- Exam Name: Designing Cisco Unified Contact Center Enterprise
- Exam Number: 500-440 UCCED
- Exam Price: $300 USD
- Duration: 75 minutes
- Number of Questions: 65-75
- Passing Score: Variable (750-850 / 1000 Approx.)
- Recommended Training:
- Administering Cisco Unified Contact Center Enterprise Part 1 (AUCCE1) 2.0
- Administering Cisco Unified Contact Center Enterprise Part 2 (AUCCE2) 2.0
- Deploying Cisco Unified Contact Center Enterprise (DUCCE) 2.0
- Exam Registration: PEARSON VUE
- Sample Questions: Cisco 500-440 Sample Questions
- Practice Exam: Cisco Unified Contact Center Enterprise Specialist Practice Test
Friday, 18 September 2020
Cisco 500-440 Sample Questions | Syllabus | UCCED Practice Test
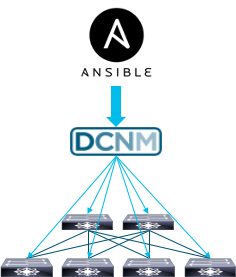
Streamline NX-OS fabric deployments with Cisco DCNM and Red Hat Ansible
Today I will give an overview of our recent integration between Cisco Data Center Network Manager (DCNM) and Red Hat Ansible to streamline NX-OS fabric deployments.
Introduction
Traditionally in data center network management, configuration was often a manual, error prone process, with an operator going device by device to make changes, with every change requiring a deep understanding of both the OS specific CLIs as well as an knowledge of the technology and the implications of each CLI change, to attain a desired outcome.
Cisco DCNM
Cisco DCNM is a turnkey solution for NX-OS network-wide workload orchestration and workflow automation, providing everything from Day 0 auto-provision, through Day N configuration changes. The solution is delivered through an easy to use UI for a single point of management for both network configuration and monitoring.
Additionally, operators have begun to understand and embrace the DevOps model to streamline network management. It is now widely accepted that network automation can be leveraged to accelerate network deployment and optimize network operations in a data center.
With the current global COVID-19 pandemic, network teams are being asked to do more with less, all while working remotely.
The importance of automation was highlighted even further in a recent IDC survey[1].
As part of the responses to the survey,
1. 48% of respondents said they will increase investment in automation solutions to reduce manual management of the network
2. 46% require increased ability to remotely manage network operations
Ansible and Cisco DCNM
Red Hat Ansible is an open-source solution that addresses challenges from network automation and application deployment, to managing a cloud infrastructure, in order to drive a more efficient IT environment with a simplified toolchain.
Ansible has emerged as one of the most popular platforms to automate and simplify network management tasks and boost cost savings and operational efficiency. Ansible works with many different operating systems that run on Cisco Networking platforms including ACI, IOS-XE and IOS-XR.
For several years now, Cisco has offered industry leading Ansible modules for NX-OS, which have been widely adopted and remain extremely popular to automate and streamline network deployments.
However, customers are increasingly looking to move towards a single point of management for their fabrics, rather than making changes at a device by device level.
Ansible, in conjunction with Cisco DCNM, provides a perfect combination for customers to embrace the DevOps model and accelerate NX-OS deployment, monitoring, day-to-day management, and more. Ansible achieves this goal by leveraging the open APIs of DCNM to automate the most common tasks.
Operational efficiencies made possible by Ansible and Cisco DCNM include the following:
◉ Addition or removal of NX-OS switches from a fabric
◉ Management of networks within a VXLAN fabric
◉ Addition or removal of VRFs from a VXLAN fabric
◉ Orchestration of switch interfaces within a DCNM managed fabric
Key Benefits of Cisco DCNM/Ansible solution
Thursday, 17 September 2020
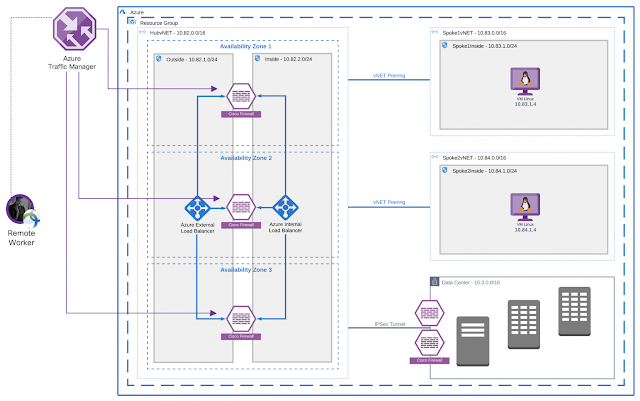
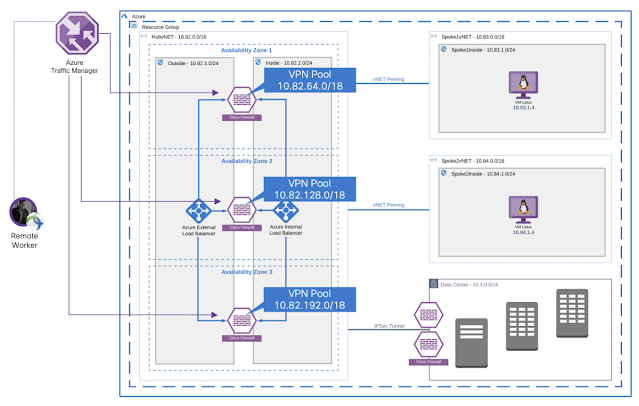
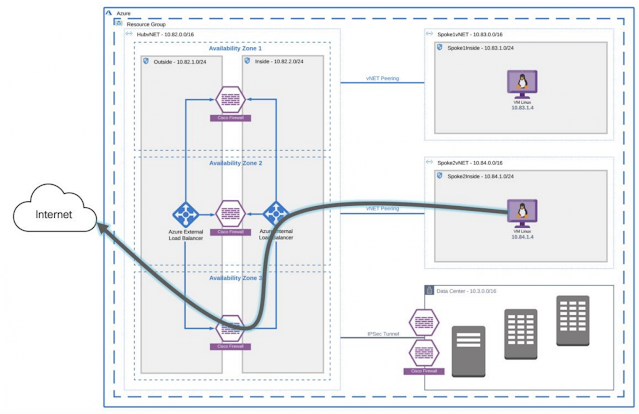
Cisco Secure Remote Worker Architecture for Azure
Today companies are investing in empowering their workforce to have a secure connection to the resources hosted in the Cloud. Cisco provides a secure remote worker solution that uses the Cisco AnyConnect Secure Mobility Client, Cisco Duo, Cisco Umbrella, and Cisco Advanced Malware Protection (AMP) for Endpoints.
◉ Cisco AnyConnect Secure Mobility Client: Cisco AnyConnect Secure Mobility Client empowers remote workers with frictionless, highly secure access to the enterprise network from any device, at any time, in any location while protecting the organization. It provides a consistent user experience across devices, both on and off-premises, without creating a headache for your IT teams. Simplify management with a single agent.
◉ Cisco Duo: Cisco Duo is a user-friendly, scalable way to keep business ahead of ever-changing security threats by implementing the Zero Trust security model. Multi-factor authentication from Duo protects the network by using a second source of validation, like a phone or token, to verify user identity before granting access. Cisco Duo is engineered to provide a simple, streamlined login experience for every remote user. As a cloud-based solution, it integrates easily with your existing technology and provides administrative, visibility, and monitoring.
◉ Cisco Umbrella Roaming Security Module: Cisco Umbrella Roaming Security module for Cisco AnyConnect provides always-on security on any network, anywhere, any time — both on and off your corporate VPN. The Roaming Security module enforces security at the DNS layer to block malware, phishing, and command and control callbacks over any port. Umbrella provides real-time visibility into all internet activity per hostname both on and off your network or VPN.
◉ Cisco Advanced Malware Protection (AMP) Enabler: Cisco AnyConnect AMP Enabler module is used as a medium for deploying Advanced Malware Protection (AMP) for Endpoints. It pushes the AMP for Endpoints software to a subset of endpoints from a server hosted locally within the enterprise and installs AMP services to its existing user base. This approach provides AnyConnect user base administrators with an additional security agent that detects potential malware threats in the network, removes those threats, and protects the enterprise from compromise. It saves bandwidth and time taken to download, requires no changes on the portal side, and can be done without authentication credentials being sent to the endpoint. AnyConnect AMP Enabler protects the user both on and off the network or VPN.
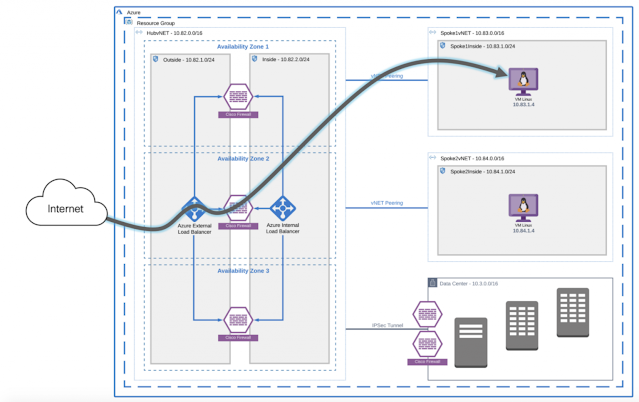
Cisco Secure Remote Worker Architecture for Azure
Traffic Flow
Wednesday, 16 September 2020
Adapting to the New Work Environment through Automation
It’s such an odd time right now. Standing where we are, we know the world and the workforce is changing. While there’s universal consensus that nothing will be the same, no one is sure exactly what the new workforce environment will look like. Sure, there are hints. According to a recent IDC webinar—COVID 19 and Enterprise Networking—Assessing the Impact, Planning for the Future—the number of remote workers will surge from less than 7% to nearly 30%. And networks will need to change to support business continuity in this geographically dispersed workforce with application and collaboration experiences that mirror those in the office.
But what will that look like? VPN? Cloud?
One sure thing is that network automation will play an increasingly important role going forward. The same IDC report bears this out, indicating that, at 48%, the number one area of increased IT investment will be for network automation. Why? Because regardless of how IT pivots to support distributed workers, the infrastructure required to handle that load will be more complex and more demanding. The management task is simply too heavy a lift to perform manually. It must be handled through automation.
This distributed workforce requirement aligns with the core automation capabilities built into Cisco DNA Center. We have always touted the time and cost savings available using Cisco DNA Center automation capabilities. Those benefits still remain. However, the emphasis moving forward will be on business resilience and continuity.
Cisco DNA Center automation works because it uses business intent to define how a network should run. Then it defines policies and configurations to ensure the network operates as intended. Then—and here’s the real power—Cisco DNA Center automatically pushes those polices and configurations throughout the network. Even a geographically distributed network.
There are several aspects of the new workforce environment that require this higher level of automation: deployments, complexity, consistent experience, configuration changes, security, and software maintenance. Let’s take a closer look at each.
Deployments
As enterprises scramble to support work from home, the number of new device deployments—for remote access, security, and routing—has exploded. The number and overnight turnaround makes managing the deployments manually nearly impossible. An IT department with a dozen techs can’t scale up to instantaneously deploy thousands or tens of thousands of remote deployments over one weekend. And, I’ve heard story after story of that’s exactly what Cisco DNA enabled.
Complexity
Complexity is likely to grow as organizations adapt to a more remote workplace. This is because of two factors—distribution and control. First, as workers work from home, the number of points of connection will become more distributed. And, second, the organization has less control over the technology in those home office environments. Sure, you can send virtual office routers, but you won’t have control over the ISP or wiring in the house. This makes access policy more difficult to implement and enforce – and configurations more difficult to establish and manage.
It’s just not realistic to assume that any IT department would have the manual resources to tackle this complexity. That’s where Cisco DNA automation comes in. You can establish different configurations for remote offices, headquarters, even different ISPs, then use Cisco DNA Center to automatically configure all of the necessary devices to support that remote access.
Consistent Experience
One of the things I keep hearing about the shift to working remotely is that employees don’t see their home office as workplace lite. It’s their new office. To deliver the same level of productivity, employees need to have an experience that’s consistent with the one they had in the campus or branch. That means consistent application access and performance, even while working from their new home office.
Sure, some of this consistent experience is dependent on the network devices used in the remote office. But consistent configurations and access policies are even more important. Again, with the number of home office locations exploding, there is no way for an IT department to manually provision all of these offices for optimal experience. And, if they try, the manual effort is guaranteed to introduce configuration errors that diminish the expected application and access experience and create potential security vulnerabilities.
Configuration Changes
While remote workplaces will be a big part of future collaboration, so will change. Employees may more frequently migrate between remote and campus environments. And enterprises may need to continually change configurations, policies and access permissions to accommodate this new demand for flexibility.
Through the configurations templates and automated deployment already discussed, Cisco DNA Center helps you easily make these changes. More importantly, because of the intent-based templates, those changes, regardless of how quickly they need to be deployed, will maintain the same level of consistency and application support as the initial deployment.
Security
With the expanded threat surface created by more remote work environments, security is a huge concern going forward. Vulnerabilities may be introduced into the network during rollout and management through deployment glitches, missed security patches and non-integrated security applications. The automation capabilities of Cisco DNA Center help with all three.
For deployments, the automated nature of the Cisco DNA deployments uses consistent configurations templates and significantly reduces manual errors, thereby greatly minimizing the introduction of security vulnerabilities through incomplete or inaccurate deployments.
Going further, Cisco DNA Center has security integrated into its automation capabilities. First, all applications are under constant attack and require effective security patch management to quickly address vulnerabilities. Cisco security advisories are made available from within Cisco DNA Center. The highest level threats for devices on your network rise to the top of the list where you can directly download and deploy the new patches to all affected devices.
In addition, Cisco DNA Center integrates several Cisco security solutions right into the solution dashboard. Stealthwatch and Umbrella can be deployed directly from within Cisco DNA Center. And rogue and adaptive wireless intrusion prevention is built right into the solution. As a result, security and network management, both in greater demand in this new environment, can be more effectively managed through the automation capabilities of Cisco DNA Center.
Software Maintenance
In the best of times, maintaining current versions of system software for all of your network devices can be a challenge. But when those devices are distributed across thousands or tens of thousands of remote worksites, the challenge is no longer possible with manual updates.
Again, Cisco DNA Center automation capabilities help you overcome this challenge. Cisco DNA Center can actively discover all the system software versions on your network devices, highlight those that are inconsistent or out of compliance, and even push the correct, up-to-date image to the identified network devices. All automatically from your Cisco DNA Center dashboard and regardless of location. In fact, you can even define different configurations by location and keep those up to date as well.
The bottom line is no one really knows the exact shape of the future workforce environment. But Cisco DNA Center automation capabilities all support the agility, flexibility, and remote access that will help you adapt as we all move forward.
Tuesday, 15 September 2020
Managing a safer return to work with Cisco DNA Spaces — An early report
This blog is an update to the initial plans I shared in Helping to keep employees safe by measuring workspace density with Cisco DNA Spaces. As I write this, we’re using Cisco DNA Spaces to monitor workplace density in 20 Cisco offices, including several in Asia Pacific and Europe. Here are our experiences after the first few months, and what’s ahead.
Counts are accurate
Before using Cisco DNA Spaces to monitor workspace density, we needed to confirm that most people in our buildings connect at least one device—phone, tablet, or laptop. In the first offices to open, Seoul and Beijing, we assigned people to count the number of people entering and exiting each floor lobby. The count closely matched the Cisco DNA Spaces count, giving us the confidence to move ahead.
More accurate than the access-control system
What if people are too close?
Beyond density measuring
Lesson learned: check if building maps are accurate
Monday, 14 September 2020
Using the New Cisco SD-WAN SDK
What is a Software Development Kit (SDK)?
Put simply this is a set of tools, libraries, and documentation to simplify interacting with a REST API. The Cisco SD-WAN Python SDK is a Python-based SDK for Cisco vManage. The SDK is intended for anybody interested in automating the configuration and operation of Cisco SD-WAN deployments using Python.
What can you do with the SDK?
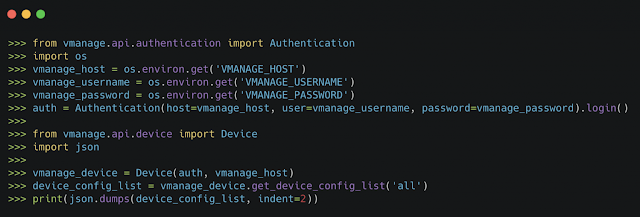
The SDK enables configuration and operations of Cisco vManage via Python-based API bindings. In a traditional SD-WAN deployment, nearly all management of the SD-WAN control plane and overlay of VPNs and edge devices is done via the Cisco vManage GUI. The SDK allows automation of vManage via Python without any GUI interaction. The following examples illustrate some of the benefits of interacting with Cisco vManage programmatically.
◉ Integration with other platforms
◉ Basic management of policy or device/feature templates
◉ Backup/restore
◉ CI/CD
So, let’s get started:
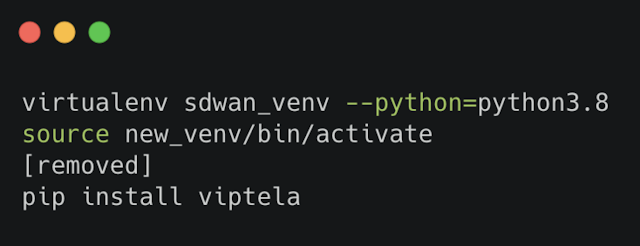
Installing the Cisco SD-WAN SDK
The Cisco SD-WAN SDK is available via PyPI, so all that is required is “pip install”. It is also recommended to use a virtual environment.
Using the Cisco SD-WAN SDK
Saturday, 12 September 2020
Securing Remote and Mobile Workers the Webex Way
New Mobile Security and Granular Controls
Mobile Webex IT Administrators have been clamoring for more granular policy enforcement tools and also more integrations with their existing tool sets. To solve for both of these, Webex now has integration with Microsoft Intune Mobile Application management, including:
◉ Passcode/Touch ID
◉ Document sharing
◉ Preventing application backup
◉ Disabling screen capture
◉ Enforcing Application Encryption
◉ Disabling Copy and Paste
◉ Remote Application Wipe
And for those customers who aren’t using Intune, Webex allows them to secure the Webex mobile apps by self-wrapping it with their preferred Mobile Application Management solution SDK by providing app binaries.
In addition, Webex now supports AppConfig – the industry standard for Mobile Application Management. Customers can deploy several policies like disable copy and paste across virtually any MDM solution.
Finally, Webex is continuing to augment native Control Hub Mobile Application Management controls and just released a capability to block message notifications on mobile screens to prevent against data loss on unattended devices.