After 2020’s twists and turns, here’s hoping that 2021 ushers in a restored sense of “normal.” In thinking about what the upcoming year might bring for industrial IoT, three key trends emerge.
Trend #1: Securing operational technology (OT)
IT will take a bolder posture to secure OT environments.
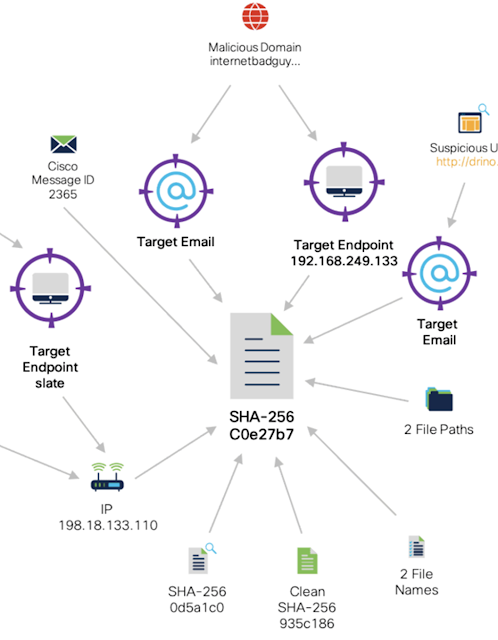
Cyber risks in industrial environments will continue to grow causing IT to take bolder steps to secure the OT network in 2021. The CISO and IT teams have accountability for cybersecurity across the enterprise. But often they do not have visibility into the OT network. Many OT networks use traditional measures like air gapping or an industrial demilitarized zone to protect against attacks. But these solutions are rife with backdoors. For example, third-party technicians and other vendors often have remote access to update systems, machines and devices. With increasing pressure from board members and government regulators to manage IoT/OT security risks, and to protect the business itself, the CISO and IT will need to do more.
Success requires OT’s help. IT cybersecurity practices that work in the enterprise are not always appropriate for industrial environments. What’s more, IT doesn’t have the expertise or insight into operational and process control technology. A simple patch could bring down production (and revenues).
Bottom line? Organizations will need solutions that strengthen cybersecurity while meeting IT and OT needs. For IT, that means visibility and control across their own environment to the OT network. For OT, it means security solutions that allow them respond to anomalies while keeping production humming.
Trend #2: Remote and autonomous operations
The need for operational resiliency will accelerate the deployment of remote and autonomous operations – driving a new class of networking.
The impact of changes brought on in 2020 is driving organizations to increasingly use IoT technologies for operational resiliency. After all, IoT helps keep a business up and running when people cannot be on the ground. It also helps improve safety and efficiencies by preventing unnecessary site visits and reducing employee movement throughout facilities.
In 2021, we will see more deployments aimed at sophisticated remote operations. These will go well beyond remote monitoring. They will include autonomous operational controls for select parts of a process and will be remotely enabled for other parts. Also, deployments will increasingly move toward full autonomy, eliminating the need for humans to be present locally or remotely. And more and more, AI will used for dynamic optimization and self-healing, in use cases such as:
◉ autonomous guided vehicles for picking and packing, material handling, and autonomous container applications across manufacturing, warehouses and ports
◉ increased automation of the distribution grid
◉ autonomous haul trucks for mining applications
◉ Computer-based train control for rail and mass transit
All these use cases require data instantly and in mass, demanding a network that can support that data plus deliver the speed required for analysis. This new class of industrial networking must provide the ability to handle more network bandwidth, offer zero latency data and support edge compute. It also needs security and scale to adapt quickly, ensuring the business is up and running – no matter what.
Trend #3: Managing multiple access technologies
Organizations will operate multiple-access technologies to achieve operational agility and flexibility.
While Ethernet has always been the foundation for connectivity in industrial IoT spaces, that connectivity is quickly expanding to wireless. Wireless helps reduce the pain of physical cabling and provides the flexibility and agility to upgrade, deploy and reconfigure the network with less operational downtime. Newer wireless technologies like Wi-Fi 6 and 5G also power use cases not possible in the past (or possible only with wired connectivity).As organizations expand their IoT deployments, the need to manage multiple access technologies will grow. Successful deployments will require the right connectivity for the use case, otherwise, costs, complexity and security risks increase. With wireless choices including Wi-Fi, LoRaWAN, Wi-SUN, public or private cellular, Bluetooth and more, organizations will need to determine the best technology for each use case.
Cisco’s recommendation: Build an access strategy to optimize costs and resources while ensuring security. Interactions between access technologies should deliver a secured and automated end-to-end IP infrastructure – and must avoid a “mishmash” leading to complexity and failed objectives.