Part 1: Critical severity threats and MITRE ATT&CK tactics
In the ongoing battle to defend your organization, deciding where to dedicate resources is vital. To do so efficiently, you need to have a solid understanding of your local network topology, cloud implementations, software and hardware assets, and the security policies in place. On top of that, you need to have an understanding of what’s traveling through and residing in your environment, and how to respond when something is found that shouldn’t be there.
This is why threat intelligence is so vital. Not only can threat intelligence help to defend what you have, it can tell you where you’re potentially vulnerable, as well as where you’ve been attacked in the past. It can ultimately help inform where to dedicate your security resources.
What threat intelligence can’t tell you is exactly where you’ll be attacked next. The fact is that there’s no perfect way to predict an attacker’s next move. The closest you can come is knowing what’s happening out in the larger threat landscape—how attackers are targeting organizations across the board. From there it’s possible to make those critical, informed decisions based on the data at hand.
This is the purpose of this new blog series, Threat Landscape Trends. In it, we’ll be taking a look at activity in the threat landscape and sharing the latest trends we see. By doing so, we hope to shed light on areas where you can quickly have an impact defending your assets, especially if dealing with limited security resources.
To do this, we’ll dive into various Cisco Security technologies that monitor, alert, and block suspected malicious activity. Each release will focus on a different product, given the unique view of activity each can provide, informing you on different aspects of the threat landscape.
Beginning at the endpoint
To kick off the series, we’ll begin with Cisco’s Endpoint Security solution. Over the course of two blog posts we’ll examine what sort of activity we’ve seen on the endpoint in the first half of 2020. In the first, we’ll look at critical severity threats and the MITRE ATT&CK framework. In part two, to be published in the coming weeks, we’ll dive deeper into the data, providing more technical detail on threat types and the tools used by attackers.
To protect an endpoint, Cisco’s Endpoint Security solution leverages a protection lattice comprised of several technologies that work together. We’ll drill down into telemetry from one of these technologies here: the Cloud Indication of Compromise (IoC) feature, which can detect suspicious behaviors observed on endpoints and look for patterns related to malicious activity.
In terms of methodology for the analysis that follows, the data is similar to alerts you would see within the dashboard of Cisco’s Endpoint Security solution, only aggregated across organizations to get the percentage of organizations that have encountered particular IoCs as a baseline. The data set covers the first half of 2020, from January 1st through June 30th. We’ll cover this in more detail in the Methodology section at the end of this post, but for now, let’s dive into the data.
Threat severity
When using Cisco’s Endpoint Security solution, one of the first things you’ll notice in the dashboards is that alerts are sorted into four threat severity categories: low, medium, high, and critical. Here is a breakdown of these severity categories in terms of the frequency that organizations encountered IoC alerts:
Percentage of low, medium, high, and critical severity IoCs
As you might expect, the vast majority of alerts fall into the low and medium categories. There’s a wide variety of IoCs within these severities. How serious a threat the activity leading to these alerts pose depends on a number of factors, which we’ll look at more broadly in part two of this blog series.
For now, let’s start with the most serious IoCs that Cisco’s Endpoint Security solution will alert on: the critical severity IoCs. While these make up a small portion of the overall IoC alerts, they’re arguably the most destructive, requiring immediate attention if seen.
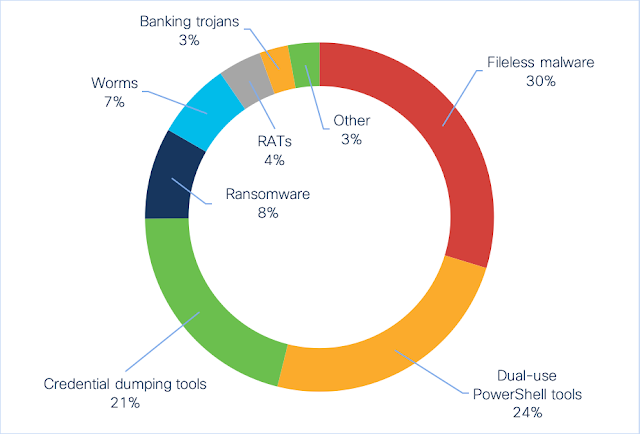
Critical severity IoCs
Sorting the critical IoCs into similar groups, the most common threat category seen was fileless malware. These IoCs indicate the presence of fileless threats—malicious code that runs in memory after initial infection, rather than through files stored on the hard drive. Here, Cisco’s Endpoint Security solution detects activity such as suspicious process injections and registry activity. Some threats often seen here include Kovter, Poweliks, Divergent, and LemonDuck.
Coming in second are dual-use tools leveraged for both exploitation and post-exploitation tasks. PowerShell Empire, CobaltStrike, Powersploit, and Metasploit are four such tools currently seen here. While these tools can very well be used for non-malicious activity, such as penetration testing, bad actors frequently utilize them. If you receive such an alert, and do not have any such active cybersecurity exercises in play, an immediate investigation is in order.
The third–most frequently seen IoC group is another category of dual-used tools. Credential dumping is the process used by malicious actors to scrape login credentials from a compromised computer. The most commonly seen of these tools in the first half of 2020 is Mimikatz, which Cisco’s Endpoint Security solution caught dumping credentials from memory.
All told, these first three categories comprise 75 percent of the critical severity IoCs seen. The remaining 25 percent contains a mix of behaviors known to be carried out by well-known threat types:
- Ransomware threats like Ryuk, Maze, BitPaymer, and others
- Worms such as Ramnit and Qakbot
- Remote access trojans like Corebot and Glupteba
- Banking trojans like Cridex, Dyre, Astaroth, and Azorult
- …and finally, a mix of downloaders, wipers, and rootkits
MITRE ATT&CK tactics
Another way to look at the IoC data is by using the tactic categories laid out in the MITRE ATT&CK framework. Within Cisco’s Endpoint Security solution, each IoC includes information about the MITRE ATT&CK tactics employed. These tactics can provide context on the objectives of different parts of an attack, such as moving laterally through a network or exfiltrating confidential information.
Multiple tactics can also apply to a single IoC. For example, an IoC that covers a dual-use tool such as PowerShell Empire covers three tactics:
- Defense Evasion: It can hide its activities from being detected.
- Execution: It can run further modules to carry out malicious tasks.
- Credential Access: It can load modules that steal credentials.
With this overlap in mind, let’s look at each tactic as a percentage of all IoCs seen:

IoCs grouped by MITRE ATT&CK tactics
By far the most common tactic, Defensive Evasion appears in 57 percent of IoC alerts seen. This isn’t surprising, as actively attempting to avoid detection is a key component of most modern attacks.
Execution also appears frequently, at 41 percent, as bad actors often launch further malicious code during multi-stage attacks. For example, an attacker that has established persistence using a dual-use tool may follow up by downloading and executing a credential dumping tool or ransomware on the compromised computer.
Two tactics commonly used to gain a foothold, Initial Access and Persistence, come in third and fourth, showing up 11 and 12 percent of the time, respectively. Communication through Command and Control rounds out the top 5 tactics, appearing in 10 percent of the IoCs seen.
Critical tactics
While this paints an interesting picture of the threat landscape, things become even more interesting when combining MITRE ATT&CK tactics with IoCs of a critical severity.
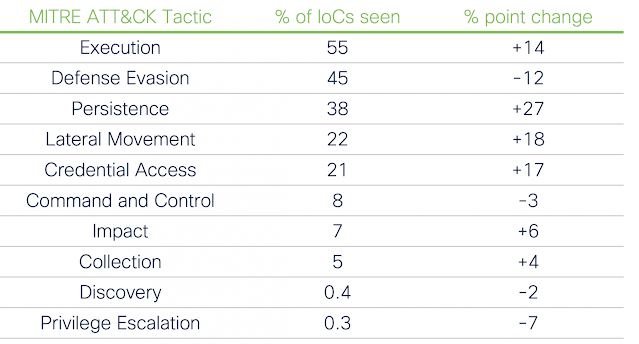
Critical severity IoCs grouped by MITRE ATT&CK tactics
For starters, two of the tactics were not seen in the critical severity IoCs at all, and two more registered less than one percent. This effectively removes a third of the tactics from focus.
What’s also interesting is how the frequency has been shuffled around. The top three remains the same, but Execution is more common amongst critical severity IoCs than Defense Evasion. Other significant moves when filtering by critical severity include:
- Persistence appears in 38 percent of critical IoCs, as opposed to 12 percent of IoCs overall.
- Lateral Movement jumps from 4 percent of IoCs seen to 22 percent.
- Credential Access moves up three spots, increasing from 4 percent to 21 percent.
- The Impact and Collections tactics both see modest increases.
- Privilege Escalation plummets from 8 percent to 0.3 percent.
- Initial Access drops off the list entirely, previously appearing fourth.
Defending against the critical
This wraps up our high-level rundown of the IoC data. So armed with this information about the common threat categories and tactics, what can you do to defend your endpoints? Here are a few suggestions about things to look at:
Limit execution of unknown files
If malicious files can’t be executed, they can’t carry out malicious activity. Use group policies and/or “allow lists” for applications that are permitted to run on endpoints in your environment. That’s not to say that every control available should be leveraged in order to completely lock an endpoint down—limiting end-user permissions too severely can create entirely different usability problems.
If your organization utilizes dual-use tools for activities like remote management, do severely limit the number of accounts that are permitted to run the tools, only granting temporary access when the tools are needed.
Monitor processes and the registry
Registry modification and process injection are two primary techniques used by fileless malware to hide its activity. Monitoring the registry for unusual changes and looking for strange process injection attempts will go a long way towards preventing such threats from gaining a foothold.
Monitor connections between endpoints
Keep an eye on the connections between different endpoints, as well as connections to servers within the environment. Investigate if two machines are connecting that shouldn’t, or an endpoint is talking to a server in a way that it doesn’t normally. This could be a sign that bad actors are attempting to move laterally across a network.