Traffic Analytics (ETA) allows you to detect and mitigate network threats in encrypted traffic to gain deeper insight without decryption. It also allows you to quickly contain infected devices and uses, while securing your network. Paired with Cisco Stealthwatch, you can get real-time monitoring using machine learning and context-aware analysis.
The publication also references having a strong Continuing Diagnostics and Mitigations (CDM) program as “key to the success of ZTA.”
This is a complete inventory of physical and virtual assets. In order to protect systems, agencies need insight into everything on their infrastructure:
◉ What’s connected? The devices, applications and services used; as well as the security posture, vulnerabilities and threats associated.
◉ Who’s using the network? The internal and external users, including any (non-person) entities acting autonomously, like service accounts that interact with resources.
◉ What is happening on the network? Insight into the traffic patterns, messages and communication between systems.
◉ How is data protected? Enterprise policies for how information is protected, both at rest and in transit.
Having visibility into the different areas of connectivity and access provides a baseline to start evaluating and responding to activity on and off the network.
Asking the above discovery questions and finding a solution that can accurately and comprehensively answer them can be challenging, as it requires user, device, system and application telemetry that spans your entire IT environment – from the local corporate network to branches to the multi-cloud; encompassing all types of users from employees to vendors to contractors to remote workers, etc.
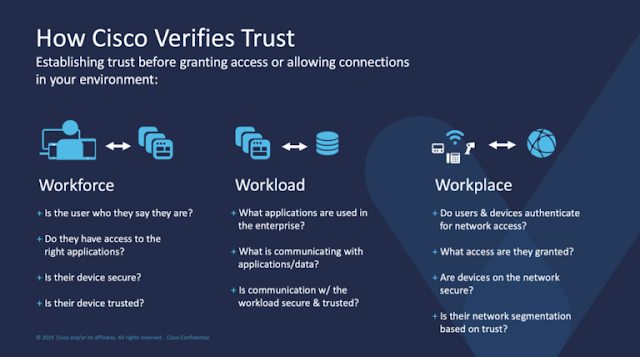
Get visibility into everything on your infrastructure, and get control over who can access what, on an ongoing basis. Cisco Zero Trust provides a comprehensive approach to securing all access across your applications and environment, from any user, device and location. It protects your workforce, workloads and workplace.
It is comprised of a portfolio of the three following primary products:
◉ To protect the workforce, Duo Security ensures that only the right users and secure devices can access applications.
◉ To protect workloads, Tetration secures all connections within your apps, across multi-cloud.
◉ To protect the workplace, SD-Access secures all user and device connections across your network, including IoT.
This complete zero-trust security model allows you to mitigate, detect and respond to risks across your environment. Verifying trust before granting access across your applications, devices and networks can help protect against identity-based and other access security risks.
What’s the problem they’re trying to solve? Agencies and enterprise networks have given authorized users broad access to resources, since they’ve traditionally focused on perimeter defenses. But that’s led to lateral movement within the network – one of the biggest security challenges for federal agencies.
Realistically, NIST recognizes that the migration to a ZTA is more of a journey rather than a complete replacement of an enterprise’s infrastructure. Most enterprises will likely continue to operate in a hybrid model – of both zero trust + legacy mode – for awhile as they continue their IT modernization investments.
And despite the misleading name, they state that ZTA is not a single network architecture, but rather a set of guiding principles.
The overall design denotes:
◉ A shift away from wide network perimeters to a narrower focus on protecting individual or small groups of resources
◉ No implicit trust is granted to systems based on their physical or network location
While traditional methods block attacks coming from the internet, they may not be effective at detecting or blocking attacks originating from inside the network.
ZTA seeks to focus on the crux of the issue, which NIST defines as two main objectives:
1. Eliminate unauthorized access to data and services
2. Make the access control enforcement as granular as possible
Zero Trust Architecture Tenets
NIST lists out a few conceptual guidelines that the design and deployment of a ZTA should align with (summarized for brevity below):
1. All data and computing services are considered resources. For example, an enterprise might classify personally-owned devices as resources, if they’re allowed to access enterprise resources.
2. All communication is secure regardless of network location. This means access requests from within the network must meet the same security requirements as those from outside of it, and communication must be encrypted and authenticated.
3. Access to individual enterprise resources is granted on a per-connection basis. The trust of whatever is requesting access is evaluated before granted access – authentication to one resource doesn’t automatically mean they get access to another resource.
4. Access to resources is determined by policy, including the state of user identity and the requesting system, and may include other behavioral attributes. NIST defines ‘user identity’ as a network account used to request access, plus any enterprise-assigned attributes to that account. A ‘requesting system’ refers to device characteristics (software versions, network location, etc.). ‘Behavioral attributes’ include user & device analytics, any behavior deviations from baselined patterns.
5. The enterprise ensures all owned and associated systems are in the most secure state possible, while monitoring systems to ensure they remain secure. Enterprises need to monitor the state of systems and apply patches or fixes as needed – any systems discovered to be vulnerable or non-enterprise owned may be denied access to enterprise resources.
6. User authentication is dynamic and strictly enforced before access is allowed. NIST refers to this as a ‘constant cycle of access’ of threat assessment and continuous authentication, requiring user provisioning and authorization (the use of MFA for access to enterprise resources), as well as continuous monitoring and re-authentication throughout user interaction.
Zero Trust Architecture Threats
What follows is a summary of some of the key potential ZTA threats listed in the publication:
Insider Threat
To reduce the risk of an insider threat, a ZTA can:
◉ Prevent a compromised account or system from accessing resources outside of how it’s intended
◉ MFA for network access can reduce the risk of access from a compromised account
◉ Prevent compromised accounts or systems from moving laterally through the network
◉ Using context to detect any access activity outside of the norm and block account or system access
To prevent the threat of unauthorized access, Duo provides MFA for every application, as part of the Cisco Zero Trust framework. An additional layer of identity verification can help mitigate attacker access using stolen passwords or brute-force attacks. That paired with Duo’s device insight and policies provides a solid foundation for zero trust for the workforce.
Learn more about Duo’s new federal editions tailored to align with:
◉ FedRAMP/FISMA security controls
◉ NIST’s Digital Identity Guidelines (NIST SP 800-63-3)
◉ FIPS 140-2 compliance
Network Visibility
In a ZTA, all traffic should be inspected, logged and analyzed to identify and respond to network attacks against the enterprise. But some enterprise network traffic may be difficult to monitor, as it comes from third-party systems or applications that cannot be examined due to encrypted traffic.
In this situation, NIST recommends collecting encrypted traffic metadata and analyzing it to detect malware or attackers on the network. It also references Cisco’s research on machine learning techniques for encrypted traffic (section 5.4, page 22):
“The enterprise can collect metadata about the encrypted traffic and use that to detect possible malware communicating on the network or an active attacker. Machine learning techniques [Anderson] can be used to analyze traffic that cannot be decrypted and examined. Employing this type of machine learning would allow the enterprise to categorize traffic as valid or possibly malicious and subject to remediation.”
Cisco Encrypted Traffic Analytics (ETA) allows you to detect and mitigate network threats in encrypted traffic to gain deeper insight without decryption. It also allows you to quickly contain infected devices and uses, while securing your network. Paired with Cisco Stealthwatch, you can get real-time monitoring using machine learning and context-aware analysis.
Zero Trust Architecture: Continuous Monitoring
The publication also references having a strong Continuing Diagnostics and Mitigations (CDM) program as “key to the success of ZTA.”
This is a complete inventory of physical and virtual assets. In order to protect systems, agencies need insight into everything on their infrastructure:
◉ What’s connected? The devices, applications and services used; as well as the security posture, vulnerabilities and threats associated.
◉ Who’s using the network? The internal and external users, including any (non-person) entities acting autonomously, like service accounts that interact with resources.
◉ What is happening on the network? Insight into the traffic patterns, messages and communication between systems.
◉ How is data protected? Enterprise policies for how information is protected, both at rest and in transit.
Having visibility into the different areas of connectivity and access provides a baseline to start evaluating and responding to activity on and off the network.
Cisco Zero Trust
Asking the above discovery questions and finding a solution that can accurately and comprehensively answer them can be challenging, as it requires user, device, system and application telemetry that spans your entire IT environment – from the local corporate network to branches to the multi-cloud; encompassing all types of users from employees to vendors to contractors to remote workers, etc.
It is comprised of a portfolio of the three following primary products:
◉ To protect the workforce, Duo Security ensures that only the right users and secure devices can access applications.
◉ To protect workloads, Tetration secures all connections within your apps, across multi-cloud.
◉ To protect the workplace, SD-Access secures all user and device connections across your network, including IoT.
This complete zero-trust security model allows you to mitigate, detect and respond to risks across your environment. Verifying trust before granting access across your applications, devices and networks can help protect against identity-based and other access security risks.