Similar to what most of our customers are doing these days, the majority of my working hours are spent working from my home office. It’s not a new experience for me. At Cisco, we have always been good at using our own technology to run our business, so working from home is common for most Cisco employees.
My home office setup provides me with the same experience I’m used to in the office – same secure corporate Wi-Fi network run off a Cisco access point, a Cisco DX video end point for Cisco Webex meetings and nothing more.
This is exactly the need we are seeing at our customers, as they look to enable their remote workforce. A secure solution, deployed quickly and at scale.
Never in recent memory has IT around the world needed to address a crisis such as this in such a short time. Never in recent history has the network played such a crucial role in keeping businesses going when everything else stops. IT and the network are now at the forefront, the only enabler for businesses to continue operating.
Business continuity is the name of the game, but what are the easiest ways to get that critical element of network connectivity up and running?
Let’s unpack the three main challenges that customers are struggling with today:
My home office setup provides me with the same experience I’m used to in the office – same secure corporate Wi-Fi network run off a Cisco access point, a Cisco DX video end point for Cisco Webex meetings and nothing more.
This is exactly the need we are seeing at our customers, as they look to enable their remote workforce. A secure solution, deployed quickly and at scale.
Never in recent memory has IT around the world needed to address a crisis such as this in such a short time. Never in recent history has the network played such a crucial role in keeping businesses going when everything else stops. IT and the network are now at the forefront, the only enabler for businesses to continue operating.
Business continuity is the name of the game, but what are the easiest ways to get that critical element of network connectivity up and running?
Let’s unpack the three main challenges that customers are struggling with today:
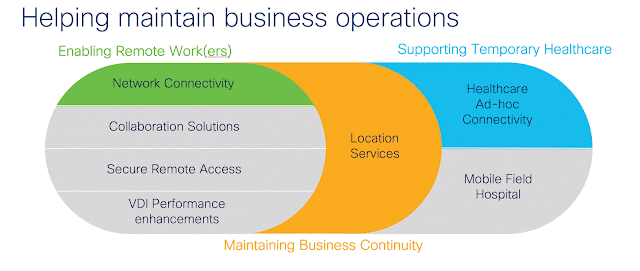
Enabling Remote Work(ers)
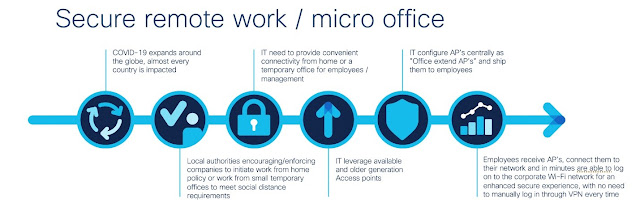
With a pandemic like this one, governments are attempting to slow down the spread of the virus by enforcing strict social distancing guidelines, which means businesses across all industries, geographies and sizes are closing their physical spaces. Employees are expected to work, but from their home or as a small team in a micro office. And IT is being asked to provide the secure network connectivity.
There are several ways to do this – via a VPN connection, a virtual office router deployed at home and providing not only connectivity but also security, Wi-Fi, switching and more, or by setting up access points that bridge to the corporate network. Although Cisco has offerings to address all three options – I will discuss the latter two.
Many customers I speak to have old and un-used access points, usually sitting in a warehouse and collecting dust after being replaced by newer generation AP’s. IT can re-purpose these by centrally configuring them to be Office Extend Access Points (OEAP). IT can also temporarily pull, say, every third access point from the office ceiling and use those for home connectivity.
IT can then ship the access points to the employees home, who would connect them to their home network and voila!, within minutes are able to securely log onto the corporate Wi-Fi network, with no need to log-in through VPN every time.
Almost any Cisco Aironet or Catalyst access point can be used, going three generations back to 11n AP’s.
Customers can also leverage the Wireless LAN Controller’s free 60-90 days evaluation license to deploy any wireless LAN controller, virtual or physical, so investment is minimal.
Customers that are looking to manage their network with a central cloud management dashboard can deploy Cisco Meraki’s remote work offers that build on Meraki’s Security & SD-WAN, Teleworker Appliances (MX, Z) and Access Points (MR), which have the capability to securely extend a corporate network into the home. Meraki Insight (MI) gives IT admins a view into the performance of cloud-based applications (WebEx, O365, G-Suite, etc.) and Meraki Systems Manager (SM) keeps school/government/enterprise issued devices secure when those are off the network, and assists in the rapid deployment of security offerings (Duo, Umbrella, Clarity, etc.).
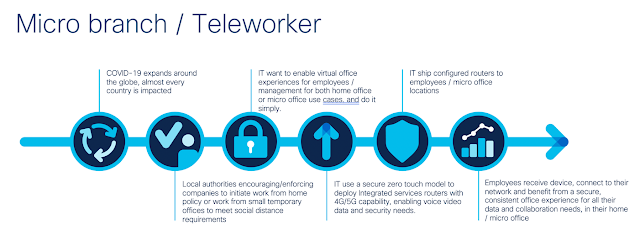
And finally, customers can also set up teleworker, and small branch offices using Cisco ISR 1K devices. For environments where there is no network already present, like in pop-up healthcare facilities, Cisco ISR1K routers offer advanced LTE/cellular options for expanded WAN coverage, backhaul over cellular, backup/fail-over connectivity and active-active configurations.
While this solution might require more time for planning and deployment, it offers the most robust capabilities, is SD-WAN ready and can serve the business future needs beyond the pandemic.
Keeping consumer businesses running
While in many industries work from the workplace is put on hold, there are some consumer- oriented businesses like retail, healthcare, and transportation – where operation is essential.
What can be done to provide shoppers with a safe experience when they go to shop for food? How can airports maintain the health of their travelers and staff? How can hospitals track location of critical devices?
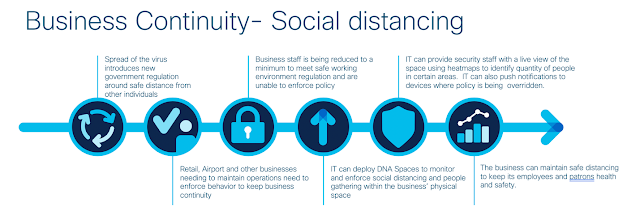
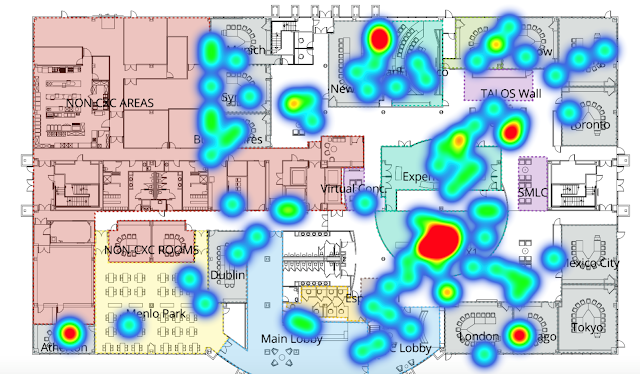
Location based network analytics, enabled by Cisco DNA Spaces, can provide the right insights, and is available to customers for 90 days at no cost. Cisco DNA Spaces, which provides wireless customers with rich location-based services, including location analytics, engagement toolkits and enterprise integrations, enables businesses to use technology in order to solve this physical challenge.
For instance, by leveraging the existing Cisco wireless network at the retailer, IT can provide the security staff access to the Cisco DNA Spaces dashboard so they can monitor the real-time clustering of devices to enforce social distancing at the retailers physical space, by looking at heatmaps overlaid on the business’s floor plan. IT can also push notifications to devices where policy is being overridden.
Another use case focuses on guest engagement. Imagine you go to a pharmacy. You obviously want to spend the least time possible inside the store. Cisco DNA Spaces’ captive portal capability can enable you to check-in when arriving to the pharmacy’s parking lot, and when your turn comes, the business will notify you to come in and conduct your shopping. That way the business can have control over the amount of shoppers on location, reducing health risks.
Other use cases include leveraging Cisco’s partnerships with healthcare solutions providers such as Stanley Healthcare, where the need to track critical assets related to Covid-19 patients, such as respirators or even nurse panic buttons can be enabled by using Cisco DNA Spaces and Stanley Healthcare’s RFID tags.
Supporting temporary healthcare
As many of you have already seen, due to the risks associated with this virus, healthcare providers are deploying temporary facilities such as screening zones, drive-through clinics, as we as full-fledged temporary hospitals, to address the influx of patients, while containing the risk of spread to other patients and staff.
These can be adjacent to the healthcare providers campus where an existing network can extend out, for instance setting up a screening tent in the parking lot of the hospital. Or it can be a mobile field hospital or screening location set up in a nearby location, school or stadium, where there is no available network.
The quickest way to address this challenge is to leverage the existing indoor wireless network, using external directional or omni antennas, to extend to the nearby facility.
Another way is by deploying a wireless mesh solution where one access point is connected to the wired network, and other access points connect to it over Wi-Fi. Almost any AP can operate in this mode and a combination of indoor and outdoor AP’s can be used.
Other options include Mobility Express access points, Meraki access points, point to point bridging or Cellular based wireless backhaul solutions.
The network IS the enabler for business continuity, and the role of IT is immensely important. Although IT companies might not be considered essential businesses per government taxonomy, IT is essential to maintaining business continuity. I’m sure your account team is ready for any ask or question you may have, and I encourage you to reach out for help, as we are all in this together, in solidarity.