Corporate social responsibility (CSR) is core to our purpose, our culture, and how we invest. We focus on People, Society, and Planet—issues that align with our business strategy and where we can have the greatest potential for impact. Our success is built on a Conscious Culture, where trustworthiness and ethical conduct are expected and supported among our employees, suppliers, and business partners.
How we manage CSR
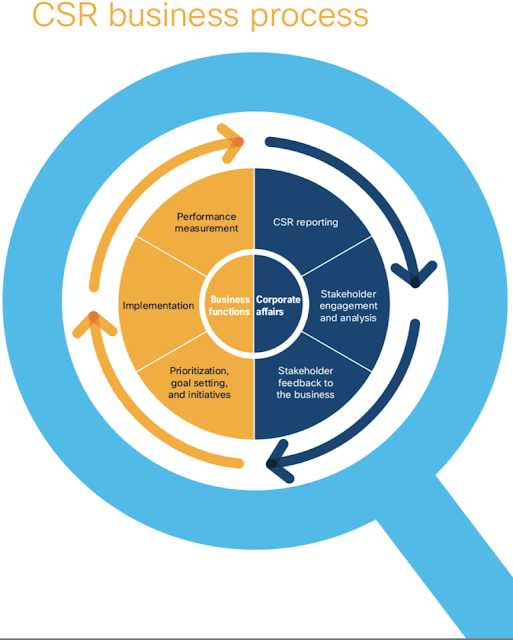
Corporate Affairs, as part of the Human Resources organization, champions Cisco’s strategic approach to CSR, including social investment programs and environmental sustainability. The organization also stewards our commitments to CSR performance and transparency. The Corporate Affairs team is responsible for:
◉ Defining and managing our social investment strategy and programs
◉ Driving CSR governance processes
◉ Collaborating with a broad range of stakeholders
◉ Conducting socio-economic research and developing data driven insights
◉ Assessing and monitoring CSR priority issues
◉ Producing our annual CSR Report
◉ Coordinating and ensuring cross-functional ESG alignment
Business functions own CSR priorities. Teams integrate priorities into their business strategy by setting goals, implementing plans, and measuring performance. Some priorities touch multiple functions. In these cases, we establish cross-functional teams to align CSR business process and implement against our commitments. In some cases, CSR goals and objectives may be linked to performance factors and compensation for CSR owners. For example, Supplier Code of Conduct performance may be considered when assessing the performance of key supply chain leaders.
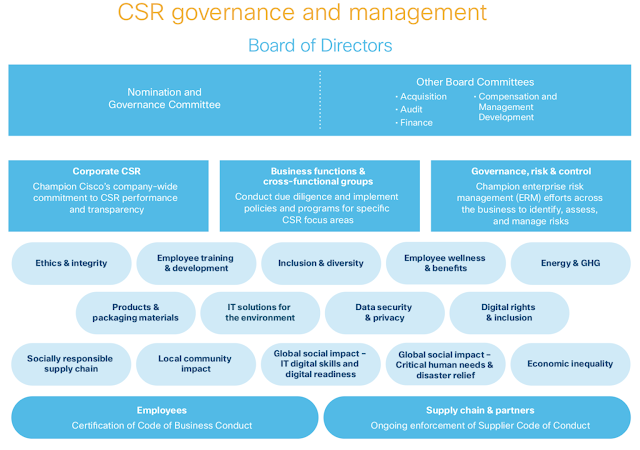
We believe that risk is inherent in innovation and the pursuit of long-term growth opportunities. Cisco’s management is responsible for day-to-day risk management activities. The Board of Directors, acting directly and through its committees, is responsible for the oversight of risk management.
Cisco’s management has implemented an enterprise risk management (ERM) program, managed by Cisco’s internal audit function, that is designed to work across the business to identify, assess, govern, and manage risks and Cisco’s response to those risks. Cisco’s internal audit function performs an annual risk assessment that is utilized by the ERM program.
The Audit Committee, which oversees our financial and risk management policies, including data protection (comprising both privacy and security), receives regular reports on ERM from the chair of the ERM operating committee, as well as regular reports on cybersecurity from Cisco’s Chief Security and Trust Officer. Other Board committees oversee certain categories of risk associated with their respective areas of responsibility.
The Nomination and Governance Committee of the Board reviews Cisco’s policies and programs concerning corporate social responsibility, including environmental, social, and governance matters. CSR and environmental sustainability are represented through Tae Yoo, Senior Vice President of Corporate Affairs, and Francine Katsoudas, Executive Vice President and Chief People Officer.
Engaging with stakeholders
Building bridges of understanding with key stakeholders helps us maximize impact and informs our materiality process. Through regular dialogue, we can better align our business to social and environmental needs.
We partner with a wide range of global and local organizations to shape and extend the reach of our CSR programs, including governments, nonprofits, multilateral organizations, and peers. We have been a strategic partner of the World Economic Forum (WEF) since 2002. Our engagement with the WEF provides us with world leader insights, influences our CSR strategy, and enables us to learn from others and share best practices. Other partnerships and memberships include: Business for Social Responsibility (BSR); the Conference Board’s Sustainability Council II on Innovation and Growth; the CEF (formerly the Corporate Eco Forum); and the Responsible Business Alliance (formerly the EICC or Electronic Industry Citizenship Coalition).
In addition to the formal materiality assessment, Cisco’s environment team independently gathers feedback on emerging issues, the quality of our reporting, and our sustainability performance from sources including stakeholder inquiries and key rankings and ratings. “Stakeholder inquiries” is the umbrella term we use for questions we receive from a variety of sources, including:
◉ Customers and partners. The visibility of environmental sustainability continues to increase in customer and partner requests for proposal (RFP), supplier qualification, and contract processes.
◉ Employees
◉ Financial and industry analysts
◉ Shareholders and investors
◉ Sustainability data aggregators, which includes companies like Ecovadis that collect sustainability information for our customers and partners. It also includes a range of organizations that collect and package sustainability information for resale or for their own analysis.
◉ Environmental advocacy groups
◉ Academia, including researchers and students
◉ Media
Environment-related topics form the vast majority of stakeholder inquiries that Cisco receives. These inquiries provide continuous, real-time insight into the environmental issues of interest to different categories of stakeholders. In FY19, we continued to see increasing customer and investor interest in environmental sustainability, as reflected in customer requests for proposals, customer and environmental advocacy surveys, and other inquiries.