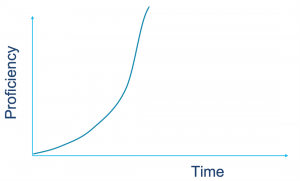
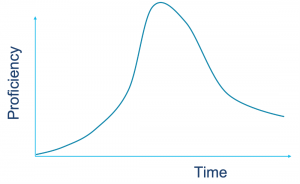
We’ve all heard about the learning curve – showing the relationship between time spent studying material and proficiency.
DevNet Automation Bootcamps help your team focus, learn, and retain
The same factors that make it easier to learn new ideas, also help combat the forgetting curve. The newly launched DevNet Automation Bootcamp is based on recent andragogy research about not just how adults learn, but how to help them retain their knowledge.
The goal of a bootcamp is to maximize your team’s ability to leave with the knowledge, skills, and confidence to implement what you’ve learned.
Automation Bootcamps flatten the forgetting curve by providing an immersive training experience where we:
1. Focus on what you are most motivated to learn – the ideal customer for the Bootcamp has a goal, a big change, for example an implementation, taking over work from a vendor, building a new team, or implementing a new technology. The students generally need the skills, and they need them soon. They know that they will be using what they learn within the next few months. They are motivated.
2. Provide just the training you need and remove training you don’t – Every lecture and lab is relevant – the Cisco team starts by interviewing the customer and learning exactly what they need to know to succeed, and creating a tailored outline – focusing on the areas the customer needs and taking out any training they don’t need. This maximizes classroom time as all topics are identified as important for the success of their project.
3. Deliver training based on technical learning research and styles – the bootcamp brings together the best of instructor led training and self-paced training in a robust format that maximizes student learning and retention.
4. Reduce complexity – the mix of tailored content, multi-modal learning, repetition, and bootcamp style labs helps students internalize complex topics and take the learning back to their home environments and succeed.
5. Repeat concepts at different levels to lock in knowledge and build confidence – The training is broken up into three portions, and each portion reiterates and deepens the core knowledge of the topics:
◉ 5-days of instructor led training –This is foundational training focusing on the concepts, paradigms, and a deep introduction to the core concepts reinforced with over 40% labs
◉ 2-3 weeks of self-paced training with regular instructor led review sessions, leveraging the “flipped classroom” model and using repetition to settle the learning into the retention parts of the brain
◉ 4-days of hands-on deep dive lab where the students are taking their knowledge and applying it in hands on labs and building end-to-end solutions and/or troubleshooting real issues
In the 5-Day instructor-led training, you’ll work with Cisco experts to identify topics specific to your situation. In the 4-day deep dive lab, you’ll extend the skills you gained in the 5-day class
Examples of Automation Bootcamps Topics
ACI Troubleshooting and Operations Immersion Bootcamp
◉ 5-Day Instructor-led training – May include an introduction to ACI (fabric infrastructure, configuration) and ACI Operations (configuration management, monitoring, and troubleshooting)
◉ 4-day Deep Dive Lab – May include building an ACI fabric and troubleshoot issues and then explore ACI Multisite, ACI Multipod, hypervisor integration, complex ACI configuration problems.
ACI Automation Bootcamp
◉ 5-Day Instructor-led training – May include an introduction to automation (Python, APIs, and more) and then dive into ACI automation with Python, SDKs, tools, and more.
◉ 4-day Deep Dive Lab – May include exploring automation actions, tools, toolkits, SDKs and doing deep labs on ACI REST API interface, ACI API Inspector, ACIToolkit, Ansible, pyATS, and CI/CD pipelines using GitLab-CI.
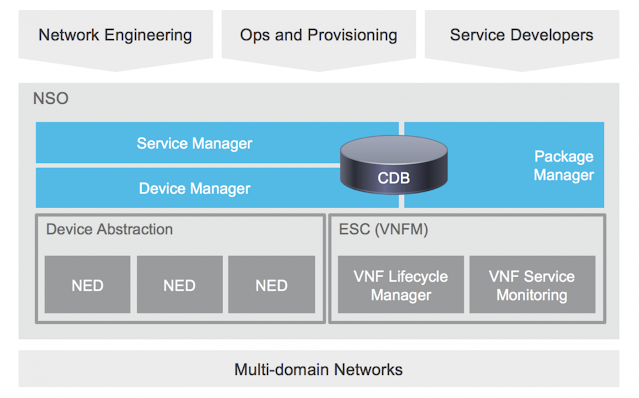
NSO Automation Bootcamp
◉ 5-Day Instructor-led training – May include intro to NSO (components, use cases, installation, NETCONF/YANG, manage devices) NSO services, administration, and DevOps.
◉ 4-day Deep Dive Lab – May include exploring introductory techniques such as installation, the network CLI and config database, and more. Or choose to practice advanced topics such as Python-powered services, advanced YANG constructs, northbound integratiosn, and more.
NX-OS Automation Bootcamp
◉ 5-Day Instructor-led training – May include an intro to automation (Python, APIs, and more) and exploration of NX-OS automation (day-zero provisioning, on-box / off-box programmability, and telemetry).
◉ 4-day Deep Dive Lab – May include performing complete automation actions and learning the roles of tools, toolkits, and SDKs. You will build gain immersive experience with technologies such as NX-API CLI and NX-API REST, model-driven programmability, GuestShell, Ansible, NX-SDK, pyATS, CML, and CI/CD pipelines using GitLab-CI.
Meraki Automation Bootcamp
◉ 5-Day Instructor-led training – May include intro to automation (Python, APIs, and more) and Meraki automation (workflows, APIs, and more)
◉ 4-day Deep Dive Lab – May include exploring Meraki Dashboard and REST, Meraki action batches, and troubleshoot common Meraki issues, or focus on automation provisioning and configuration.
SDA Product Immersion Bootcamp
◉ SDA 5-Day Instructor-led training – May include an introduction to SDA (Cisco SDA fundamentals, provisioning, policies, wireless integration, and border operations) and SDA operations (operating, managing, and integrating Cisco DNA Center, and understanding programmable network infrastructure)
◉ SDA 4-day Deep Dive Lab – May include performing complete SDA implementation tasks. You will build an SD-Access fabric network and nodes and then solve common issues using troubleshooting use cases.