With the advent of SaaS and cloud business models, customers expect a shorter time between when they buy something and when they attain value from their purchase. These days, partners can’t sell something, install it, support it, and expect their customers will satisfactorily consume and receive available value from what was bought.
Partners need to enable customers with a customer success strategy that helps ensure they will derive maximum value and ROI from their purchases — but this can be challenging. As an example, newly purchased business-critical technologies can be complex to implement and deploy. As another example, in the absence of usage data, it’s often difficult for customers to know their level of consumption for purchased products, which can make renewal discussions troublesome.
The Cisco Customer Experience (CX) team has an answer, helping Cisco partners transform from a traditional product resell business model to a value-added lifecycle growth model and helping them to help their customers extract the most value from their investments.
To be clear, many Cisco partners have built very successful businesses selling their professional services along with reselling Cisco offerings. That said, although this approach has yielded considerable success in the past, going forward it is not well differentiated, because many partners can essentially replicate this formula. The result is a diluted value proposition, reduced margins, and — quite frankly — a future struggle for survival.
So, to help partners create new sources of value and enable expanded growth, while helping ensure that customers have an optimal experience, Cisco offers the CX Success Portfolio. The Cisco CX Success Portfolio consists of three fundamental elements:
◉ A simplified Cisco portfolio of products and services that makes it easier for buyers to buy and partners to bundle in their own value-add services.
◉ Insights and analytics based on usage and telemetry data generated from the Cisco portfolio, spotlighting customer consumption of the overall product and specific features and enabling ongoing partner-to-customer discussions to help deliver customer satisfaction and identify partner upsell opportunities.
◉ A lifecycle selling framework, which helps guide the selling motion to where there are opportunities to grow revenues.
Previously, Cisco services were sold as product attach during the initial sale and then hopefully again at renewal. The result was a complicated portfolio of product and service offerings not aligned to the customer lifecycle. In the future, the new CX portfolio will have a simplified, agile, and innovative services portfolio with flexible options to meet your customer’s business requirements. We are developing a new suite of solution capabilities comprised of four primary focus areas:
1. Expert Resources
2. Trusted Support
3. Insights and Analytics
4. Contextual Learning
We are evolving our portfolio with new Expert Resources; designed a more tailored approach to hardware and software with Trusted Support; added Insights and Analytics features; and added Contextual Learning to create an optimal experience in every step of your customer’s lifecycle journey. We will offer graduated service levels that build upon each other as they increase — with everything from self-help tools to working beside them to show, guide, and jointly team to deliver the right level of support to meet specific needs or directly execute successful outcomes.
Your customer can choose the right level of support, expert guidance and insights that aligns with their budget, resources and IT environment, to resolve issues quickly and realize value faster at all levels of their lifecycle.
Additionally, this simplified portfolio makes it easier for partners to bundle in their own value-added implementation, deployment and ongoing management services. As an example, a partner can bundle in accelerators, such as one-on-one workshops, which provide deeper education on how to deploy a purchased technology.
In addition, the Cisco portfolio now provides usage and telemetry data, offering partners insights into how much their customers are utilizing the products they’ve purchased. This data becomes a critical tool to help partners engage with customers, ultimately with the goal to increase usage and satisfaction with purchases, which can lead to increased renewals. This data also gives partners a lens into opportunities on how best to position their services en route to upselling additional services.
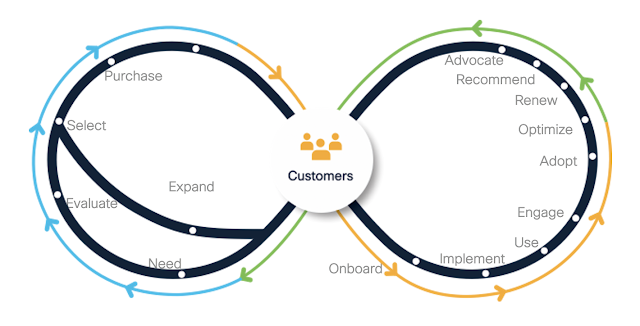
Ultimately, Cisco’s simplified portfolio, along with insights and analytics, provide the foundation for partners to align their services around the Cisco CX Lifecycle framework racetrack, as shown in Figure 1.
Figure 1: The customer lifecycle
Partners need to enable customers with a customer success strategy that helps ensure they will derive maximum value and ROI from their purchases — but this can be challenging. As an example, newly purchased business-critical technologies can be complex to implement and deploy. As another example, in the absence of usage data, it’s often difficult for customers to know their level of consumption for purchased products, which can make renewal discussions troublesome.
The Cisco Customer Experience (CX) team has an answer, helping Cisco partners transform from a traditional product resell business model to a value-added lifecycle growth model and helping them to help their customers extract the most value from their investments.
To be clear, many Cisco partners have built very successful businesses selling their professional services along with reselling Cisco offerings. That said, although this approach has yielded considerable success in the past, going forward it is not well differentiated, because many partners can essentially replicate this formula. The result is a diluted value proposition, reduced margins, and — quite frankly — a future struggle for survival.
So, to help partners create new sources of value and enable expanded growth, while helping ensure that customers have an optimal experience, Cisco offers the CX Success Portfolio. The Cisco CX Success Portfolio consists of three fundamental elements:
◉ A simplified Cisco portfolio of products and services that makes it easier for buyers to buy and partners to bundle in their own value-add services.
◉ Insights and analytics based on usage and telemetry data generated from the Cisco portfolio, spotlighting customer consumption of the overall product and specific features and enabling ongoing partner-to-customer discussions to help deliver customer satisfaction and identify partner upsell opportunities.
◉ A lifecycle selling framework, which helps guide the selling motion to where there are opportunities to grow revenues.
A simplified Cisco portfolio
Previously, Cisco services were sold as product attach during the initial sale and then hopefully again at renewal. The result was a complicated portfolio of product and service offerings not aligned to the customer lifecycle. In the future, the new CX portfolio will have a simplified, agile, and innovative services portfolio with flexible options to meet your customer’s business requirements. We are developing a new suite of solution capabilities comprised of four primary focus areas:
1. Expert Resources
2. Trusted Support
3. Insights and Analytics
4. Contextual Learning
We are evolving our portfolio with new Expert Resources; designed a more tailored approach to hardware and software with Trusted Support; added Insights and Analytics features; and added Contextual Learning to create an optimal experience in every step of your customer’s lifecycle journey. We will offer graduated service levels that build upon each other as they increase — with everything from self-help tools to working beside them to show, guide, and jointly team to deliver the right level of support to meet specific needs or directly execute successful outcomes.
Your customer can choose the right level of support, expert guidance and insights that aligns with their budget, resources and IT environment, to resolve issues quickly and realize value faster at all levels of their lifecycle.
Additionally, this simplified portfolio makes it easier for partners to bundle in their own value-added implementation, deployment and ongoing management services. As an example, a partner can bundle in accelerators, such as one-on-one workshops, which provide deeper education on how to deploy a purchased technology.
Insights and analytics
In addition, the Cisco portfolio now provides usage and telemetry data, offering partners insights into how much their customers are utilizing the products they’ve purchased. This data becomes a critical tool to help partners engage with customers, ultimately with the goal to increase usage and satisfaction with purchases, which can lead to increased renewals. This data also gives partners a lens into opportunities on how best to position their services en route to upselling additional services.
Lifecycle Services Framework
Ultimately, Cisco’s simplified portfolio, along with insights and analytics, provide the foundation for partners to align their services around the Cisco CX Lifecycle framework racetrack, as shown in Figure 1.
Figure 1: The customer lifecycle
Partners can utilize this framework to align capabilities in their organization to deliver enhanced customer experiences in areas such as customer and user onboarding, implementation, adoption, expansion, training, customer success help desks, and traditional technical support. Likewise, partner CX capabilities need to meet customer expectations around regular reviews of product utilization and outcomes delivered, help with renewals and future planning, and provide timely updates on new features and offers.
The breadth and depth of partner lifecycle services, offered in concert with their industry and domain expertise, can create strong differentiators and help fuel future growth in four major areas:
◉ Increase deal sizes at purchase, because partners are better positioned to achieve a higher attach of Cisco CX offers and sell at a higher price point as a part of the bundled offer.
◉ Increase bookings, because more partner value-added services can be sold along with Cisco Simplified Portfolio offers. Partners will have opportunities to better differentiate themselves by offering accelerators for deployment and adoption of technologies.
◉ Increase renewal rates through insights and analytics, facilitating partner investments in their customers’ success as they work with customers around increasing adoption and renewal activities.
◉ Increase upsell pull-through, as partners utilize insights and analytics to identify additional upsell opportunities for Cisco product portfolio.
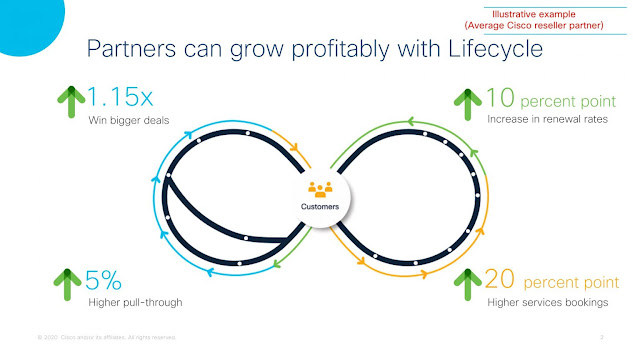
According to Cisco’s own research, by adopting the lifecycle selling framework, as shown in Figure 2, partners on average can expect to see a 1.15X increase in deal size, a 20 percent point increase in partner service pull-through, a 10 percent increase in renewal rates, and a 5 percent higher pull-through. Ultimately, this leads to increased partner revenues.
Figure 2: Partners can grow profitability with the CX lifecycle
How much additional revenue? Ultimately through the Cisco CX Success Portfolio and adopting the lifecycle selling framework, Cisco has discovered that over a five-year period partners on average can see a 2X increase in revenue, as shown in Figure 3.
Figure 3: Increased partner revenue through lifecycle selling
Survive and thrive
Essentially, Cisco CX is here to help partners not only survive by further differentiating their offers from traditional box reselling, but also thrive through increases in revenue over the lifetime of each deal.
In fact, this is the path Cisco took. In the last few years, Cisco has increasingly focused on growing its recurring software business, which has resulted in better visibility into future earnings and higher profitability. Partners can look to Cisco as an example of how they might evolve themselves.